Overview of Attack Surface Reduction Rules in Intune
In this guide, we will learn about the Attack Surface Reduction Rules in Intune. Using Intune, you can create and configure ASR rules for your organization. Let’s examine what attack surface reduction rules are, as well as a list of the ASR configurable rules.
The Attack Surface reduction rules that you create in Intune (MEM) apply to Microsoft Defender for Endpoint Plan 2, Microsoft 365 Defender and Microsoft Defender Antivirus. There are many examples of ASR rules that you can create with Microsoft Intune and I will share a list of ASR Rules in this guide.
Microsoft recommends you to test how Intune ASR rules will impact your organization before enabling them by running ASR rules in audit mode for a brief period of time. While you are running the rules in audit mode, you can identify any line-of-business applications that might get blocked erroneously, and exclude them from ASR. Start with a small, controlled group to limit potential work disruptions, and later you can expand your deployment across your organization.
Attacks Surface Reduction is a complex topic, and there are many aspects to consider. To make it easier I am going to list some resources for getting started with Attack Surface Reduction rules in Intune.
- Understand and use attack surface reduction capabilities
- Attack surface reduction rules overview
- Plan attack surface reduction (ASR) rules deployment
- Test attack surface reduction (ASR) rules
- Enable attack surface reduction (ASR) rules
- Operationalize attack surface reduction (ASR) rules
What are Attack Surfaces?
Attack surfaces are all the places where your organization is vulnerable to cyberthreats and attacks. Defender for Endpoint includes numerous capabilities to help reduce your attack surfaces.
All the points where your company is exposed to cyberthreats and attacks are known as attack surfaces. Various features in Defender for Endpoint might help you decrease your attack surfaces.
Methods to Configure ASR Capabilities
When you configure attack surface reduction capabilities, you can choose from among several methods:
- Microsoft Endpoint Manager (includes Microsoft Intune and Configuration Manager)
- Group Policy
- PowerShell cmdlets
What are Attack Surface Reduction Rules in Intune?
Attack surface reduction measures focus on actions that malware and malicious software commonly take to infect computers, such as: executable files and scripts used in Office applications or web mail that attempt to download or run files obfuscated. Another example is suspicious script behaviors that apps don’t usually initiate during normal day-to-day work.
For Intune, ASR rules target certain software behaviors, such as:
- Launching executable files and scripts that attempt to download or run files
- Running obfuscated or otherwise suspicious scripts
- Behaviors that apps don’t usually occur during normal day-to-day work
By reducing the different attack surfaces, you can help prevent attacks from happening in the first place. Take a look at detailed guide on how to use attack surface reduction capabilities.
Operating System Requirements for ASR Rules
You can set attack surface reduction rules for devices that are running any of the following editions and versions of Windows:
- Windows 10 Pro, version 1709 or later
- Windows 10 Enterprise, version 1709 or later
- Windows Server, version 1803 (Semi-Annual Channel) or later
- Windows Server 2022
- Windows Server 2019
- Windows Server 2016
- Windows Server 2012 R2
Licensing Requirements for ASR
To use the entire feature-set of attack surface reduction rules, you need:
- Microsoft Defender Antivirus as primary AV (real-time protection on)
- Cloud-Delivery Protection on (some rules require that)
- Windows 10 Enterprise E5 or E3 License
Attack Surface Reduction Rules Deployment Phases
As with any new, large-scale implementation that could affect your line of business, it is important to plan and implement it in a methodical way. Because ASR rules are so good at stopping malware, they need to be carefully planned and set up to make sure they work best for your customers’ unique workflows. For ASR rules to work in your environment, you need to carefully plan, test, implement, and run them.
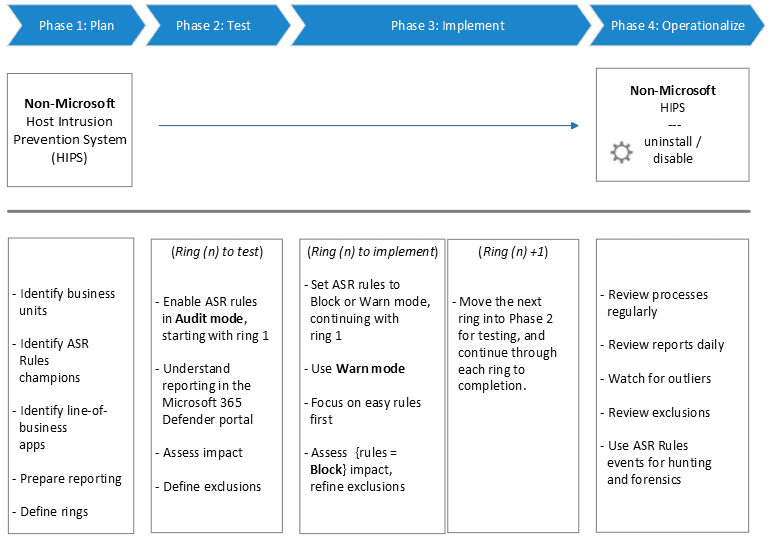
The below diagram illustrates four deployment phases of Attack Surface Reduction Rules.
