Enable Site System Roles for HTTPS or Enhanced HTTP
During SCCM 2103 prerequisite check you encounter Enable site system roles for HTTPS or Enhanced HTTP warning. In this post I will cover how to fix this warning.
When you install or update to SCCM 2103, there are several new warning prerequisite checks added. One among them is Enable site system roles for HTTPS or Enhanced HTTP. The other one is if you have a secondary site that uses SQL Server Express edition, this check warns if the version is earlier than SQL Server 2016 with service pack 2 (13.0.5026.0).
Most of us are going to encounter the same warning during SCCM 2103 prerequisite check. Although this is a warning and will not halt your SCCM 2103 upgrade but it is important that you fix this warning. First let us understand why this warning comes up and how to fix the warning.
If you haven’t performed SCCM 2103 upgrade, here is the upgrade guide – https://www.prajwaldesai.com/sccm-2103-upgrade-guide/.
Enable site system roles for HTTPS or Enhanced HTTP
So why do we get Enable site system roles for HTTPS or Enhanced HTTP warning during SCCM 2103 prerequisite check ?. The answer is if your site is configured to allow HTTP communication without enhanced HTTP, you’ll see this warning. To improve the security of client communications, in SCCM 2103 will require HTTPS communication or enhanced HTTP. You must plan to configure the site for HTTPS only or to use Configuration Manager-generated certificates for HTTP site systems.
Here is a screenshot of what you would see during the SCCM 2103 prerequisite check. The prerequisite check passed with warnings.
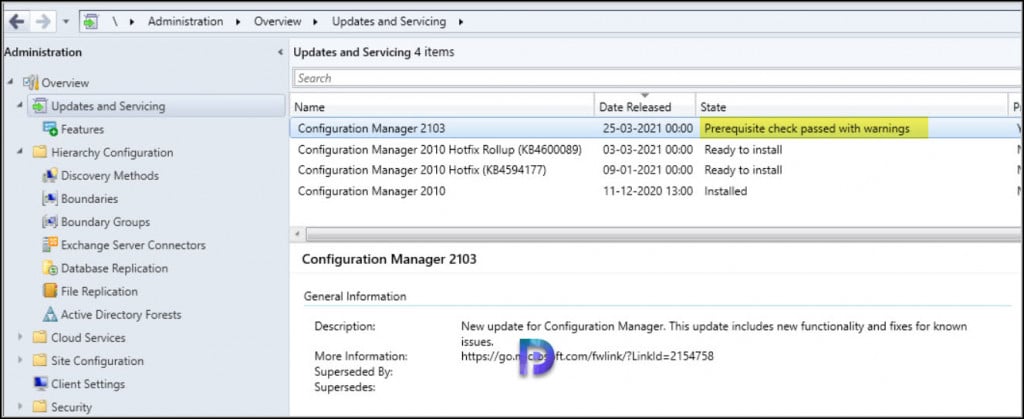
If you review the ConfigMgrPrereq.log file located on root drive of site server, the entire warning is visible.
[Completed with warning] Description: HTTPS or Enhanced HTTP are not enabled for client communication. HTTP-only communication is deprecated and support will be removed in a future version of Configuration Manager. Enable a more secure communication method for the site either by enabling HTTPS or Enhanced HTTP.
Fix SCCM 2103 Prerequisite Check Warning – Enable site system roles for HTTPS or Enhanced HTTP
So how do I fix Enable site system roles for HTTPS or Enhanced HTTP warning ?. The answer is already answered in the SCCM 2103 prerequisite check warning.
- HTTPS or Enhanced HTTP are not enabled for client communication – When I viewed the Communication Security tab of my site properties, the communication method was set to HTTPS or HTTP. Microsoft either wants you to select HTTPS only or Enhanced HTTP.
- HTTP-only communication is deprecated and support will be removed in a future version of Configuration Manager – This is a change introduced in SCCM 2103 and going forward this will apply to all the Configuration Manager current branch releases.
- Enable a more secure communication method for the site either by enabling HTTPS or Enhanced HTTP – To fix this warning, select HTTPS only or enhanced HTTP. If you have PKI certificates for SCCM, select HTTPS only. Other wise select Use Configuration Manager generated certificates for HTTP site systems.
