Fix Unable to RDP Azure VM using AAD Credentials
The inability to RDP to an Azure VM using Azure AD (AAD) credentials is a frequent problem that most of us experience. If you are unable to RDP Azure VM with Azure AD credentials, this troubleshooting article will surely help you.
Few months ago, I was in a similar situation where I was unable to RDP Azure VM using Azure AD credentials. I created a new VM and attempted to RDP and even that failed. This was a Windows 11 VM in Azure and AAD credentials didn’t work at all.
Based on my research, many people have issues in connecting to Virtual Machines hosted in Azure with their AAD credentials. Most of us don’t know where to begin troubleshooting this issue. Some of you may assume that you are entering wrong password and attempt to reset the accounts often.
Table of Contents
Azure VM Connectivity Issues
To be honest, the issue is not with Azure VM, rather there are many things involved when you connect to Azure VM via RDP. When I attempted to RDP a VM in Azure with my AAD credentials, I saw the login attempt failed error. Initially, I thought I was entering wrong information on the login screen.
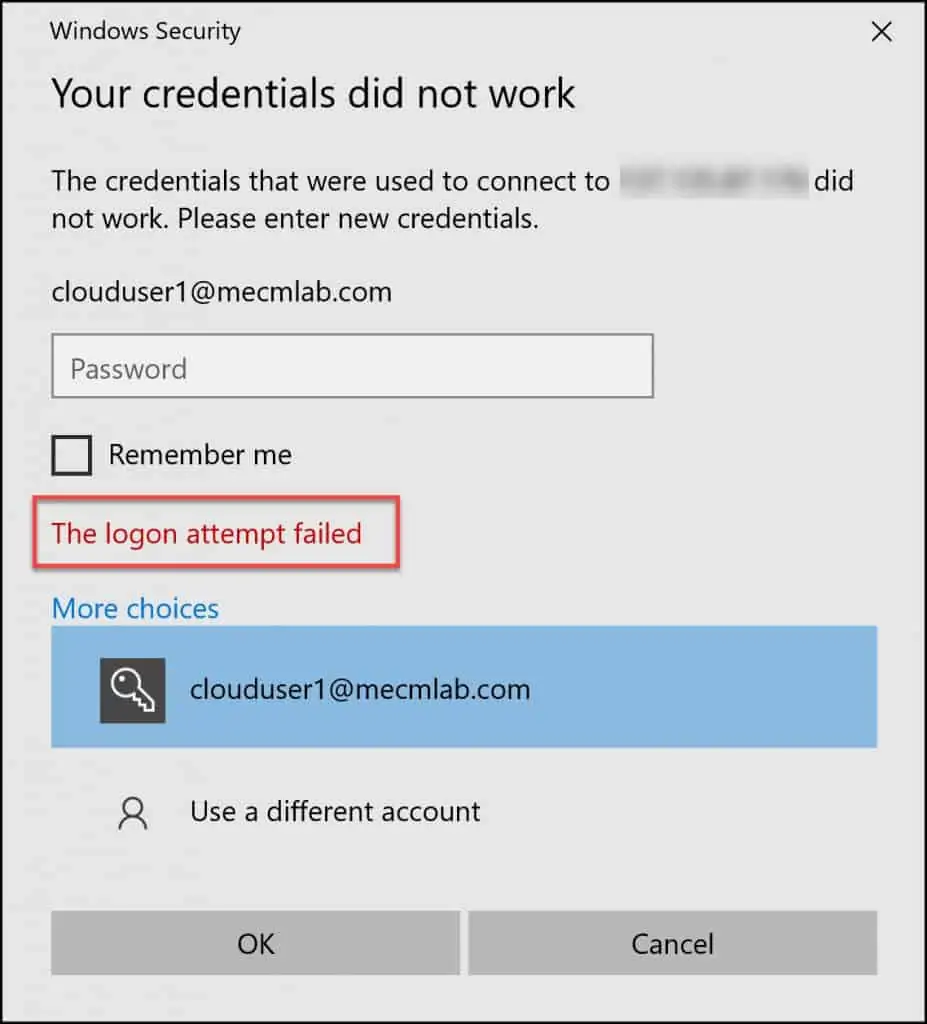
Some of you may also see Your credentials did not work error. It is so confusing and definitely not a good thing to see when you want to RDP into VM quickly.
Troubleshooting the Azure VM RDP issue involves many steps but don’t worry, I have covered all of them in this article for you. I have written it in a way that is easier to understand and follow the steps. If you have questions, feel free to contact me and I will be happy to respond.
The Remote Desktop Protocol (RDP) connection to your Windows-based Azure virtual machine (VM) can fail for various reasons, leaving you unable to access your VM. The issue could be with the Azure VM, or it could be with the configuration in Azure.
Most of us are not aware of the configuration that is essential before you RDP VM with Azure AD credentials. If these configurations are not in-place, you will struggle with accessing the VM.
When you cannot RDP Azure VM using Azure AD credentials, there is no single solution to this issue. Rather, there are certain steps that you need to follow to ensure you can successfully RDP to the Azure VM. For more information, refer to troubleshooting Remote Desktop connections to an Azure virtual machine.
Fix Unable to RDP VM using Azure AD Credentials Issues
As mentioned earlier, I will cover the troubleshooting steps to resolve the common issue unable to RDP Azure VM using Azure AD credentials. If you want to RDP Azure VM, you need to ensure the required settings are in place.
