KB2267602 Defender Update Deletes Shortcuts & ASR Issues
After installing the latest Defender update, KB2267602, some users are unable to utilize the application shortcuts on the Start menu and taskbar. Microsoft has acknowledged this issue by logging an incident ticket (MO497128) and is working on a fix.
After installing KB2267602 version 1.381.2140.0 on a device, the application shortcuts on the Start menu and taskbar are automatically deleted. Reports coming in from multiple customers being impacted by this due to attack surface reduction rules. The issues have been reported over Twitter and other social platform by multiple users.
Microsoft has published a new incident MO497128 confirming that KB2267602 Defender update indeed causes issues to users accessing the application shortcuts on Start Menu and Taskbar.
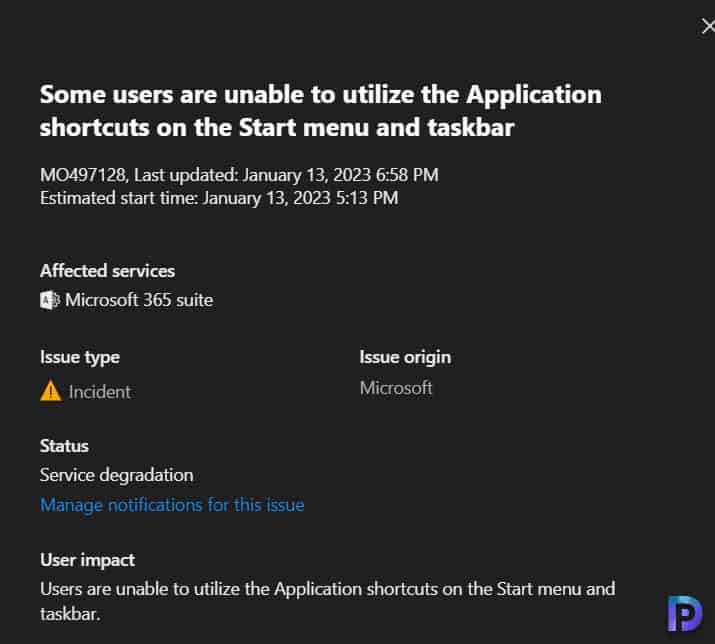
Tracking MO497128 Incident
If you have installed KB2267602 update on your devices and have been experiencing the issues, here are some updates related to MO497128 incident:
- First Response from Microsoft: We’re reviewing customer report data to determine our next troubleshooting steps.
- Second Response from Microsoft: We’re investigating recent changes to the Microsoft Defender service to identify the underlying root cause and formulate a mitigation plan.
- Third Response from Microsoft: We’ve identified that a specific rule was resulting in impact. We’ve reverted the rule to prevent further impact whilst we investigate further. This quick update is designed to give the latest information on this issue.
- Fourth Response from Microsoft: We reverted the offending ASR rule, however, this change is propagating throughout the environment and could take several hours to complete. We recommend that you take action to place the offending ASR rule into Audit Mode and prevent further impact until the update has completed deployment
To track this issue, you can visit the Microsoft 365 admin center health dashboard and select Service Health. Select the Service – Microsoft 365 Suite and here you can track all the details about this issue. If you wish to get the updates about the MO497128, you can select customize and configure email.