- Phase 1: Plan for ASR Rules
- Phase 2: Test attack surface reduction (ASR) rules
- Phase 3: Implement or Enable attack surface reduction (ASR) rules
- Phase 4: Report and troubleshoot Microsoft Defender for Endpoint ASR Rules
List of Attack Surface Reduction Rules In Intune
With Intune, you can configure the following Attack Surface Reduction (ASR) rules and deploy it to your endpoints. The below table lists all the Intune ASR Rules, description and GUID that you can configure for your endpoints.
| Intune ASR Rule Name | ASR Rule Description | Rule GUID |
|---|---|---|
| Block abuse of exploited vulnerable signed drivers | This rule prevents an application from writing a vulnerable signed driver to disk. The vulnerable signed drivers can be exploited by local applications – that have sufficient privileges – to gain access to the kernel eventually leading to system compromise. | 56a863a9-875e-4185-98a7-b882c64b5ce5 |
| Block Adobe Reader from creating child processes | This rule prevents attacks by blocking Adobe Reader from creating processes. | 7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c |
| Block all Office applications from creating child processes | This rule blocks Office apps from creating child processes. Office apps include Word, Excel, PowerPoint, OneNote, and Access. | d4f940ab-401b-4efc-aadc-ad5f3c50688a |
| Block credential stealing from the Windows local security authority subsystem (lsass.exe) | This ASR rule helps prevent credential stealing by locking down Local Security Authority Subsystem Service (LSASS). LSASS authenticates users who sign in on a Windows computer. Microsoft Defender Credential Guard in Windows normally prevents attempts to extract credentials from LSASS. | 9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2 |
| Block executable content from email client and webmail | This rule blocks the following file types from launching from email opened within the Microsoft Outlook application, or Outlook.com and other popular webmail providers | be9ba2d9-53ea-4cdc-84e5-9b1eeee46550 |
| Block executable files from running unless they meet a prevalence, age, or trusted list criterion | This ASR rule blocks executable files, such as .exe, .dll, or .scr, from launching. Thus, launching untrusted or unknown executable files can be risky, as it might not be initially clear if the files are malicious. | 01443614-cd74-433a-b99e-2ecdc07bfc25 |
| Block execution of potentially obfuscated scripts | This rule detects suspicious properties within an obfuscated script. Malware writers and developers of legitimate software frequently employ script obfuscation to conceal intellectual property or speed up the loading of scripts. In order to make malicious code more difficult to comprehend and prevent it from being closely examined by security tools and humans, malware developers also employ obfuscation. | 5beb7efe-fd9a-4556-801d-275e5ffc04cc |
