Enable Microsoft Defender for Endpoint in Intune
In this article, you will learn you how to enable Microsoft Defender for Endpoint in Intune. With few steps, you can connect Microsoft Defender for Endpoint with Intune.
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. Go through the Microsoft documentation to understand more about Microsoft Defender for Endpoint.
You can integrate Microsoft Defender for Endpoint with Microsoft Intune as a Mobile Threat Defense solution. Other than Intune, the Microsoft Defender for Endpoint directly integrates with various Microsoft solutions including:
- Azure Defender
- Azure Sentinel
- Intune
- Microsoft Cloud App Security
- Microsoft Defender for Identity
- Microsoft Defender for Office
- Skype for Business
Before you enable Microsoft Defender for Endpoint in Intune, ensure you are aware of these.
- The set-up requires administrative access to both the Microsoft Defender Security Center, and to Intune. I will be using the global administrator account to complete the integration of defender for endpoint and Intune.
- Enabling Microsoft Defender for Endpoint in Intune is a one-time process for a tenant.
- After you have enabled support for Microsoft Defender for Endpoint in Intune, you established a service-to-service connection between Intune and Microsoft Defender for Endpoint.
Table of Contents
Enable Microsoft Defender for Endpoint in Intune
Use the following steps to enable Microsoft Defender for Endpoint in Intune.
- Sign in to the Microsoft Endpoint Manager admin center.
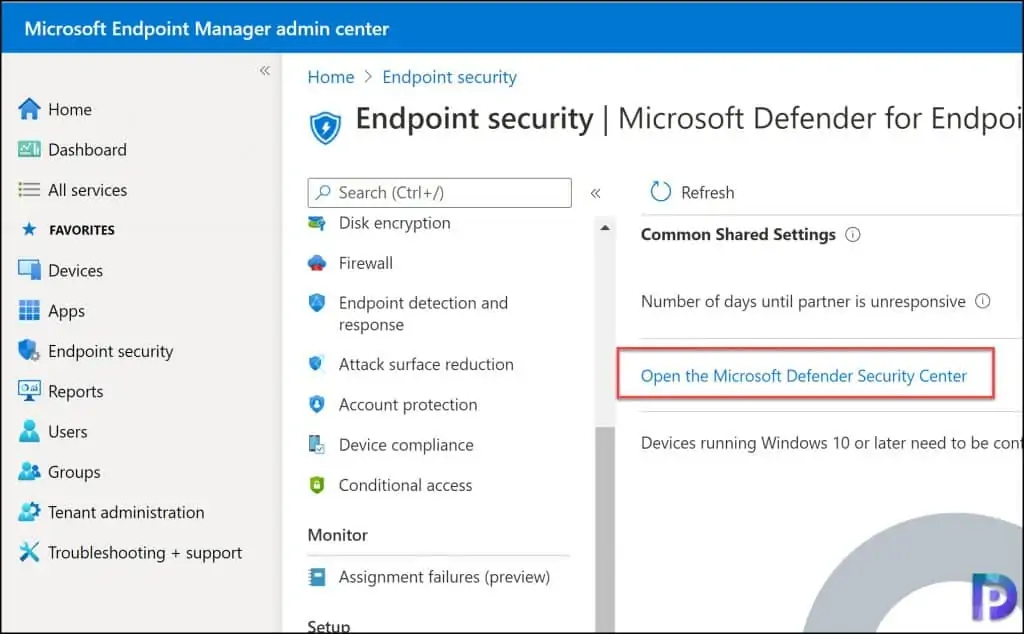
- Select Endpoint security > Microsoft Defender for Endpoint, and then select Open the Microsoft Defender Security Center.