Suppose that you are connecting with Remote Desktop (RDP) to an Azure AD joined computer with a user account. The connection we want to establish is to an Azure AD joined computer, logging on with an account from Azure AD.
Check Network Requirements
To enable Azure AD authentication for your Windows VMs in Azure, you need to ensure your VMs network configuration permits outbound access to the following endpoints over TCP port 443:
For Azure Global
- https://enterpriseregistration.windows.net – For device registration.
- http://169.254.169.254 – Azure Instance Metadata Service endpoint.
- https://login.microsoftonline.com – For authentication flows.
- https://pas.windows.net – For Azure RBAC flows.
For Azure Government
- https://enterpriseregistration.microsoftonline.us – For device registration.
- http://169.254.169.254 – Azure Instance Metadata Service.
- https://login.microsoftonline.us – For authentication flows.
- https://pasff.usgovcloudapi.net – For Azure RBAC flows.
Step 1 – Enable Azure AD login for Windows VM
Few years ago, Microsoft announced Azure AD authentication to Windows Virtual Machines (VMs) in Azure giving you the ability to manage and control who can access a VM.
The Azure AD login for Windows VM in Azure needs to be manually enabled. You can enable this option while creating a new Virtual Machine in Azure. With this option enabled you can use your corporate AD credentials to log in to Windows VMs in Azure.
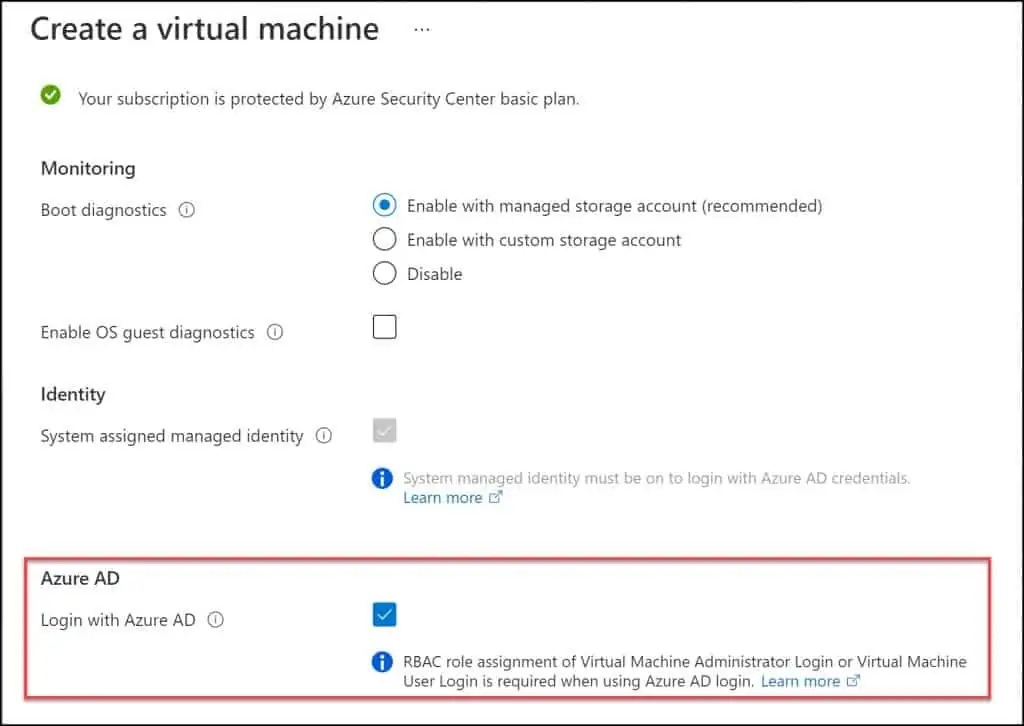
If you are creating a new VM in Azure and you want to log in using Azure AD credentials, you must enable the Login with Azure AD option.
There are two ways to enable Azure AD login for a VM in Azure:
- You can enable in Azure Portal while creating a VM.
- You can also use the Azure Cloud Shell experience when creating a Windows VM or on an existing Windows VM.
In the Azure portal, on the Create a Virtual machine window, select Management and under Azure AD, select Login with Azure AD. With this option enabled, you can log in to the VM using the Azure AD credentials.
Step 2 – Configure RBAC Role Assignment for Azure AD login
After you enable the login with Azure option in step 1, the next step is important before you RDP VM using Azure AD credentials. To log in to the VM using your Azure AD credential, you will first need to configure role assignments for the VM. You cannot skip this step as it is an essential step.
You must configure Azure role assignments for users who are authorized to log in to the VM. The RBAC role assignment of Virtual Machine Administrator Login or Virtual Machine User Login is required when using Azure AD login.
There are two Azure roles used to authorize VM login. Each of these roles are unique, and you can assign either of these two roles for the users.
- Virtual Machine Administrator Login: Users assigned with this role can log in to an Azure virtual machine with administrator privileges.
- Virtual Machine User Login: Users assigned with this role can log in to an Azure virtual machine with regular user privileges.
To configure RBAC Role assignments for Azure AD login, you can either use the Azure portal or Azure cloud shell. I haven’t used the Azure cloud shell much, and therefore, I prefer to use the Azure portal because it’s easy to use.