| Block JavaScript or VBScript from launching downloaded executable content | This ASR rule prevents scripts from launching potentially malicious downloaded content. Malware written in JavaScript or VBScript often acts as a downloader to fetch and launch other malware from the Internet. | d3e037e1-3eb8-44c8-a917-57927947596d |
| Block Office applications from creating executable content | This rule prevents Office apps, including Word, Excel, and PowerPoint, from creating potentially malicious executable content, by blocking malicious code from being written to disk. | 3b576869-a4ec-4529-8536-b80a7769e899 |
| Block Office applications from injecting code into other processes | This rule blocks code injection attempts from Office apps into other processes. Attackers might attempt to use Office apps to migrate malicious code into other processes through code injection, so the code can masquerade as a clean process. | 75668c1f-73b5-4cf0-bb93-3ecf5cb7cc84 |
| Block Office communication application from creating child processes | This rule prevents Outlook from creating child processes, while still allowing legitimate Outlook functions. | 26190899-1602-49e8-8b27-eb1d0a1ce869 |
| Block persistence through WMI event subscription * File and folder exclusions not supported. | This rule prevents malware from abusing WMI to attain persistence on a device. | e6db77e5-3df2-4cf1-b95a-636979351e5b |
| Block process creations originating from PSExec and WMI commands | This ASR rule blocks processes created through PsExec and WMI from running. Both PsExec and WMI can remotely execute code. There’s a risk of malware abusing functionality of PsExec and WMI for command and control purposes, or to spread an infection throughout an organization’s network. | d1e49aac-8f56-4280-b9ba-993a6d77406c |
| Block untrusted and unsigned processes that run from USB | With this rule, admins can prevent unsigned or untrusted executable files from running from USB removable drives, including SD cards. Blocked file types include executable files (such as .exe, .dll, or .scr) | b2b3f03d-6a65-4f7b-a9c7-1c7ef74a9ba4 |
| Block Win32 API calls from Office macros | This rule prevents VBA macros from calling Win32 APIs. | 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b |
| Use advanced protection against ransomware | This rule provides an extra layer of protection against ransomware. It uses both client and cloud heuristics to determine whether a file resembles ransomware. | c1db55ab-c21a-4637-bb3f-a12568109d35 |
Create Attack Surface Reduction Rule in Intune
The process of creating a new ASR rule in Intune involves following steps:
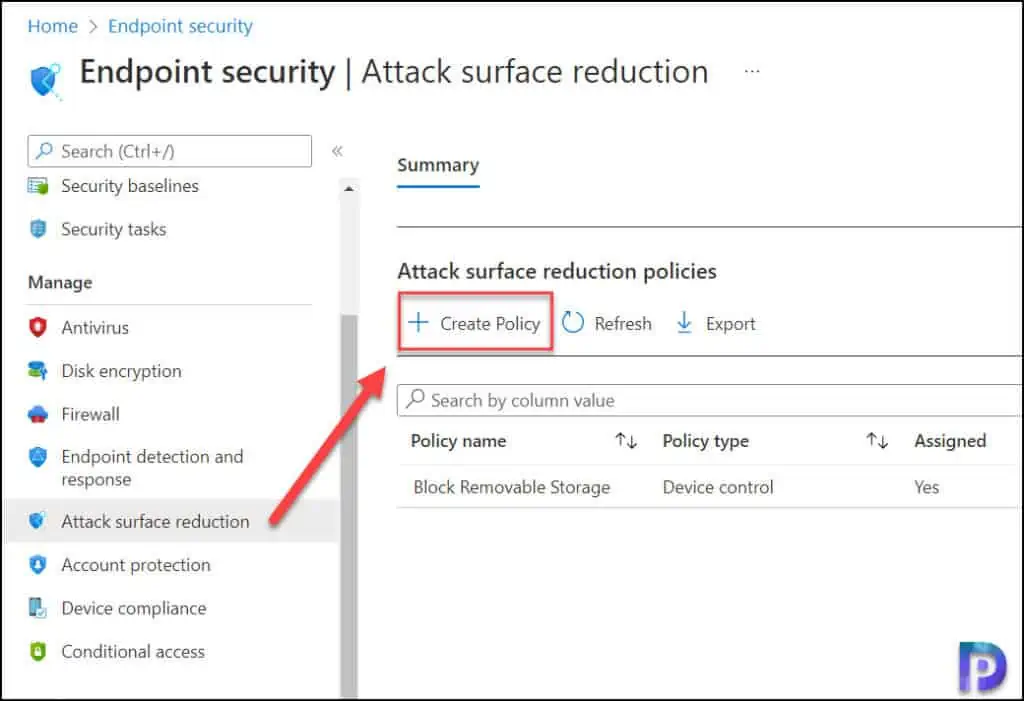
- Sign in to the Microsoft Endpoint Manager admin center.
- Select Endpoint Security and then select Attack Surface Reduction.
- Now click on Create Policy button to create a ASR rule.
