Fake Microsoft Account Unusual Sign-in Activity Emails
Recently, a lot of people have been getting emails about unusual sign-in activity on their Microsoft accounts. These unusual sign-in activity emails from a fake Microsoft account are dangerous, and you shouldn’t click any of the links in the email.
In the last few weeks, I’ve been getting a lot of these emails about unusual sign-in activity. The emails are so convincingly real-looking that it’s impossible to tell which ones are fake.
Anyone would assume this is being sent by the Microsoft Accounts Team based on the sender address, email composition, and other details.
Microsoft never sends such phishing emails if your account has not been successfully signed in. The real emails from Microsoft always appear in the Inbox folder, while the fake emails typically land in the Junk Email folder, which is crucial.
I’m sure that a number of account users received these emails, and the attacker intended to trap some of them in order to access their email accounts. Actually, the main goal of sending these strange Sign-in Activity emails is to persuade users to click the links in the email. Read how to secure your email account from hackers.
These unusual sign-in activity fake emails have nearly identical information fields and even the same sender address as the real email notifications sent by Microsoft. Therefore, it is crucial to understand how to tell these fake emails apart from real emails, which I will explain in more detail in the following section of this article.
The goal of this article is to help my readers and make them aware of such fake Microsoft emails and prevent account hacks that are being attempted by attackers every moment.
Fake Microsoft Account Unusual Sign-in Activity Emails
Let me show you an example of a fake Microsoft Account unusual sign-in activity email and the details included in such emails. This email landed in the Junk Email folder of my Microsoft Account as it failed to pass the security checks.
Unusual sign-in activity
We detected something unusual about a recent sign-in to the Microsoft account username@hotmail.com.
Sign-in details
Country/region: United States
IP address: XX.XX.XX.XX
Date: Sat, 09 Jul 2022 22:56:24 +0000
Platform: Windows 10
Browser: Firefox
A user from the United States just logged into your account from a new device. If this wasn’t you, please report the user. If this was you, we’ll trust similar activity in the future.
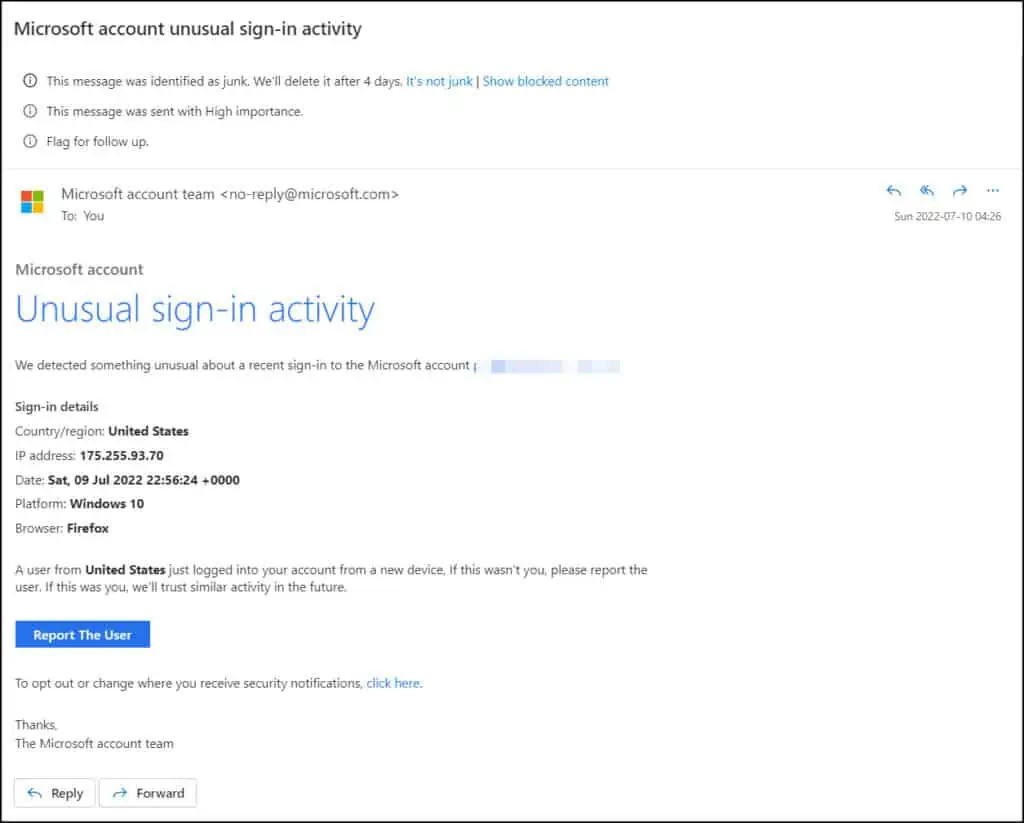
As per the above email, the account was accessed from the United States with a given IP address. The email also displays the browser and OS platform, along with the date and time the account was accessed.