Let’s configure RBAC Role assignments for Azure AD login. In the Azure portal, go to Resource Groups and select your resource group. Select Access Control (IAM) and click Add > Add Role Assignment.
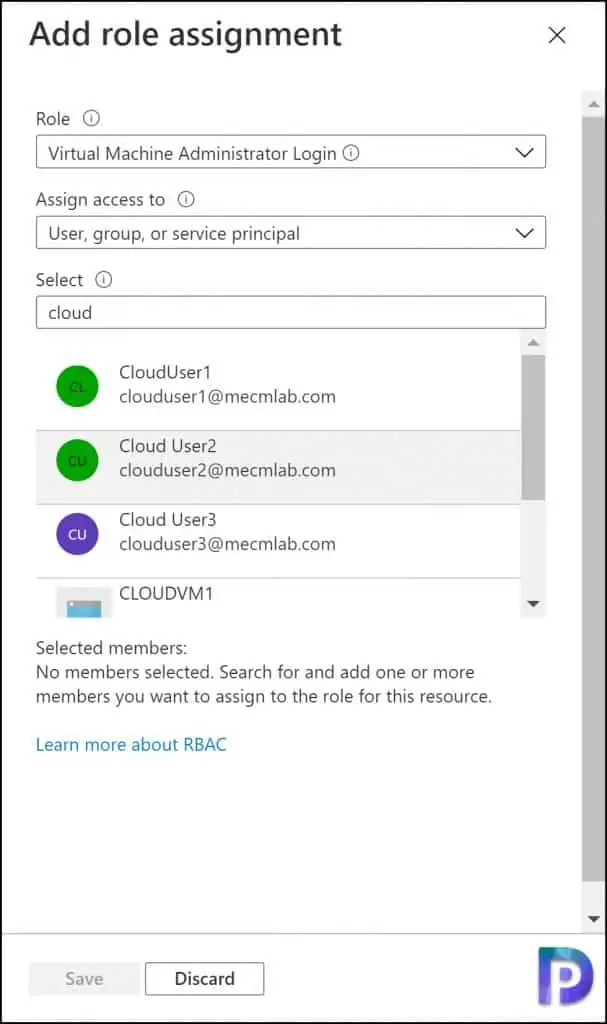
On the Add role assignment window, select the following.
- Role: Select either Virtual Machine Administrator Login or Virtual Machine User Login role.
- Assign access to: Select User, group or service principal.
- In the Select box, type the username and select the users and click Save.
Monitor the notifications where you can confirm the users were added to the selected roles.
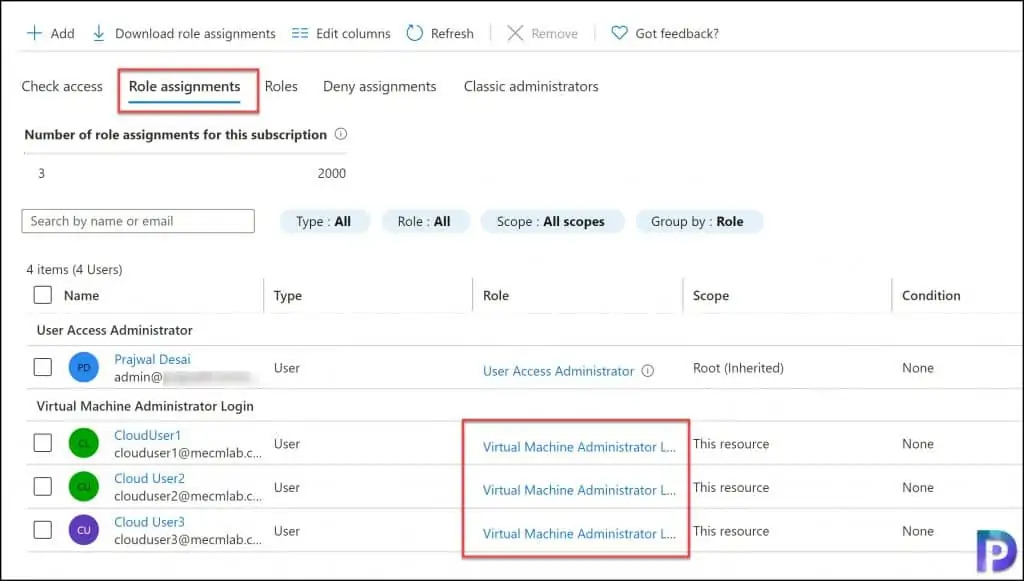
You can verify the RBAC role assignments are actually applied. In the Azure portal, click the Role assignments tab, and you should be able to see the assignments that you just configured in the above step. I have got three users, and they are now assigned to Virtual Machine Administrator Login role.
Step 3 – Verify AADLoginForWindows Extension in Azure
The AADLoginForWindows extension must install successfully in order for the VM to complete the Azure AD join process. This is a critical step to troubleshoot if you are unable to RDP Azure VM using AAD credentials.
If the AADLoginForWindows extension fails to install, you must always make a note of the exit code. The failed AADLoginForWindows extension should have the following exit codes.
- AADLoginForWindows extension fails to install with terminal error code ‘1007’ and exit code: -2145648574.
