How to Configure Network Access Account in SCCM ConfigMgr
In this post, I will show you how to configure network access account in SCCM, and I’ll describe what a network access account (NAA) is and why ConfigMgr requires one.
As a requirement for OSD, you will be prompted to create a network access account while installing Configuration Manager for your company. Are you aware of the need to create an NAA account and the appropriate permissions for a network access account? By the end of this guide, you’ll have a good understanding of the NAA account and its use. It provides an introduction to the fundamentals of network access accounts for novices.
You might have encountered the most common SCCM OSD error, “Task Sequence Failed with the Error Code 0x80070002“. This is a generic error that typically occurs during the “Applying Operating System” step of the task sequence. If you don’t set up the network access account, your task sequence will stop with the error code 0x80070002.
When client computers can’t access the content on distribution points using their local computer account, Configuration Manager instructs them to utilize the network access account instead. The network access account is primarily utilized during the installation of the operating system.
What is Network Access Account (NAA)?
In SCCM, client computers use the network access account when they can’t use their local computer account to access content on distribution points. Furthermore, the network access account is used during OS deployment.
According to Microsoft, when client computers can’t access content on distribution points using their local computer account, they use the network access account. Workgroup clients and machines from untrusted domains are primarily affected. When the machine installing the OS doesn’t yet have a computer account on the domain, the NAA account is also used during OS deployment.
Note: The network access account is never used as the security context to run programs, install software updates, or run task sequences. It’s used only for accessing resources on the network.
If you configure the SCCM site for HTTPS or Enhanced HTTP, a workgroup or Azure AD-joined client can securely access content from distribution points without the need for a network access account. This behavior includes OS deployment scenarios with a task sequence running from boot media, PXE, or Software Center.
Network Access Account Usage in Configuration Manager
If you are wondering where else does configuration manager utilize network access accounts, here are some answers:
- Multicast Deployment: During the deployment of Windows over the network with Configuration Manager.
- Task Sequence Deployment: During the task sequence deployment, the NAA is used when the option to Access content directly from a distribution point when needed by the running task sequence is enabled.
- Request State Store task sequence step: If the task sequence can’t communicate with the state migration point using the device’s computer account, it falls back to use the network access account.
- Apply OS Image: The apply OS Image task sequence step option to Access content directly from the distribution point. This option is primarily for Windows Embedded scenarios with low disk space where caching content to the local disk is costly.
- Task Sequence properties setting to Run another program first: This setting runs a package and program from a network share before the task sequence starts.
- Managing clients in untrusted domains and cross-forest scenarios allow multiple network access accounts.
Permissions for the Network Access Account
Before you create a network access account in Configuration Manager, let’s understand what permissions do NAA accounts require.
- As per Microsoft, you must grant the NAA account the minimum appropriate permissions on the content that the client requires to access the software. The account must have the “Access this computer from the network” on the distribution point. You can configure up to 10 network access accounts per site.
- You should not grant interactive sign-in rights to this account. In other words, don’t grant this account the right to join computers to the domain. If you must join computers to the domain during a task sequence, use the Task sequence domain join account.
- The network access account must always include a domain name. Pass-through security isn’t supported for this account. If you have distribution points in multiple domains, create the account in a trusted domain.
- Don’t alter the password for an active network access account to prevent account lockouts. Create a new account instead, then configure it in Configuration Manager. Remove the old account from the network shared folders and delete the account once enough time has passed for all clients to receive the new account data.
Configure Network Access Account in SCCM
Use the below steps to set the network access account in SCCM (ConfigMgr):
- In the Configuration Manager console, go to Administration > Overview > Site Configuration > Sites.
- Select your SCCM site. On the Settings group of the ribbon, select Configure Site Components. Choose Software Distribution.
- Click the Network Access Account tab. Set up one or more NAA accounts, and then select OK.
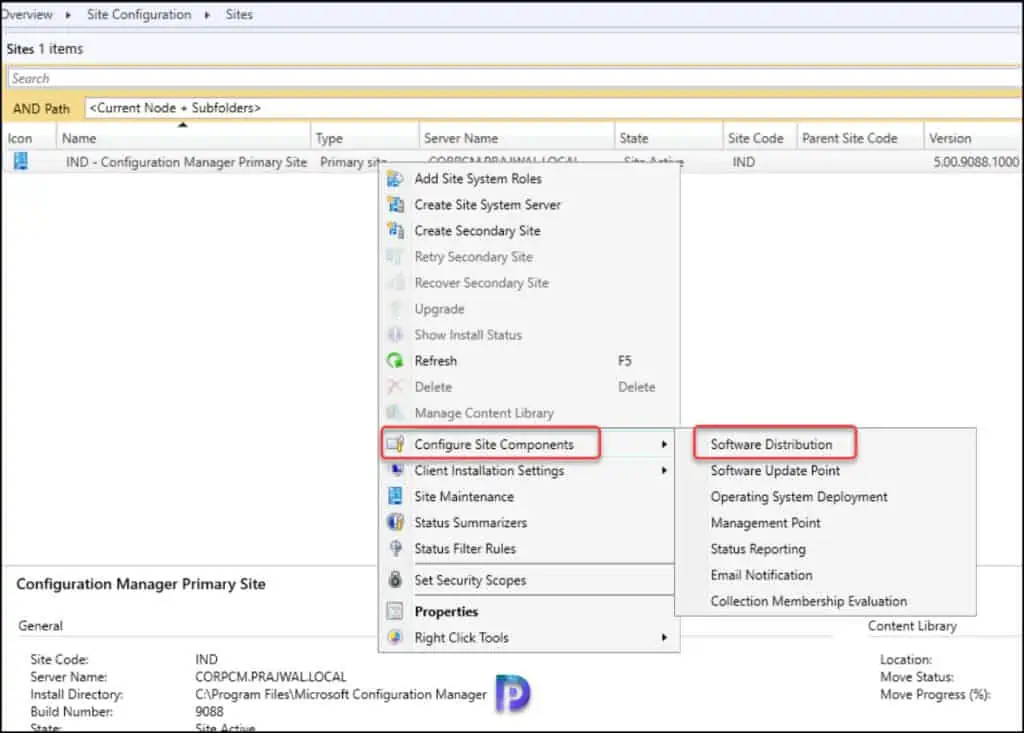
On the Software Distribution Component properties window, switch to Network Access Account tab. Here you’ll find two options:
- Use the computer account of the Configuration Manager client
- Specify the account that accesses network locations
From the above list of options, select Specify the account that accesses network location. To add a new Network Access Account, click on the Yellow star icon and select New Account.