The location, IP address, and sender email address of the email that you received may differ in your case. However, you need to pay extra attention to the links that are included in such fake emails.
If you have received a similar email that reports unusual sign-in activity for your account, please do not click any of the links provided in the email. These fake links will open a browser window with a sign-in screen where you must enter your account information. The information is sent to attackers as soon as you enter the account information.
You can actually trace the attacker’s IP address and other information if you receive emails about unusual sign-in activity. There are many ways to tell if an email is fake when you receive one of these emails. I’ll demonstrate how to do that.
Using IP Address Lookup to Tracking Location
The email states that the account was accessed from the United States, and it also provides the IP address. You can use an IP address lookup to find out where this IP address is located by following a few simple steps.
There is one important thing that you must know when you trace an IP address.
When using an IP address lookup tool, users often think they are going to find the exact location of an IP address. This is simply not true. No Internet Protocol (IP) address database can provide the exact physical address of an IP address location. At best, you’ll get the exact city in which the user of the IP is located.
There are numerous websites and online resources that can assist you in tracking down the IP address. It’s important to realize that no IP lookup tool can guarantee accuracy.
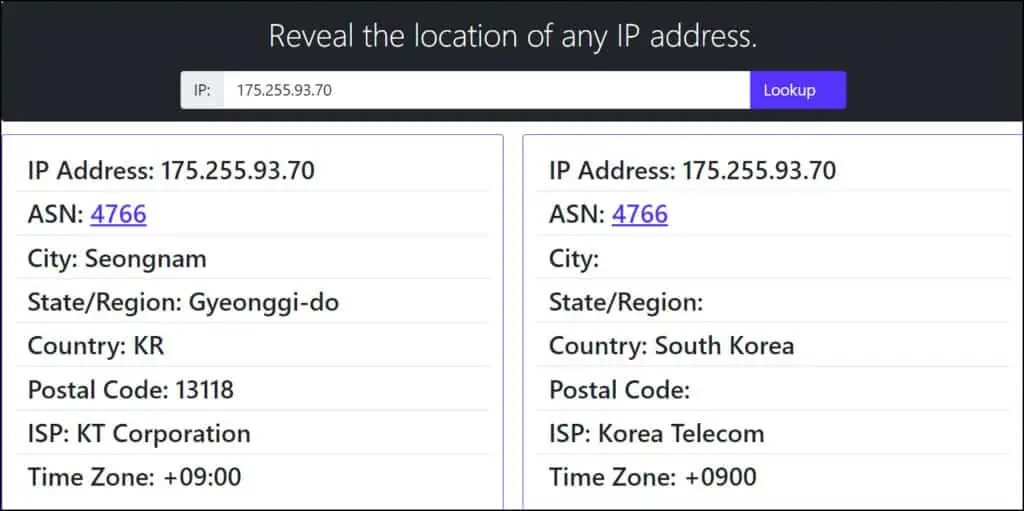
When I used one of the IP lookup tools to find the IP address listed in the fake email, I was surprised to find that it was located in South Korea, specifically Seongnam, rather than the United States. This is the first indication that the emails you received about unusual sign-in activity for your Microsoft Account were fraudulent.
View Email Message Internet Header
For every email that you receive, you can view the email message headers. An email message internet header provides a list of technical details about the message, such as who sent it, the software used to compose it, and the email servers that it passed through on its way to the recipient.
Email message headers are accessible in both Outlook and Outlook Web. To determine whether the sender is using spoofing to hide their email address, it is necessary to view the email headers. If you look at the email header, you can see if the email address is accurate or incorrect.
