Enable/Disable Remote Desktop Access using Intune
In this article, you’ll learn how to enable or disable remote desktop access using Intune on Windows devices. When you disable remote desktop connections using Intune, you prevent users from connecting to the machine using the remote desktop protocol.
When you allow remote connections to your PC, you can use another device to connect to your PC and have access to all of your apps, files, and network resources as if you were sitting at your desk. If you block the RDP connections, no one can access your PC remotely.
Ideally, you allow remote desktop connections on a computer to connect and control the computer from another device. This setting is found on the Remote tab in the System properties sheet.
Intune’s configuration policies help you lock down Windows devices as per your organization’s security requirements. The policy setting Allow users to connect remotely by using Remote Desktop Services in Intune can help you enable or disable remote desktop access.
This policy setting allows you to configure remote access to computers by using Remote Desktop Services. When this policy is disabled, users are unable to establish remote connections to the target computer through Remote Desktop Services.
Caution: When you deploy an Intune Configuration profile to disable remote desktop access, it removes the ability to RDP the machine remotely. So be careful while applying this policy to virtual machines running in Azure.
Useful Guide: Disable access to Control Panel and PC settings using Intune
Reasons to Disable remote desktop connections using Intune
Listed below are some valid reasons why organizations prefer Microsoft Intune to disable remote desktop access on Windows 10/11 devices:
- Disabling RDP (Remote Desktop Protocol) access through Intune offers several key benefits. Firstly, it helps prevent unauthorized individuals from gaining remote access to your organization’s systems. This is particularly important for sensitive data and critical infrastructure that could be compromised if left vulnerable.
- Disabling RDP connections minimizes the risk of brute-force attacks or password-guessing attempts by malicious actors. By implementing this security measure, you significantly reduce the chances of unauthorized users gaining control over your network.
- Enabling RDP can also become the gateway where a malware infection or targeted ransomware is deployed, resulting in critical service disruption.
- Disabling remote desktop connections adds an extra layer of protection against potential vulnerabilities or exploits that may exist within the RDP protocol itself. Cybercriminals may use these vulnerabilities to launch malicious attacks or gain unauthorized access to systems.
Some organizations prefer to disable remote desktop access completely on servers and even on workstations. The goal is to prevent malicious users from accessing the computer remotely via RDP.
Also Read: How to block registry access using Intune
Disable Remote Desktop Access using Intune
To manage the remote desktop connection on Windows devices managed by Intune, you can create a device configuration profile using the following steps:
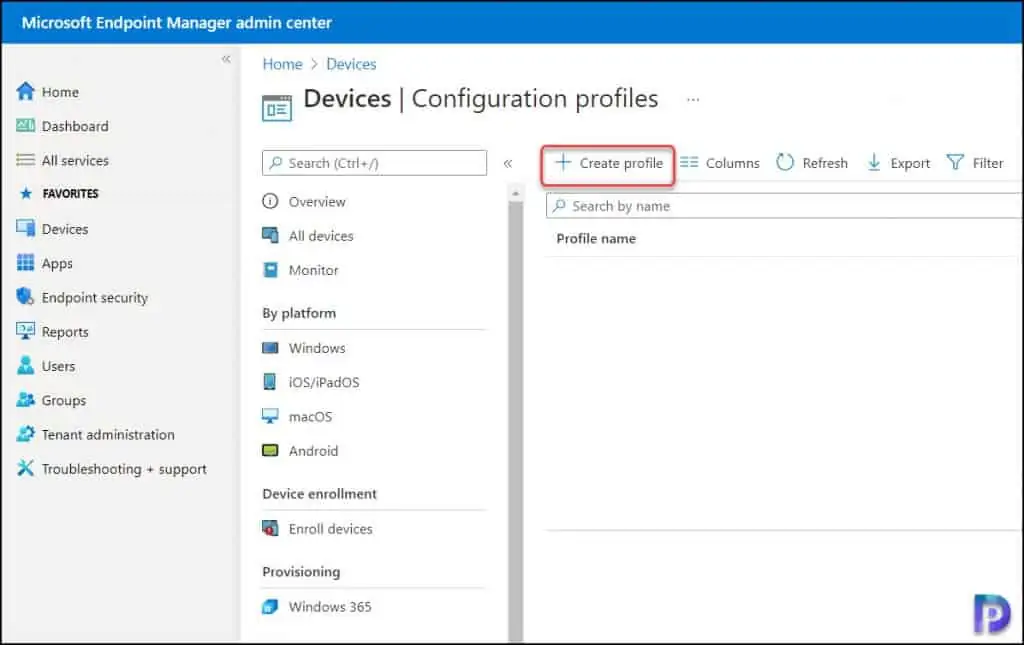
- Sign in to the Microsoft Intune admin center.