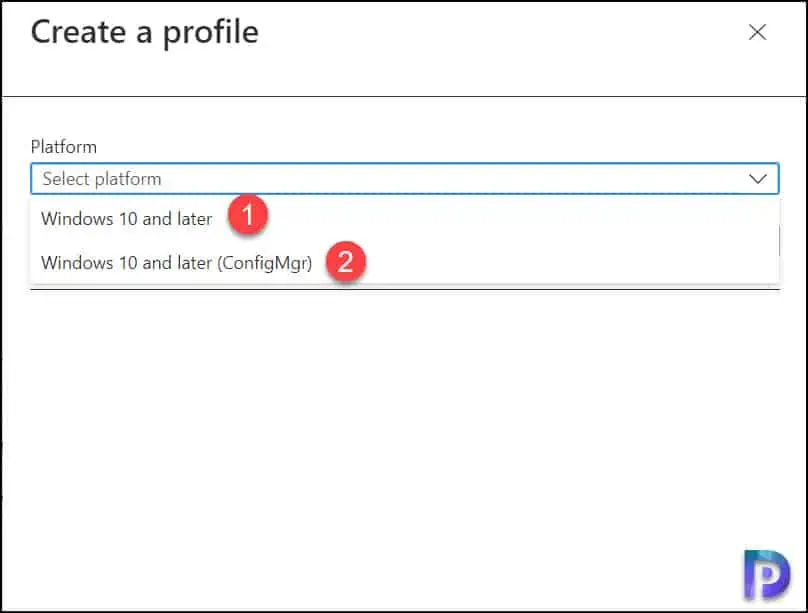
On Create a profile window, you have two options for choosing the platform.
- Windows 10 and later
- Windows 10 and later (ConfigMgr)
Select the platform as Windows 10 and later.
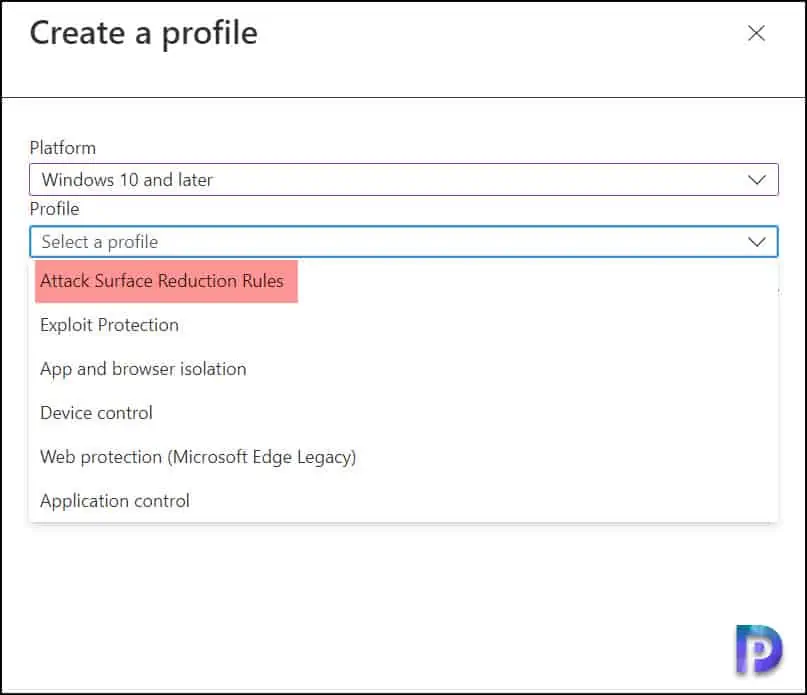
For the profile, select Attack surface reduction rules and click Create.
Configure ASR Rules using MEM | Intune
You can use Microsoft Endpoint Manager (MEM | Intune) Endpoint Security to configure custom ASR rules with following steps.
1. On the Create Profile page, click the Basics tab and enter the Profile name and description for the Attack Surface Reduction rule that you are going to configure. Click Next.