- AADLoginForWindows extension fails to install with Exit code: -2145648607
- AADLoginForWindows extension fails to install with Exit code: 51
Each of these exit codes have a unique solution. You can refer to this excellent AADLoginForWindows extension troubleshooting guide by Microsoft to resolve deployment issues.
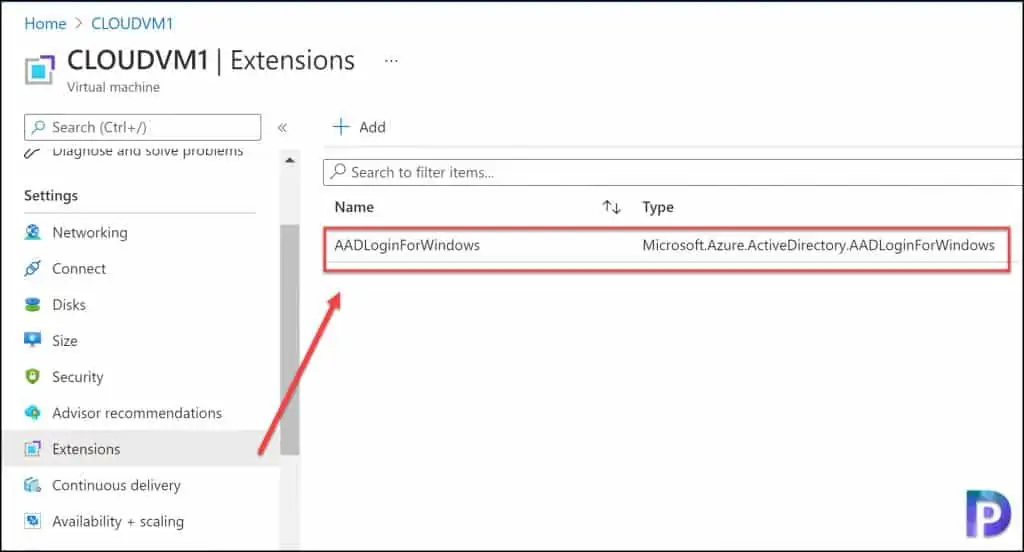
Now, I am going to show you the location of AADLoginForWindows extension. In the Azure portal, select the Virtual Machine and under Settings, click Extensions. Here you should see the AADLoginForWindows extension. The status of this extension must be Provisioning succeeded.
Step 4 – Unauthorized Client – The login attempt failed
From the Azure portal, when you download the RDP connection and attempt to connect, you may encounter Unauthorized Client The login attempt failed. This is the first error that you see when you RDP Azure VM using Azure AD Credentials.
This may seem stupid, but every so often we enter wrong credentials and try to find out why the login is not working. When you RDP VM using Azure AD credentials, ensure you are using the correct credentials. You may also reset the password and try logging in.
As per Microsoft, you must verify that the Windows 10 PC you are using to initiate the remote desktop connection is one that is either Azure AD joined, or hybrid Azure AD joined. Note that per-user enabled/Enforced Azure AD Multi-Factor Authentication is not supported for VM Sign-In. This setting causes Sign-in to fail with “Your credentials do not work” error.
Step 5 – Ensure VM is joined to Azure AD Tenant
When you are unable to RDP Azure VM using AAD credentials, ensure the Windows 10/Windows 11 VM in Azure is joined to Azure AD tenant. I have a post that details the steps to join Windows 10 VM to Azure AD. You can use those steps to verify if the VM is Azure AD joined.
You may have a question that when you are unable to RDP Azure VM, how can you log in? In this case, you have to log in using the local administrator account or the account that you set up while creating VM in Azure. If you are not sure about the password, contact the Azure administrator.
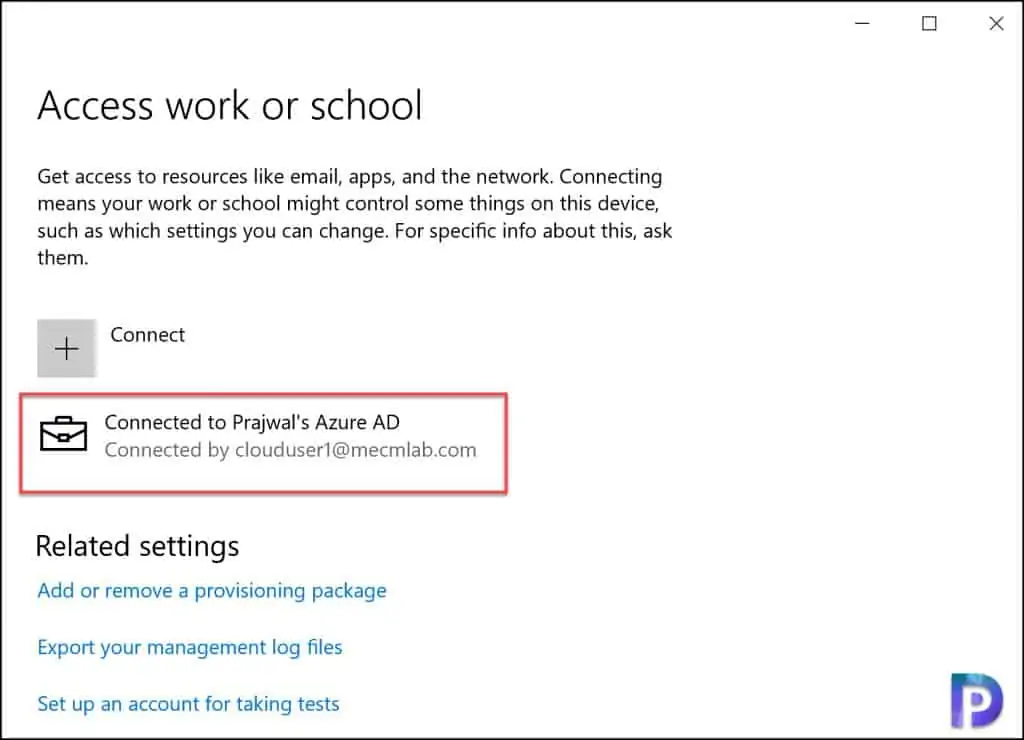
To find whether your computer or VM is Azure AD joined or not, log in to Azure VM, open Settings, and then select Accounts. Select Access work or school. If you see connect to organization Azure AD, it means your computers is joined to Azure AD.