- Go to Devices > Configuration Profiles.
- Click on Create > New Policy to create a configuration policy to disable remote desktop connections.
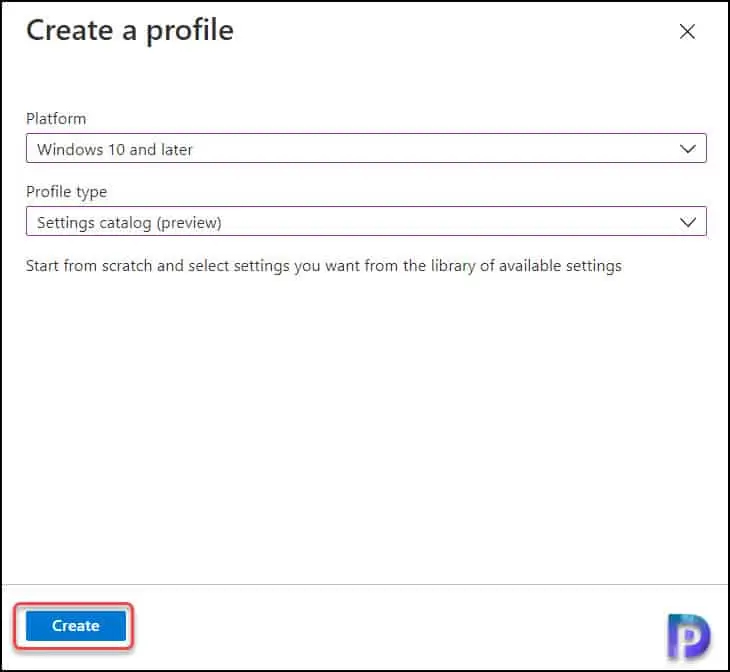
On the Create a profile window, select the ‘Platform‘ as ‘Windows 10 and later‘. Now select ‘Profile type‘ as ‘Settings Catalog‘. Click Create.
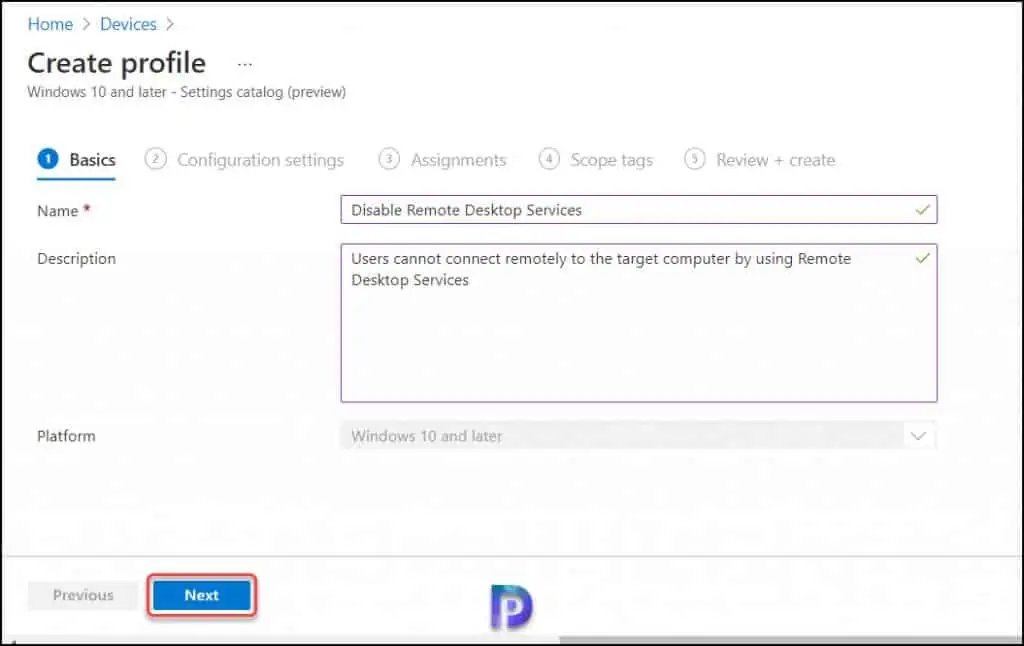
Specify the profile name as Disable Remote Desktop Access or Disable Remote Desktop Connections, and click Next.