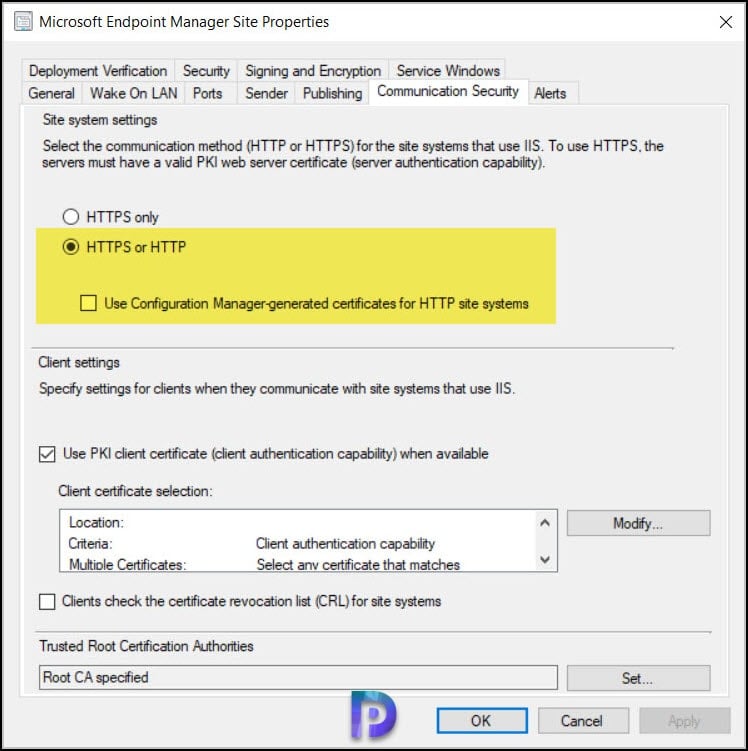
I am going to select HTTPS only option here as I have the PKI certificates implemented in my setup. When I do that Use PKI client certificate when available option is greyed out.
Note – You still got an option to switch to enhanced HTTP mode whenever you require to do so.
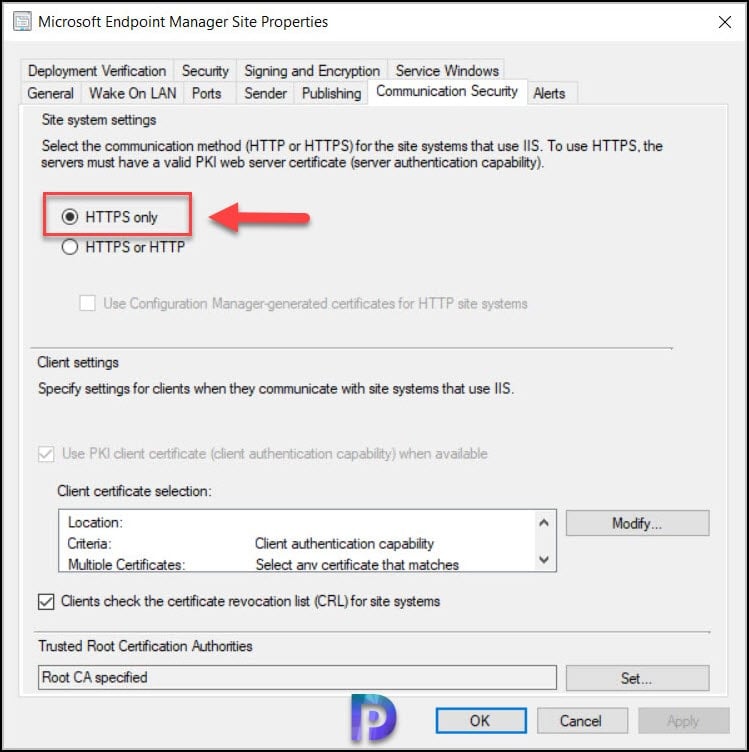
After you make the above changes, run the SCCM 2103 prerequisite check again and the warning Enable site system roles for HTTPS or Enhanced HTTP should not appear. If you have got SCCM secondary sites, you don’t need to make any changes on them. It’s just the top level site that you need to make the changes.