Step 6 – Disable Network Level Authentication
The network level authentication can sometimes restrict you to RDP Azure VM using Azure AD credentials. You can disable network level authentication on your Azure VM.
Microsoft recommends keeping the network level authentication turned on. However, this step becomes mandatory if you cannot RDP to Azure VM doesn’t work.
Use the local account to sign in to the Azure VM and perform the below steps.
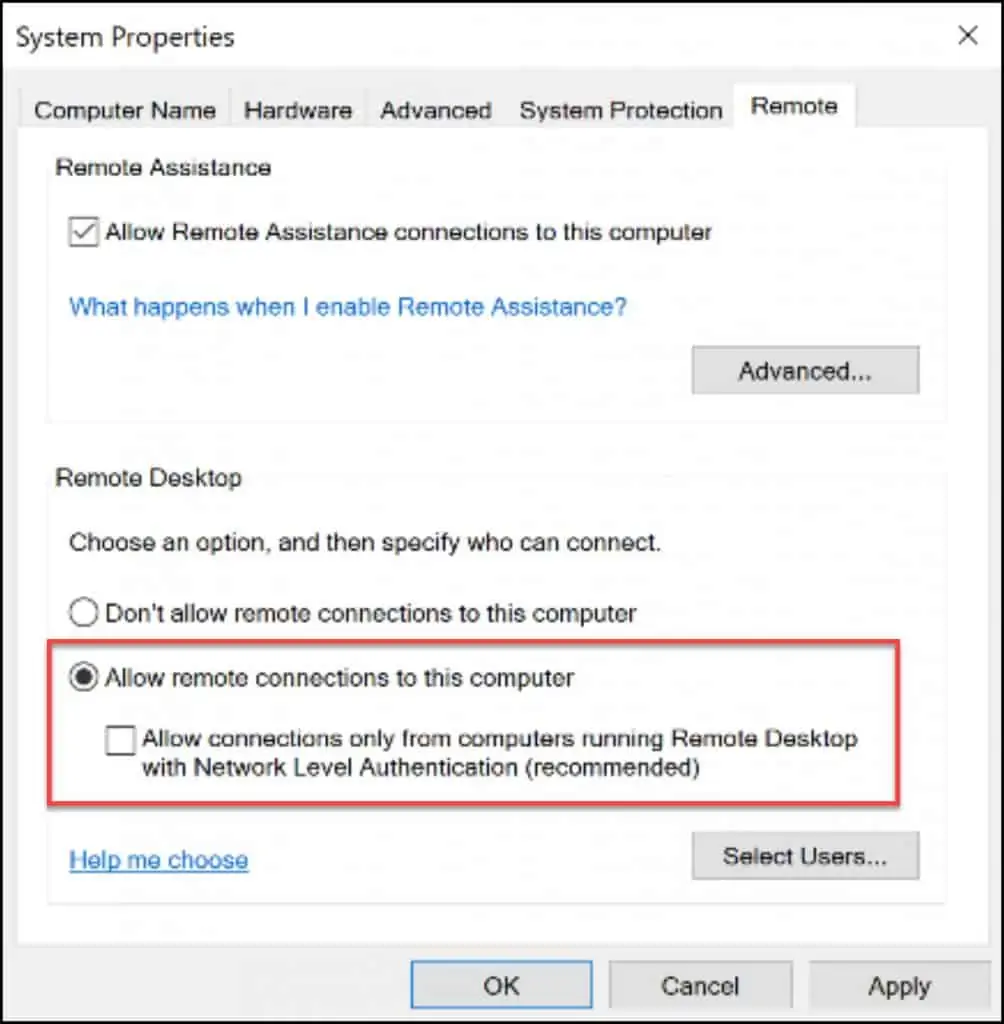
On your Windows 10 Azure VM, under the System Properties, select Remote tab. Under Remote Desktop, select Allow remote connections to this computer. Untick Allow connections only from computers running Remote Desktop with Network Level Authentication. Click Apply and OK.
Step 7 – Add Azure AD user to the Remote Desktop Users Group
In order to successfully RDP VM using Azure AD credentials, you must add Azure AD user to the remote desktop users group on the VM.
Use the local account to sign in to the Azure VM and perform the below steps. You should have the user account ready to provide the access to the Azure VM.