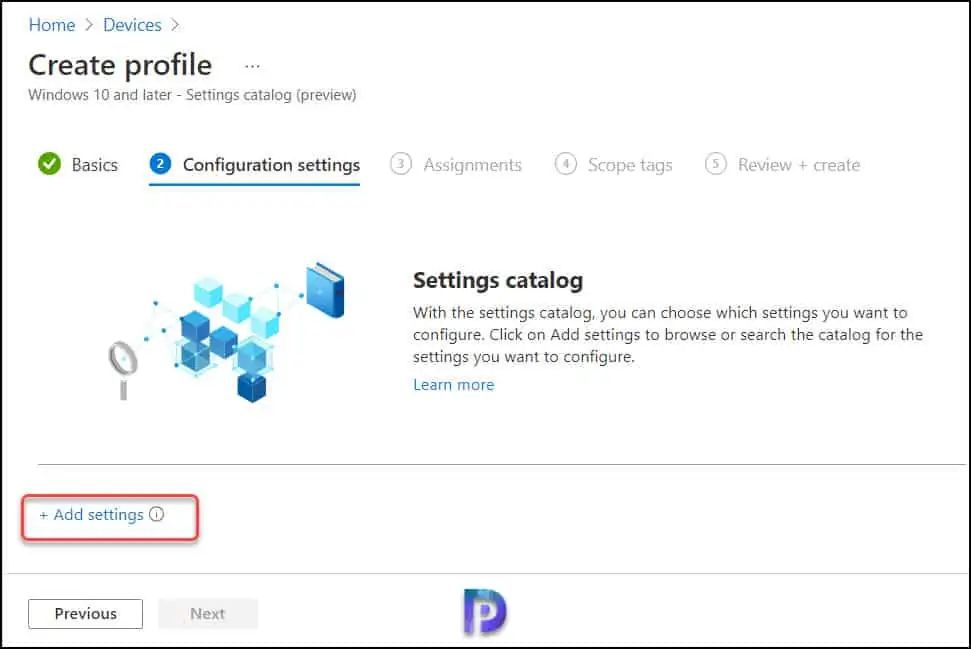
In the Configuration Settings window, we will use the Intune Settings catalog to configure the settings for remote desktop access. Select Add Settings.
On the Settings Picker window, type ‘remote desktop services‘ in the search box and click Search. From the list of results, select Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Connections.
Under Settings, select Allow users to connect remotely by using Remote Desktop Services.