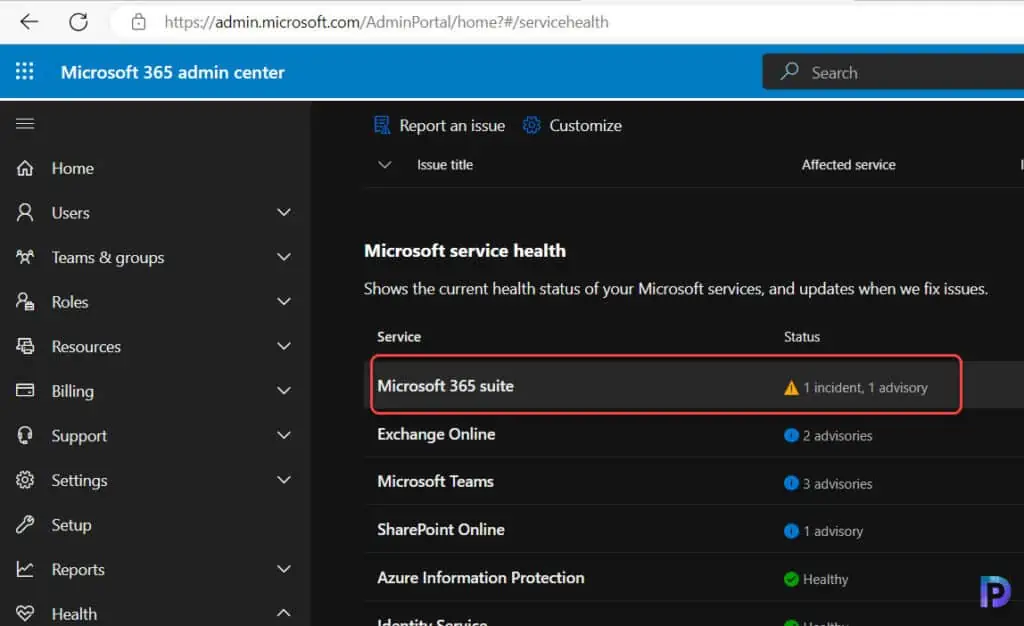
KB2267602 Defender Update Affecting ASR Rules
The KB2267602 update is causing the ASR (Attack Surface Reduction) rule to block Win32 API calls from Office Macro and even blocking applications such as OfficeClickToRun.
Notice that ASR is blocking the execution of applications on devices such as browser (explore.exe), office click to run, RuntimeBroker.exe etc.
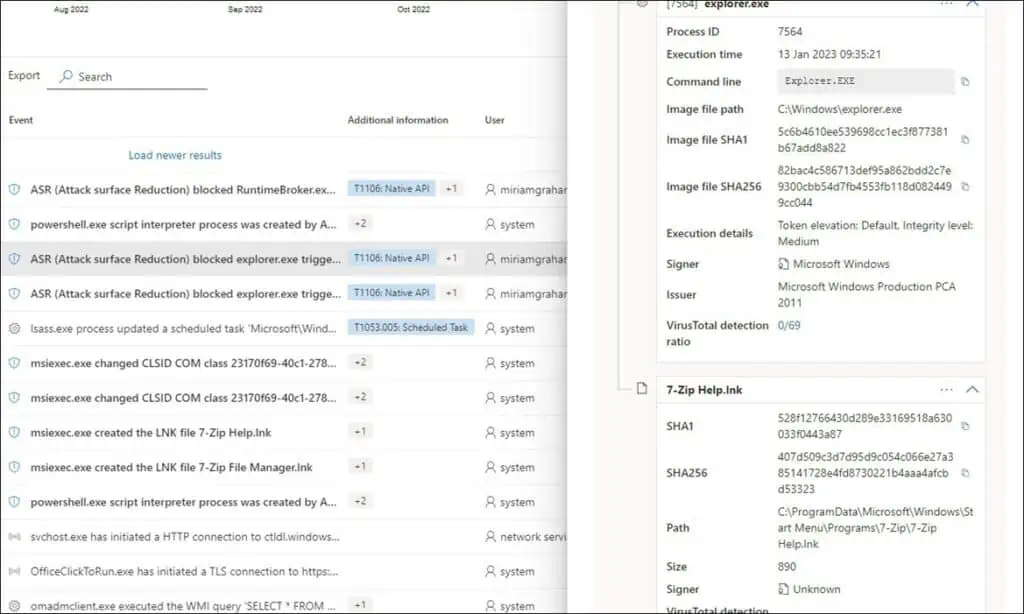
KB2267602 Workaround – Modify ASR Rules
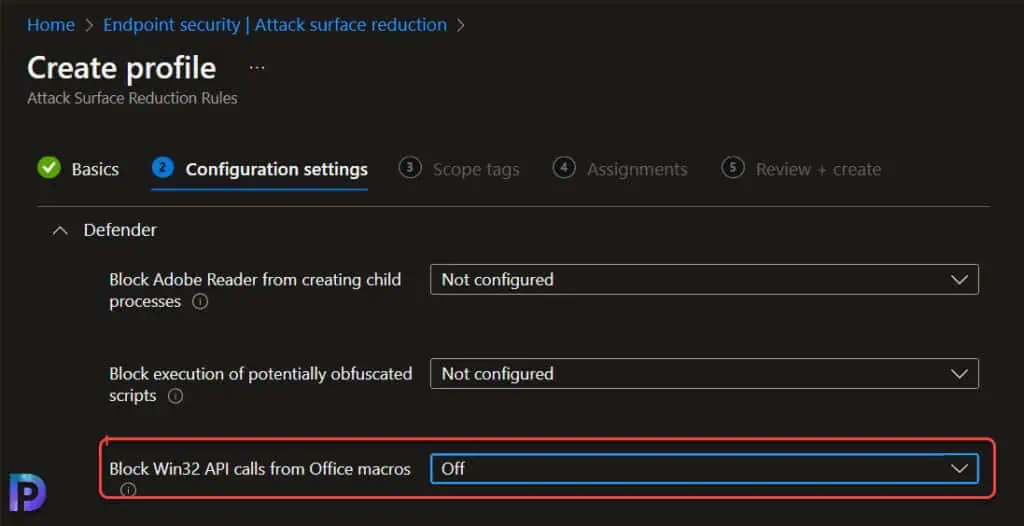
If you are deploying the defender updates with Intune, and if the rule is deleting the shortcuts from the taskbar and blocking the applications, here is a workaround for that. All you need to do is edit the ASR rule and under the Configuration Settings, change the setting Block Win32 API calls from Office macros to Off. If you set it to Audit it may not work as reported by users.
Note: Microsoft is working on this issue and will resolve it soon. Until then, you can try the workaround that is mentioned above. If the above workaround didnt work for you, please let me know in the comments section.
Workaround 1 – Launch the Office Apps via App Launcher
The following workaround has been suggested by Microsoft for users experiencing issues after installing the KB2267602 Defender update.