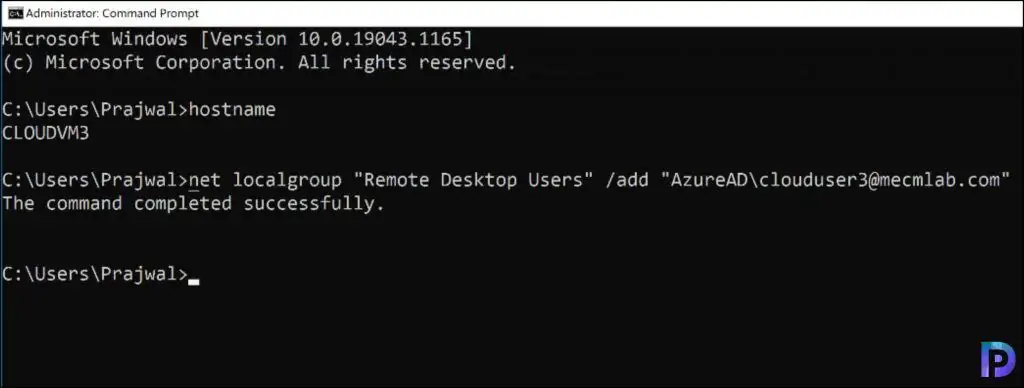
To add the Azure AD user to remote desktop users group on the Azure VM, run the below command. Replace the UPN attribute with the Azure AD user. The account should be in AzureAD\USERNAME@DOMAIN.onmicrosoft.com format.
net localgroup "Remote Desktop Users" /add "AzureAD\the-UPN-attribute-of-your-user"
Run the command prompt as administrator and enter the above command. You should see the command executed successfully message.
You can confirm if the Azure AD user has been added to the VM by running the below PowerShell command.
Get-LocalGroupMember -Name "Remote Desktop users"
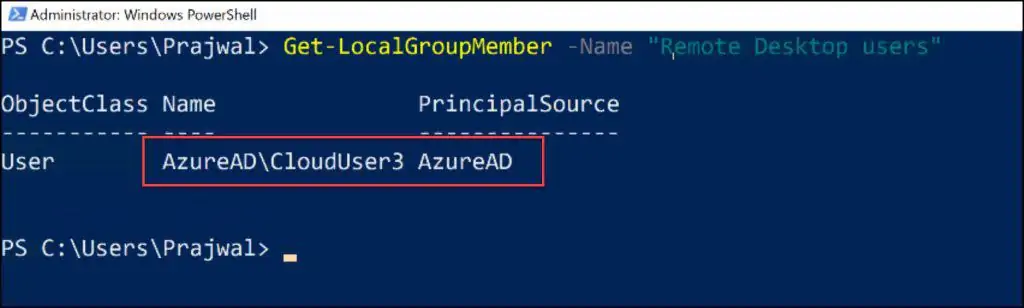
As you can see, we have successfully added the Azure AD user to the Remote Desktop Users Group. The Principal Source is Azure AD.
Step 8 – Modify the Azure VM RDP File
The last step before we test the RDP to Azure VM is to modify the Azure VM RDP file and add few lines to it. Navigate to the overview page of the virtual machine that has been enabled with Azure AD logon. Select Connect to open the Connect to virtual machine blade. Click Download RDP File.
Right-click the Azure VM RDP and open it with Notepad. You can use any other text editor as well. Since Notepad comes installed with Windows 10, it does the job. In the notepad, append the below data.
enablecredsspsupport:i:0
authentication level:i:2
So, the final RDP file data should look something like below screenshot. Save the file after you make the changes.
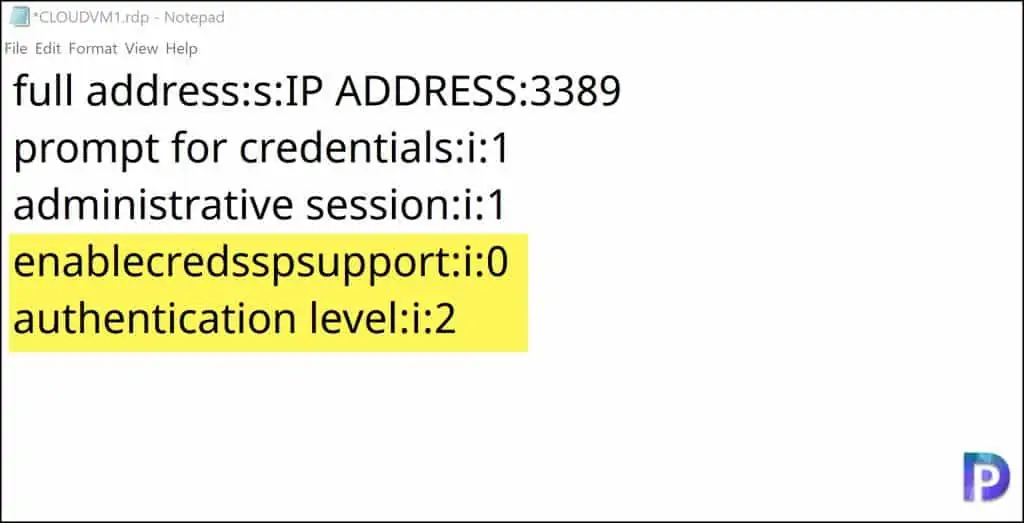
When you RDP an Azure VM, it usually prompts the user to enter the credentials. There is a way to bypass this by entering the account details within the RDP file. Let me show you how and explain the other details.
full address:s:IPADDRESS:3389 prompt for credentials:i:0 authentication level:i:2 enablecredsspsupport:i:0 username:s:USERNAME@DOMAIN.onmicrosoft.com domain:s:AzureAD
- Full Address: This is the IP address of your Azure VM. The 3389 is the Remote Desktop Protocol port.