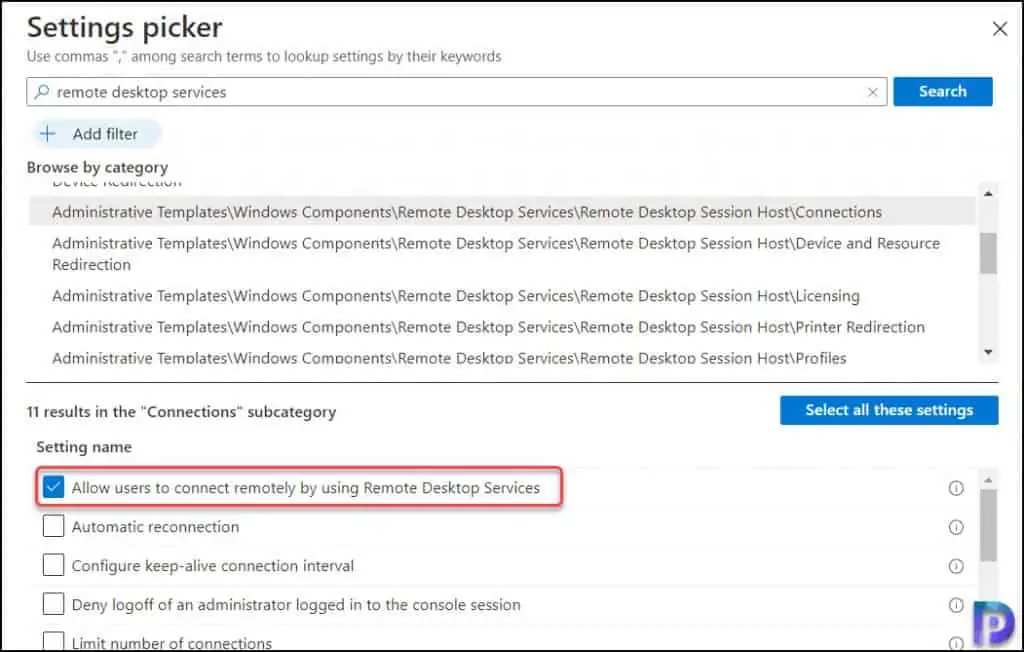
Allow users to connect remotely by using Remote Desktop Services
According to Microsoft, the description of the policy setting “Allow users to connect remotely by using Remote Desktop Services” is as follows:
- This policy setting allows you to configure remote access to computers by using Remote Desktop Services.
- If you enable this policy setting, users who are members of the Remote Desktop Users group on the target computer can connect remotely to the target computer by using Remote Desktop Services.
- If you disable this policy setting, users cannot connect remotely to the target computer by using Remote Desktop Services. The target computer will maintain any current connections but will not accept any new incoming connections.
- If you do not configure this policy setting, Remote Desktop Services uses the Remote Desktop setting on the target computer to determine whether the remote connection is allowed.
If you want to disable remote desktop access, configure the policy setting “Allow users to connect remotely by using Remote Desktop Services” to “Disabled.”
If you want to enable remote desktop access, configure the policy setting “Allow users to connect remotely by using Remote Desktop Services” to “Enabled.”
Click Next.
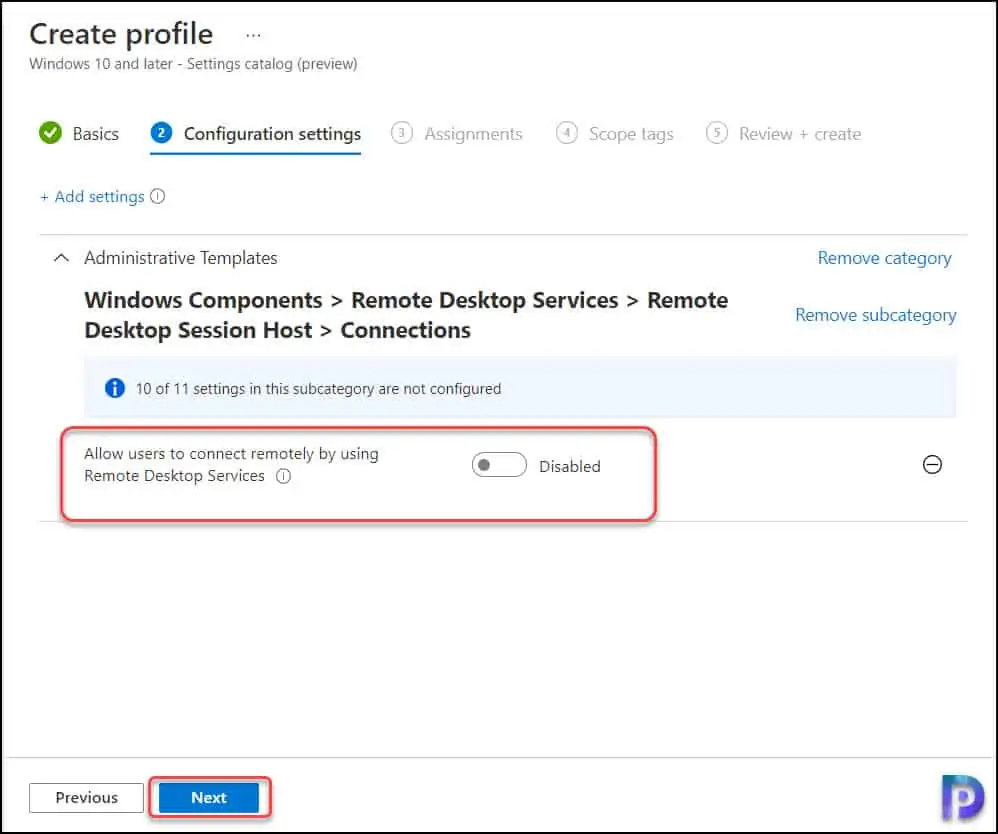
In the Assignments tab, select the Entra ID groups to apply this policy. Click Add groups and select the desired groups. Click Next.