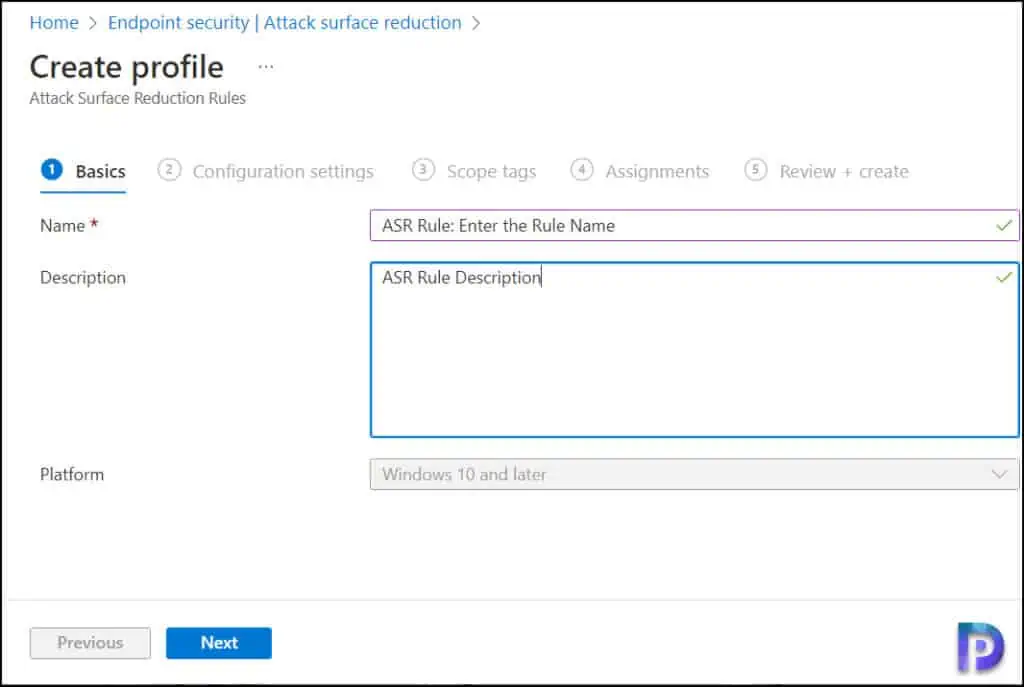
2. On the Configuration Settings tab, you’ll find a list of ASR rules that you can configure. Every ASR rule has got 4 modes that you can choose from:
- Not configured or Disable: The state in which the ASR rule hasn’t been enabled or has been disabled. The code for this state = 0.
- Block: The state in which the ASR rule is enabled. The code for this state is 1.
- Audit: The state in which the ASR rule is evaluated for the effect it would have on the organization or environment if enabled (set to block or warn). The code for this state is 2.
- Warn: The state in which the ASR rule is enabled and presents a notification to the end-user, but permits the end-user to bypass the block. The code for this state is 6.
In the Configuration settings tab, under Attack Surface Reduction Rules, set all rules to Audit mode. When you initially configure a new ASR rule in Intune, it is recommended that you test it with the Audit mode. Testing attack surface reduction (ASR) rules helps you determine if rules will impede line-of-business operations prior to enabling any rule.
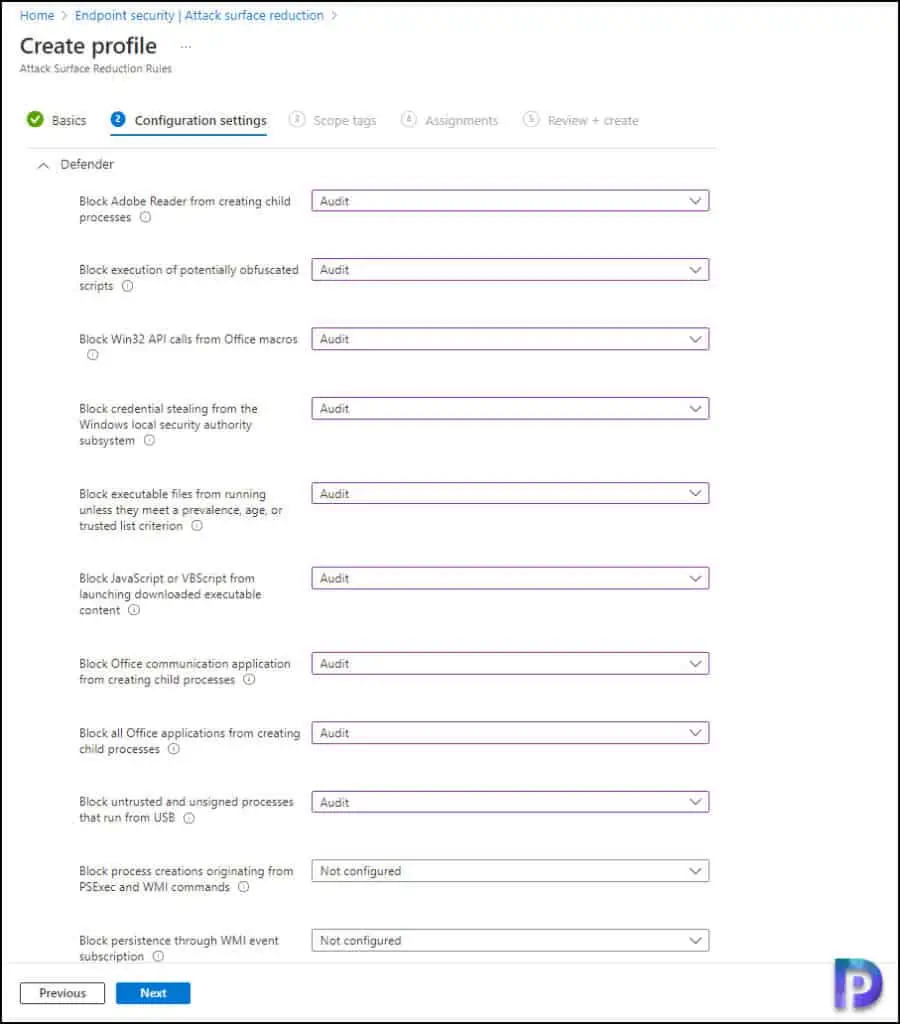
In the next steps, select the Scope Tags where you can add tag information to specific devices. On the Assignments tab, you can “deploy” or “assign” the profile to your user or device groups. Review your settings in the Review + create pane. Click Create to apply the rules.