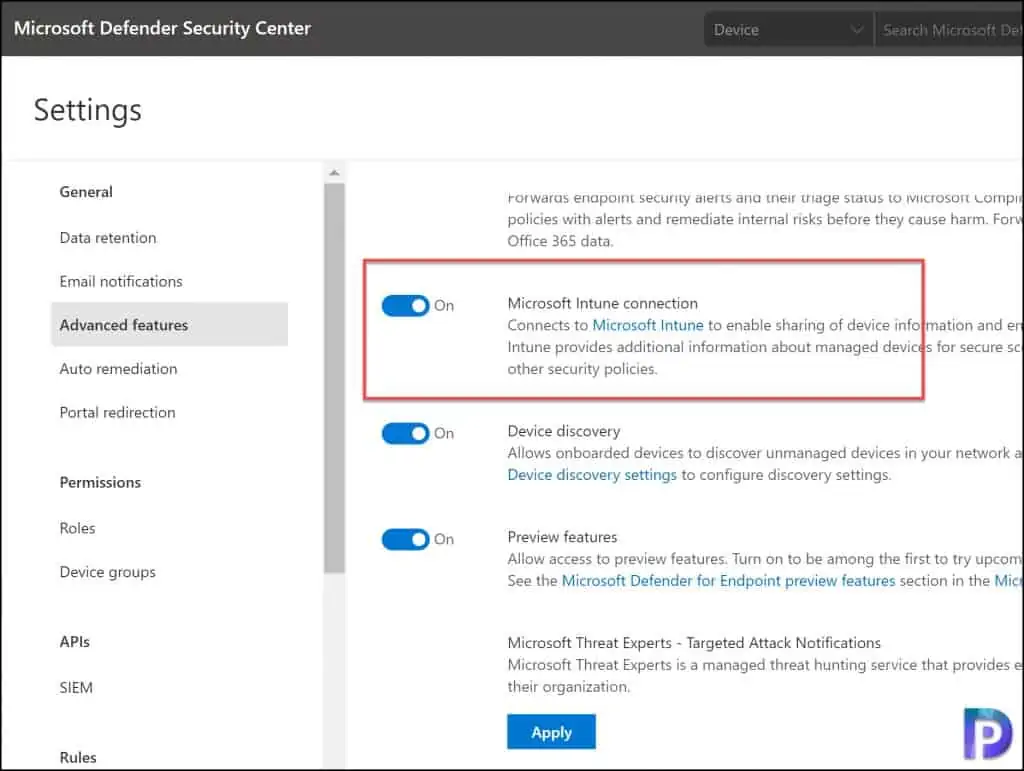
- In Microsoft Defender Security Center, select Settings > Advanced features.
- Scroll down and enable Microsoft Intune connection (choose On) and click Save Preferences.
Under the Advanced features, the list is long, and you have to scroll down to find the Microsoft Intune connection. For Microsoft Intune connection, just turn the slider from Off to On. Click Save Preferences.
Now go back to Microsoft Endpoint admin center and select Microsoft Defender for Endpoint. In the right pane, you can configure the following settings.
MDM Compliance Policy Settings
The MDM compliance policy setting is for the devices that you want to connect to Microsoft Defender for Endpoint.
- Connect Android devices to Microsoft Defender for Endpoint
- Connect iOS devices to Microsoft Defender for Endpoint
- Connect Windows devices to Microsoft Defender for Endpoint
- Block unsupported OS versions
Enable the required settings to connect your devices to Microsoft Defender for Endpoint.
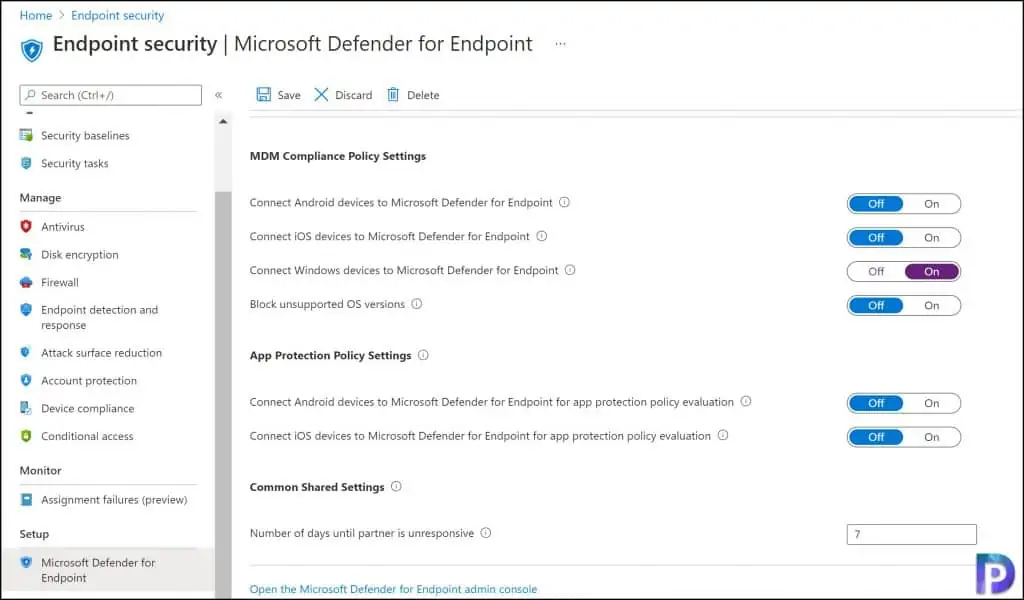
App Protection Policy Settings
The App Protection Policy settings apply to App Protection Policy MTD Connector usage. They are applicable only for Android and iOS devices.
- Connect Android devices to Microsoft Defender for Endpoint for app protection policy evaluation
- Connect iOS devices to Microsoft Defender for Endpoint for app protection policy evaluation
Common Shared Settings
Under the Common shared settings, you can configure the number of days until the partner is unresponsive, and the value is 7 days by default. As mentioned earlier, after you enable Microsoft Defender for Endpoint in Intune, you establish a service-to-service connection between Intune and Microsoft Defender for Endpoint. The services are synchronized at least once every 24 hours according to Microsoft.