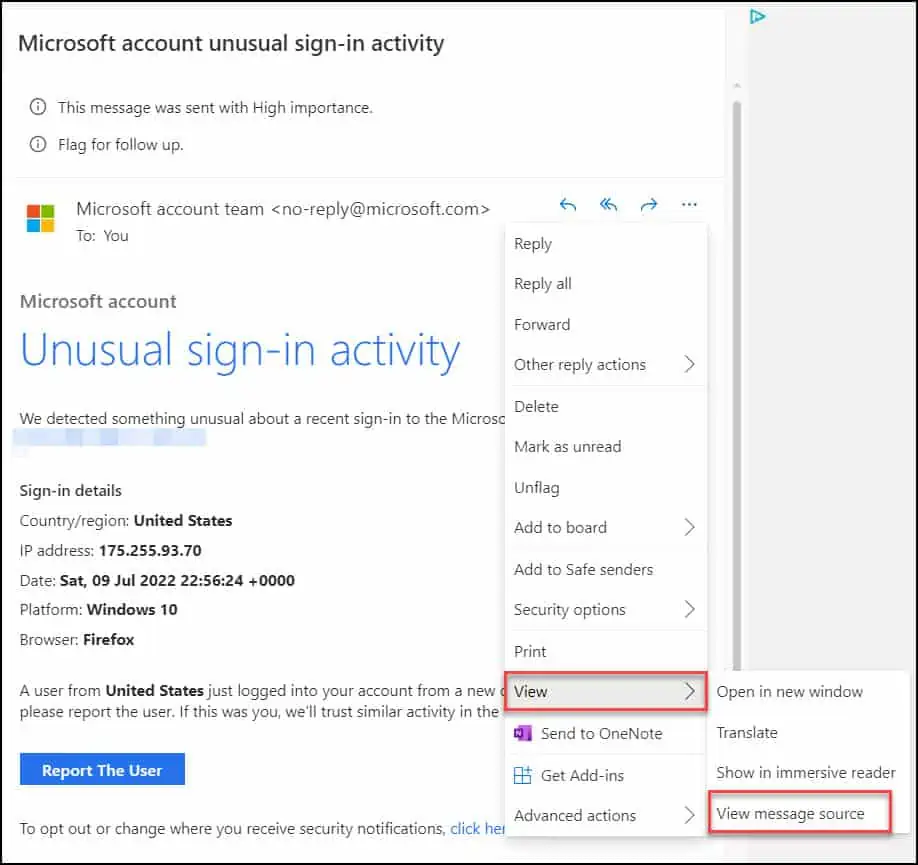
To view the email message headers for the Microsoft Account Unusual Sign-in activity emails that you received, select the three horizontal dots at the top of the message window and select View > View message source.
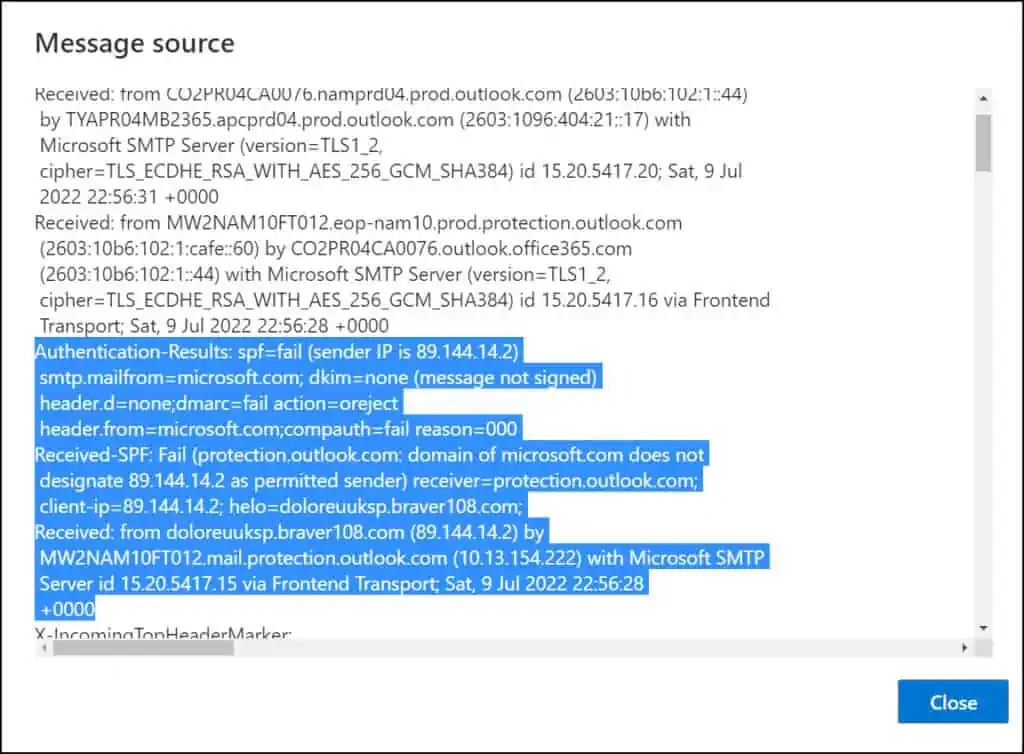
You can view a lot of technical information about the message in the Message Source window that is typically hidden when you view an email in your inbox.