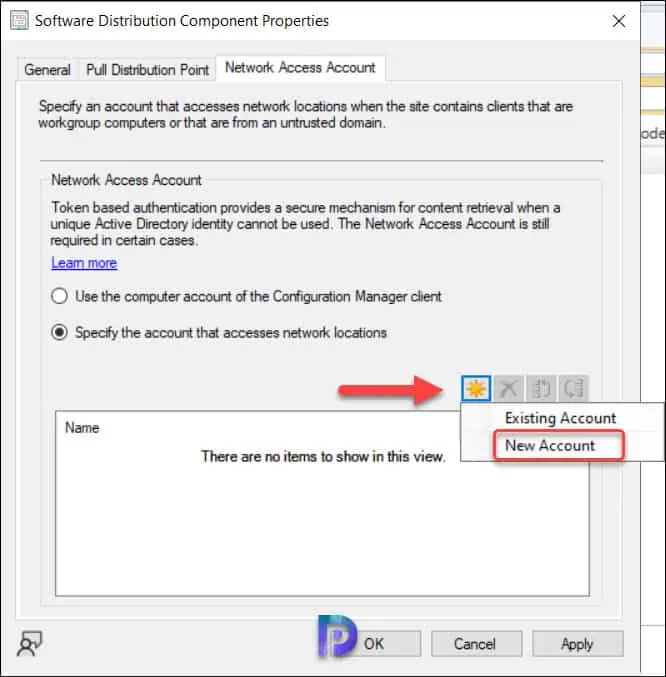
On the Windows User Account box, enter the user name. To add the user from Active Directory, click Browse and select the user account. Enter the password twice and click OK. To validate the network access account, click on Verify and you will be asked to enter a network share. Enter a network share and click on Test Connection. If the connection succeeds it means the network access account details that you have specified are correct.
Click Apply and OK to save the changes.
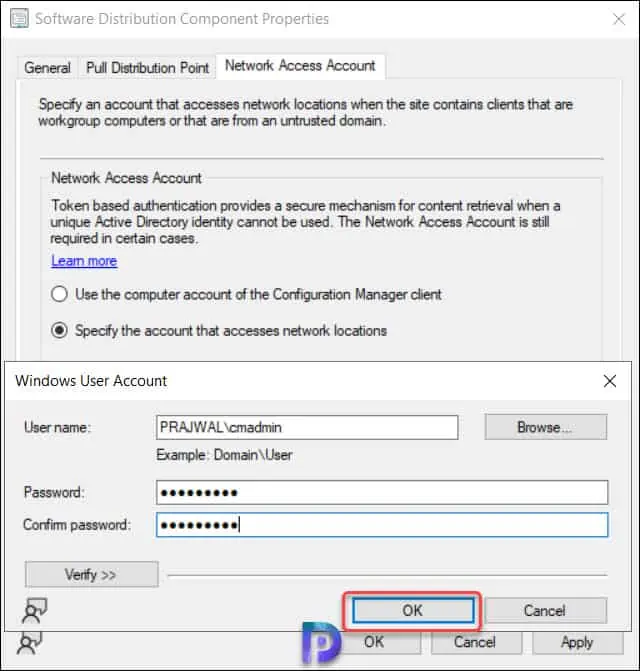
On the Network Access Account tab of Software Distribution Component properties window, you can see all the NAA accounts. You can add or specify more than one network access accounts in SCCM. Microsoft allows configuring up to 10 network access accounts per site.
Setting up Network Access Account in ConfigMgr: Video Tutorial
Watch the below YouTube video tutorial that will guide you through the steps to set up the network access account in Configuration Manager. Any subs to my YouTube channel would be most appreciated.

I saw the same message. If there a way to see if they are being used in the logs?
Good day. Sorry, tell me what to do to update to version 2211. I get the message:
[Completed with warning]: The site server configured with HTTPS/Enhanced HTTP, does not require a network access account. Please verify the minimum appropriate permission of this account(s) and remove the account(s) which has higher privileges. We recommend you remove the configured network access account(s) which are not leveraged. For more information about your network access account required permissions.
Do I need to delete the network account? but then how will the above described in the article work?
Thanks in advance!
That’s a warning, since you have defined the network access account(s), you can remove them if they aren’t being used. Otherwise, please ignore it as it’s just the warning, you can proceed with the upgrade.