Hi,
I am also having PxE issues, when I enabled the Enhanced HTTP we could not get PXE boot, the device would get an IP and then reboot with a failed boot message, I remove the Enhanced HTTP and it works again.
Please let me know which logs would be useful in troubleshooting this issue.
Before you disabled the enhanced HTTP did you examine the PXE boot log files ?.
You’re the man! Thanks as always.
Hi Prajwal,
I was wondering if you can please point me to the right directions. In our Primary Site i’ve changed from Https or http to https Only and clicked on ‘Apply’…..We now can’t image any PCs. We are stuck on ‘Start PXE over IPv4. Also, all of our devices in SCCM are showing ‘offline’ plus none of the applications in software center are visible.
-I’ve changed the setting back to HTTP Only – But still the same result
-Reboot the Primary Server and Site System Server – No change
-Check IIS – But not sure what certificates are missing in Bindings.
Any help is much appreciated.
Thanks,
Daniel
Hi, I am also having the same issue. After navigating to Administration > Site Configuration > Sites > Properties of site > Communication Security I ticked the box that says ‘Use Configuration Manager -generated certificates for HTTP site systems.
After ticking this box I am no longer able to PXE boot devices. The clients don’t receive a PXE response.
Okay, I have questions! Obviously a full PKI implementation is preferred but I don’t have the time to get that setup SO what happens with enhanced HTTP? Do I have to create) deploy certificates or is that automatically handled? What about existing clients? What about OSD to be machines? I don’t have a lab environment to test this stuff, I’m a longer admin doing everything in a medium-sized school..
Sorry, lots of typos above, I’ll try again..
“Okay, I have questions! Obviously a full PKI implementation is preferred but I don’t have the time to get that setup SO what happens with enhanced HTTP? Do I have to create/deploy certificates or is that automatically handled? What about existing clients? What about OSD to new machines? I don’t have a lab environment to test this stuff, I’m a lone admin doing everything in a medium-sized school..”
I’d like to know as well.
You don’t need to worry about the certificates. The OSD and client agents will be unaffected with this change.
Thanks Prajwal.
For clarity – We can enable the option on our Primary Site and select :
Use Configuration Manager-generated certificates for HTTP site systems
and this option will handle all client communication requirements, for OSD, for App deployment and for management, etc.
Is there any further action required for sites that do NOT have HTTPS or PKI setup?
Thanks ever so much Man, Love your site!!!
If you haven’t implemented PKI in your setup, you can switch to Use Configuration Manager-generated certificates for HTTP site systems. When you do that it shouldn’t affect OSD, app deployment etc. However I am seeing some comments where people are complaining that PXE boot isn’t working. I haven’t got any log files to review so I can’t comment much.
Im have the same issues after update to 2103 – and the pre-req warning…
I found that the DHCP Policies we had before was disabled and the Option 66 and 67 was unticked and empty.
So after adding back the DHCP Policies and options, I am now stuck with the BCD 0x089 error.
The SMSPXE log shows a
CryptVerifySignature failed, 80090006 error
followed by
untrusted certificate: xxxxxx,
PXE::MP_InitializeTransport failed; 0x80090006 PXE::MP_LookupDevice failed; 0x80070490
PXE Provider failed to process message.
Element not found. (Error: 80070490; Source: Windows)
Looking at the Management Point – HTTPS was not selected. I Selected this again.
Both the Enrollment and Enrollment Proxy Point already had HTTPS selected
Logs now showed a slightly different error:
PXE::MP_GetList failed; 0x80070490
PXE::MP_LookupDevice failed; 0x80070490
PXE::MP_ReportStatus failed; 0x80070490
PXE Provider failed to process message.
Element not found. (Error: 80070490; Source: Windows)
The Management point seems to revert back to HTTP.
The log also continues to show
Using Management Point: http://
and
CLibSMSMessageWinHttpTransport::Send: WinHttpOpenRequest – URL: :80 GET /SMS_MP/.sms_aut?MPKEYINFORMATIONEX
PS: I reinstalled PXE / WDS a few times with no benefit to this.
So maybe the underlaying issue is a SCCM installation not setup properly for HTTPS?
Hi AJ, did you or anyone get this resolved? I am upgrading to 2103 and need to know this for my org as we use PXE and it cannot go down whatsoever. Thanks.