It is clear from this screenshot that the attacker is the one who sent the phony emails purporting to be from Microsoft. The ‘Reply To‘ field is marked with an email address which doesn’t belong to Microsoft at all.
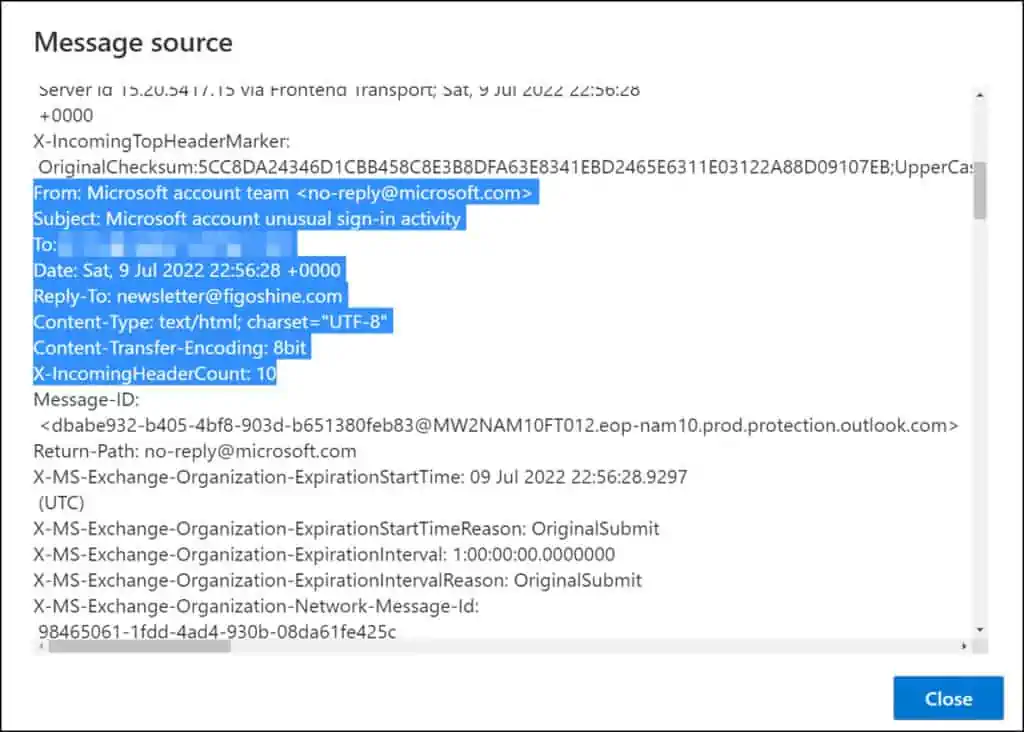
The email message header also shows the attackers IP address, and we see that Microsoft does not designate this IP as permitted sender. This email has also failed the authentication checks, and you can confirm that from Authentication results.
This confirms the unusual sign-in activity email that you received from Microsoft was not sent by Microsoft, and it was sent by an attacker.
How to Detect Fake Unusual Sign-in Activity Emails?