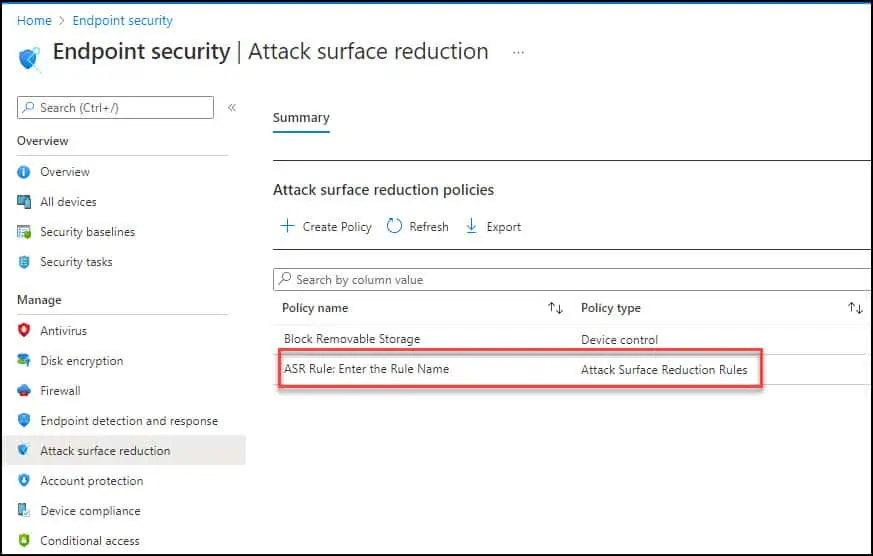
Finally, your new attack surface reduction policy for ASR rules is listed in Endpoint security | Attack surface reduction. You can select the ASR rule and make any modifications if required.
Test and Troubleshoot your Attack Surface Reduction rules
After you’ve fully deployed attack surface reduction (ASR) rules with Intune, you must have processes in place to monitor, troubleshoot and respond to ASR-related activities.
There are two ways to analyze the ADR rules and reporting details:
- Understand the Attack surface reduction rules reporting page in the Microsoft 365 Defender portal: Get a detailed report with ASR rules events, blocks, and warnings if you have an E5 subscription and use Microsoft Defender for Endpoint.
- Use Windows Event Viewer: To review apps that would have been blocked, launch Event Viewer and filter for Event ID 1121 in the Microsoft-Windows-Windows Defender/Operational log. The following table lists all network protection events that you can use for ASR troubleshooting.
| Event ID | Description |
|---|---|
| 5007 | Event when settings are changed |
| 1121 | Event when an attack surface reduction rule fires in block mode |
| 1122 | Event when an attack surface reduction rule fires in audit mode |

Hello,
I seem to be having the same issues as Colby R. mentioned.
“I see the compliance policy in deployments in SCCM, but all of my devices are marked non-compliant with the CCMSS_M365A_Settings_DetectionExitCode Equals 0 Warning.”
Any thoughts or updates? Thank you!
I seem to be having an issue getting my ASR policy to apply to my clients. I see the compliance policy in deployments in SCCM, but all of my devices are marked non-compliant with the CCMSS_M365A_Settings_DetectionExitCode Equals 0 Warning.
Any ideas?
Hi Colby,
I have the same issue you mentioned. Did you ever figure this out?