- Prompt for credentials: Defines if you should enter credentials before you enter your session. Setting the value to 1 will prompt for credentials and value 0 will not prompt for credentials.
- Authentication level: You define the server authentication level settings here. The value 2 means if the server authentication fails, show a warning and allow connecting or refuse the connection.
- Enablecredsspsupport: This setting determines whether RDP will use the Credential Security Support Provider (CredSSP) for authentication if it is available. If you set the value to 0, RDP will not use CredSSP, even if the operating system supports CredSSP
- Username: You can specify the Azure AD user account name
- Domain: Specify AzureAD as the domain name.
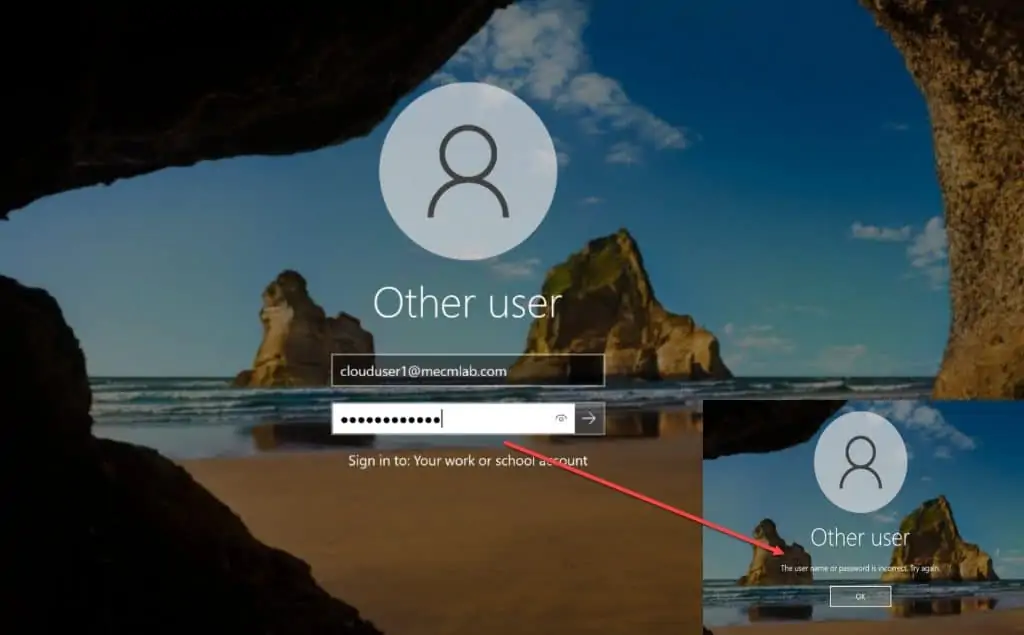
After you have performed all the steps, let’s check if we can RDP VM using Azure AD credentials now. Double-click the Azure VM RDP file and enter the credentials.
I want to cover something important here. After following all the steps, some of us will still ignore this simple fact. If you are entering only the Azure AD user account without the domain on the login screen, you will never RDP into the VM. You will see The username or password is incorrect. Try again message.
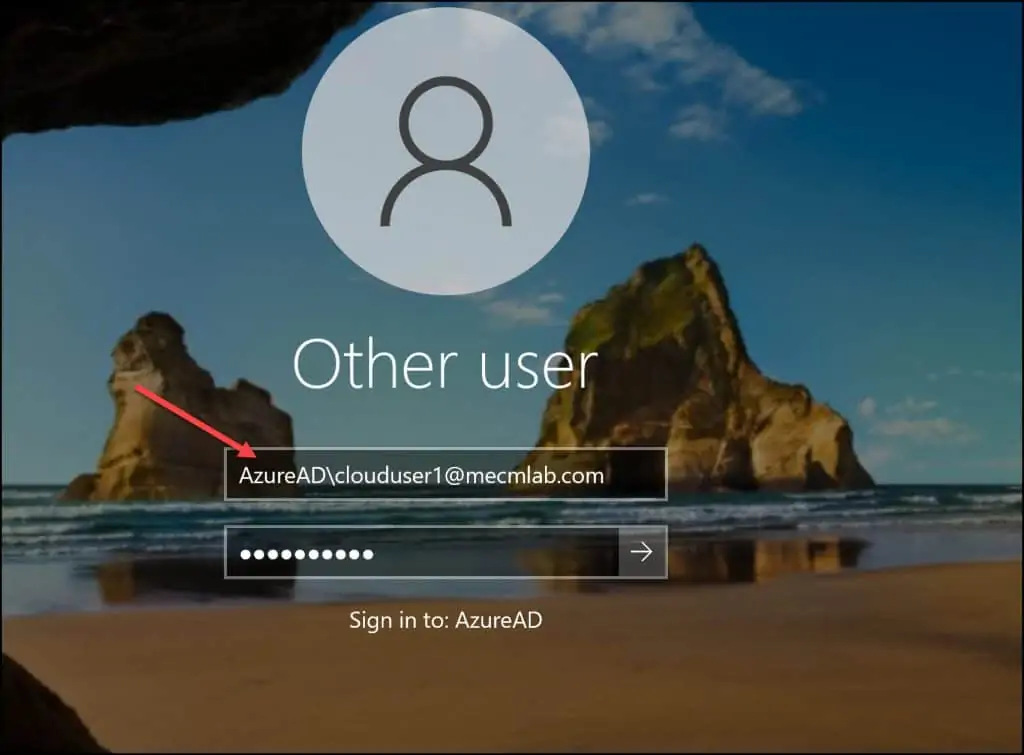
The correct way to log in to Azure VM is by prefixing the AzureAD as domain. You must enter the username as AzureAD\username@domain.onmicrosoft.com. Now you should be able to log in to the Azure VM.