Okay, so how do you spot these fake emails that claim someone else accessed your account remotely? The answer is: When you click on links, you should always be aware of the URLs of the landing pages. Make sure the URL is valid and free of errors or a certificate that isn’t valid before entering your login information in a login form that has been displayed.
Microsoft’s spam detection capabilities are excellent, and typically, these emails about account unusual sign-in activity are classified as junk by Microsoft, which is why they appear in the junk folder.
Typically, users will click a link without ever checking the URL, and the majority of phishing sites are created to look like legitimate websites. The URLs should be observed carefully in the browser when you open links from your emails. You can also hover your mouse over the link, but don’t click, to see if the address matches the link that was typed in the message.
The same is the case with attachments that arrive in your inbox. Without scanning then with a proper antivirus scanner, you should never download and open anything from that attachment.
Inform Microsoft about Phishing Scams
You can report phishing emails to Microsoft when you receive fake Microsoft account emails about unusual sign-in activity in your inbox. You are also helping other Microsoft account users by reporting such emails to Microsoft.
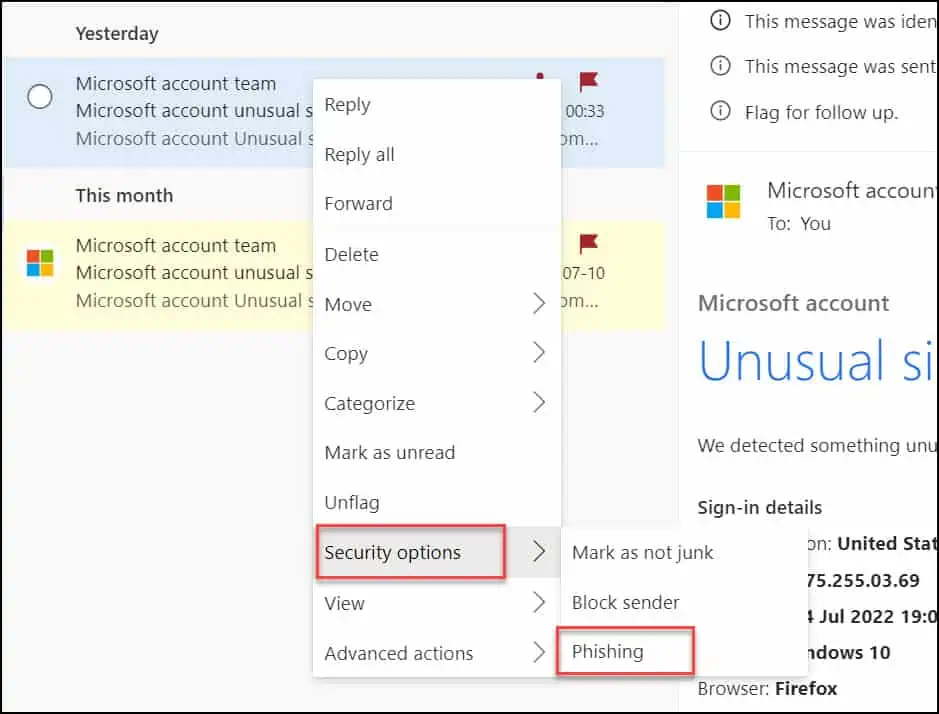
Reporting phishing scams aids in the protection of both your and other people’s information. To report phishing emails to Microsoft, right-click the email and select Security Options > Phishing.