While we investigate the underlying issue, users can directly launch Office apps by using the Office app or through the Microsoft 365 app launcher. More details on the Microsoft 365 app launcher can be found in https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a.
Workaround 2: Configure ASR Rule to Audit Mode
The following workaround has been recommended by Microsoft for setups using Intune to manage defender updates.
We recommend that you put the ASR rule to Audit Mode to avoid further impact. This can be done through the following options:
- Using Powershell: Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- Using Intune: https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- Using Group Policy: https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- Note that ASR rule “Block Win32 API calls from Office macros” with ID: 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b
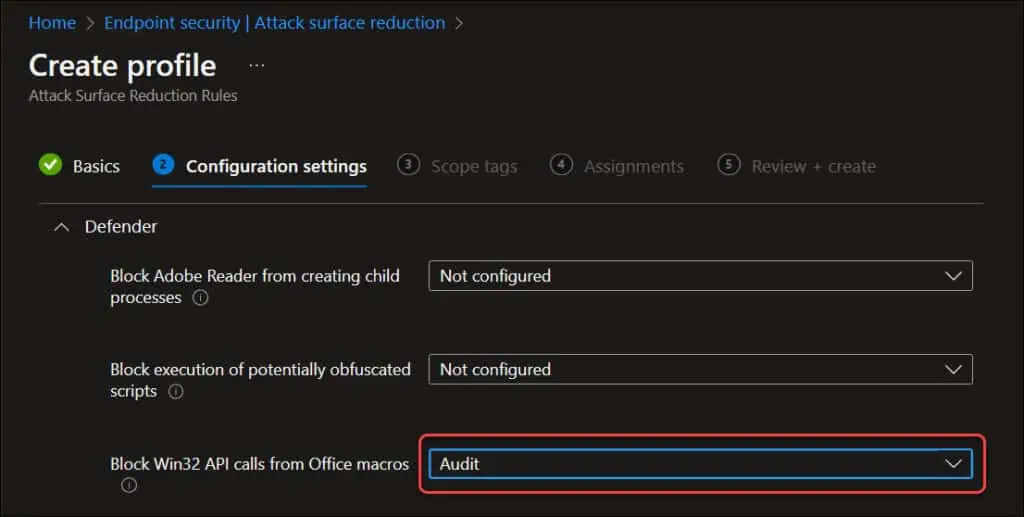
You can also set the rule to disabled mode. In that case, please consider using the following PowerShell command:
Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions Disabled

Shortcuts for Office can be restored by doing quick repair option from programs and features.