I am just getting started with Azure and got my free subscription and setup a server 2019 vm, followed the official doc and all the steps here..Ie: ticking the Azure AD, Assigning VM admin role assignment, checking extension, Disabling NLA, Adding user to the Remote desktop users group, Disabling firewall in VM, Updating RDP shortcut with the 2 lines, putting in AzureAD\UPN for login, Disabling the AD security defaults. I still get the error “The sign in method you are trying to use isn’t allowed, try a different signin method or contact system administrator”
This is so frustrating, i thought this would be the easiest thing on Azure..How does everyone else manage their servers on Azure ? thought there would be more info out there regarding this..
Hi Projwal – Are you able to comment on this setup please:
– AAD Joined PCs at the office, no local AD, no Azure VMs
– Separate VPN solution allows remote connection to the office
– RDP to AAD joined PC – used to work from an AAD-Registered personal PC – I think when NLA was disabled on the office PC.
– MFA is enabled on the AAD User account, no conditional access policies.
I replaced my office PC – and now it seems I can only RDP to the AAD-joined PC from another AAD-Joined PC, where I am asked for my PIN only to authenticate, not any MFA etc. Is this NLA kicking in?
Is it possible to connect with NLA required on the remote, but the client is not AAD-Joined (only registered)?
I couldn’t find out much about how NLA works, especially with AAD-Join, but I feel like I should leave it on for security.
Also any knowledge of the enablerdsaadauth:i:1 setting? If I enable this on my aad-registered device I go through MFA but then get error CAA20002 which from searching seems like an authentication issue, but no results specific to RDS.
Thanks
Is this process being similar for Win Server 2019? Can I do same steps for win 2019 server so that Azure AD user can login to the server?
Thank you for the detailed description.
Has anyone already solved the problem that username and password can not be sent via copy&paste to the VM’s login screen?
Especially if you run many VMs it is very time consuming to enter your password manually again and again.
kind regards
Few things can be added to the RDP file.
Thanks again.
Could not find RDP file settings to achieve a ‘Copy and Paste’ functionality to the login screen so far.
If someone has an idea then do not hesitate to tell me 🙂
You Should add a step / information regarding multi-factor authentication. MFA interferes with login. I just disabled MFA on my test user and successfully logged in afterward. My test user still belongs to a Conditional Access Policy that enables MFA. For the moment that does not seem to interfere. I have yet to verify that MFA is functioning for the test user at all. I try to come back and report my findings.
Excellent question, currently Microsoft don’t have any solution apart from excluding the Azure VM sign-in in MFA conditional policy. But we need to find a way so that MFA also work with it.
Thank you Prajwal for the detail explanation and waiting for your reply on MFA.
Just wanted to share an improvement:
Arriving at the vm login or lock screen was not practical for me because you are not allowed to paste the password which can be drag.
If you update the RDP file with the VM-LOCALLY ACTIVE name of the user account, you can just authenticate (and paste) locally and you will just end up _in_ your VM, not at the front door.
In my case, after using ‘whomai’ in Powershell, I updated in the rdp file from:
domain:s:AzureAD
username:s:name@domain.tld
to
domain:s:AzureAD
username:s:namedomain
Note that the .tld is gone as well as the @ sign, but we shouldn’t assume universal logic.
The notation whomai returned was:
azuread\namedomain
I also had to use:
enablecredsspsupport:i:1
and I temporary enabled:
prompt for credentials:i:1
After that I saved my credentials in my local windows credential store and I can now just login the VM without being force to type a password.
P.s. It is a bit much this all requires this many steps, anyhow I am grateful for your post! Before, I couldn’t get in at all. After I could get in with some hoops. Now, I double click rdp file.
Thank you, Thank you , Thank you
after a lot of pain, your simple guide was exactly what I needed to get this working – including adding the AzureAD domain prefix
Hi Prajwal, thanks for the above steps, I tried everything but getting “The sign-in method is not allowed please contact your administrator” error, any inputs will be greatly appreciated.
Thanks
Lakshay
Hi, if you have MFA enabled/enforced, you will have to set up a conditional access policy.
Cody, would you mind going into more detail on what the policy is doing? Is it about bypassing MFA for the Virtual Machine logins or what? Prajwal, maybe you can test this and add this info to the document? That would be valuable and seems to be missing from your otherwise comprehensive write-up here.
I done all the steps but i am getting logon attempt failed. Can u please help me?