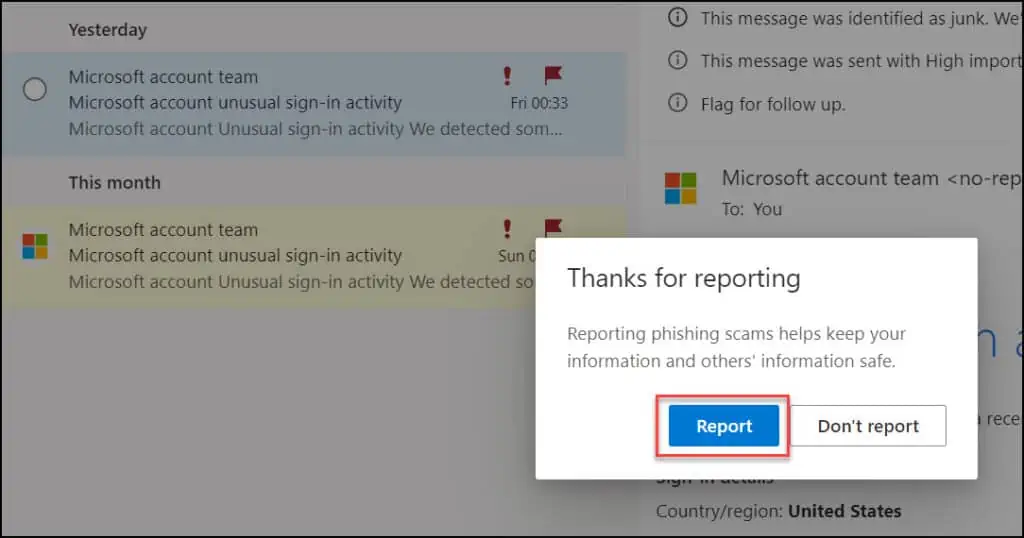
Click Report and the email is now sent to the Microsoft security team, who will review it and block such emails in the future.
Check your most recent sign-in history with Microsoft Account
You always receive an email when your account is logged in from a remote location, whether it be a Gmail account or a Hotmail/Outlook account. The emails are sent even when someone tries to log in to your account, alerting you to this activity.
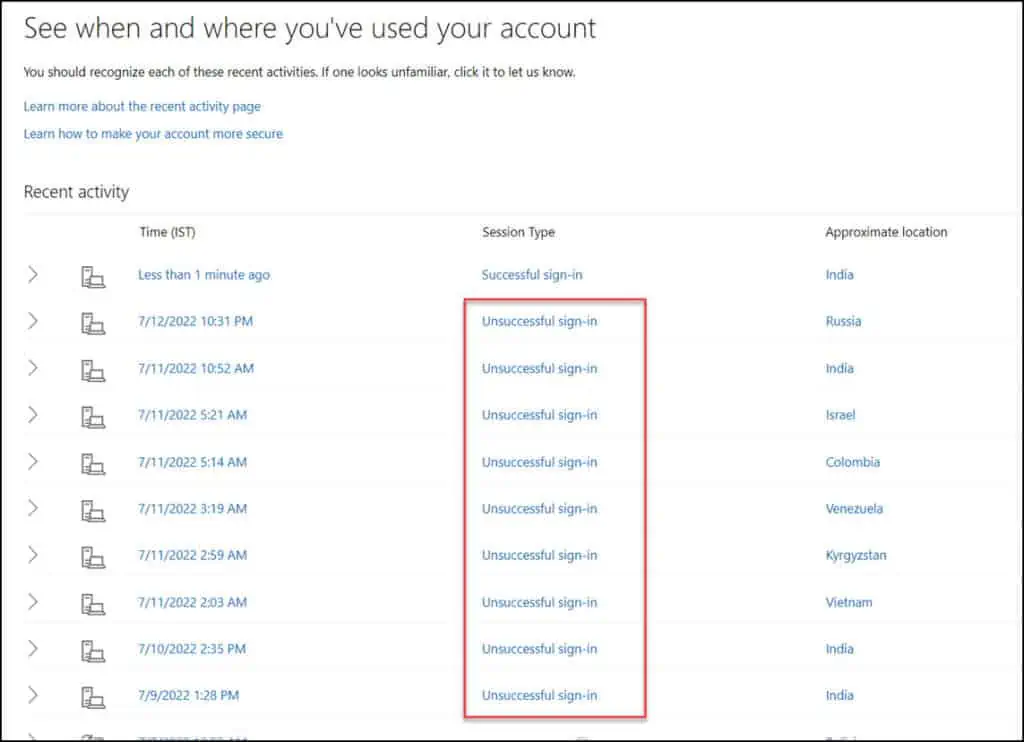
When using Hotmail or Outlook, you can check your account activity page to see who has accessed your account. You will be prompted to authenticate when you visit this page, and you can view account activity only after successful authentication.
The account activity details include the session type, approximate location, and the date and time your account was accessed. The session type is significant in this situation because it indicates whether the account successfully signed in or whether an unsuccessful sign-in attempt was made.
Repeated unsuccessful sign-in attempts usually indicate that someone is trying to log in to your email account but with a wrong password. Unfortunately, you cannot prevent that because if your email address is already known to attackers or exposed, you will see this activity often.
The approximate location is typically the country name, and you can use the IP lookup to trace the IP address. What’s critical here is if the account activity shows that your account had a successful sign-in from a unknown remote location, it means you need to secure your account at the earliest.
The best way to handle emails with fake Microsoft Account sign-in activity
In this section, I will list down essential points on how to deal with these fake unusual sign-in activity emails pretending to be from Microsoft.
Avoid clicking the links in the dubious email
Never open any links or attachments found in shady emails. When you suspect the email is fake, or when you receive a fake password reset email, you should never click any links in the email. When you know the email is fake, there is no point in visiting those links.
Avoid downloading and opening attachments from suspicious emails
Many of us receive emails with claims that we have won prizes, fake orders are being shipped, or large sums of money are about to be sent, among other things. These are fake emails, and you should never download and open attachments from such emails. These attachments usually contain virus, Trojan or malicious code that is intended to harm your computer and steal your data.
Scan Emails and Attachments with Antivirus Scanner
When you install Windows 10 or Upgrade to Windows 11, it comes installed with Windows Security. This software provides the latest antivirus protection and your device will be actively protected from the moment you start Windows.
You must scan the emails and the attachments using an Antivirus scanner. Most antivirus softwares can even scan within a .zip file and detect malicious content.
Mark Suspicious Emails as Junk
If you are confident about an email that arrived in your inbox is unwanted or spam, right-click the email and select Security Options > Mark as Junk. When you mark an email as Junk, the next it arrives, it will be moved to Junk Email folder.
Use Strong passwords to secure your Email account
Most users have the problem with remembering the passwords, so they set an easy password and sometimes same password is used for all their accounts. This should be avoided, and you must always set a complex and unique password for your accounts. Read this article to know how to create secure hack proof strong email password.
Use Password Managers
When you have multiple Hotmail/Outlook accounts, remembering the passwords will be difficult. The solution is to use the password managers and these softwares can remember your passwords and help you autofill in the browser when required.
Use Two-Step verification with Microsoft account
Two-step verification helps protect you by making it more difficult for someone else to sign in to your Microsoft account. It uses two different forms of identity: your password, and a contact method (also known as security info). Here is a helpful article on how to use two-step verification for Microsoft account.

Hi, I have the same issue as Ruby, I clicked on the report the user button and then I hit the send button and sent the email to a weird email address. I tried to change my password but I would not receive the sms with the code. I had to answer questions have my identity verified, which was done successfully, I got an password recovery email to my other email but I messed up the password change, coz I didn’t expect the verification to be done so fast I also changed my phone trusted phone number… the change can take up to 30days.. so now I can’t access the account data until microsoft changes the phone number in my account.
What worries me the most is that any email I sent from the attacked email account out is not delivered…
What shall I do?
Thank you
Lucie
Hello! I have received that email and I have clicked the link. Now I receive a lot of spam emails What can I do?
Create a rule and block the emails.
Thank you!
This was a very helpful article. I received a couple of emails just like this, and reported them both to Microsoft as phishing. Ordinarily, when a malicious email makes it to my inbox, the header tends to reveal that it wasn’t actually sent from the declared source. In this instance, the “sent from” address appears to be no-reply microsoft, but it’s not. In the article you refer to this as header spoofing, and I followed your instructions to view the message source, to confirm as much. Thanks for rendering such an important online security service, Prajwal.
Hello, I got this email in my junk and I clicked the report the user and it didnt take me to a new tab but it got me to send “Report the user” to their weird email address and I clicked send. It didnt have any information of mine or I didn’t put anything there.
I recently got one of these exact messages. I never clicked on any of its links. !!!
Anyways, if someone was attempting to access my account, shouldn’t my Hotmail App for authentication alert me?? I have been using two-way verification for over a year now.
I get such messages, but when I check in my account (not using the link in the mail, but accessing the real MS site) I see that the IP is assigned to “MSFT”!
I use WIndows Live Mail that checks every 10 minutes and the message type is “Automatic Sync”, so I am not sure what is happening here… I see a few attempts from the US and many from my own location.
Sign in to your Microsoft Account and check the sign-in activity. What you need to check is the successful sign in and the location. If you find successful sign-in from an unknown location, you must change the account password immediately.