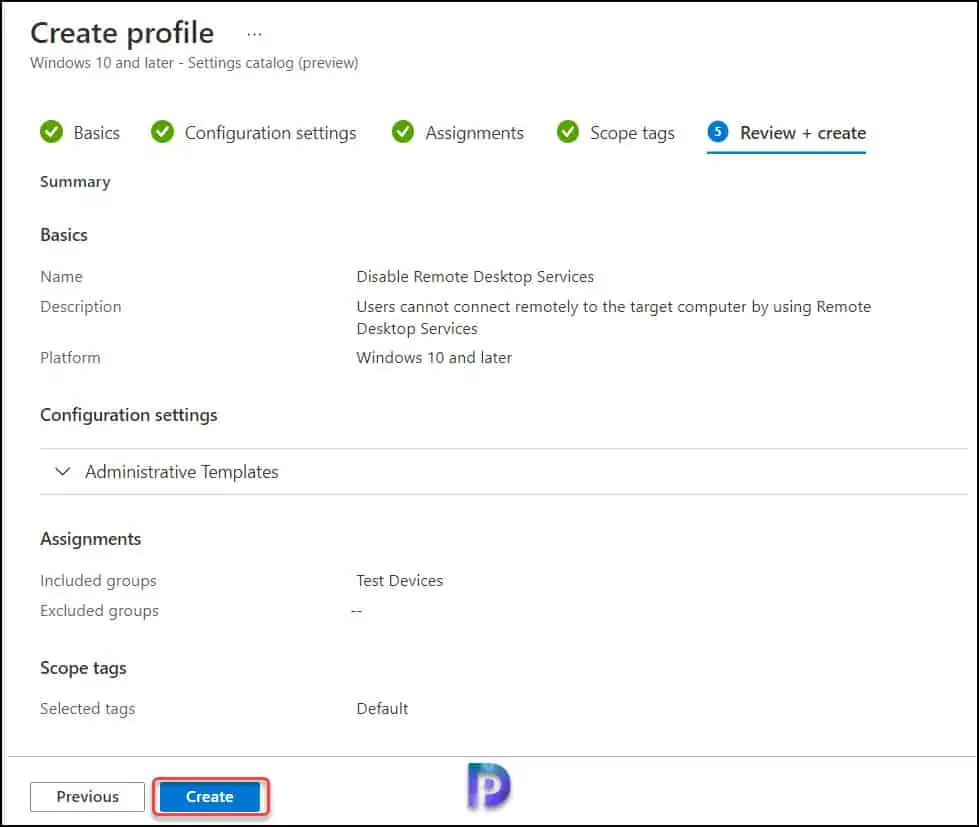
We will not configure the scope tags. Click Next.
On the Review+Create tab, verify all the settings, and click Create. A notification should appear confirming that the profile has been created successfully.
Monitor Policy in Intune
While the settings are being applied to Windows devices, you can monitor the newly created policy in Intune. In the Intune admin center, select the policy and review the Device and user check-in status. Under “Device and user check-in status,” you get to see the total number of devices and users who successfully received the policy settings. In some cases, the policy may fail to apply to certain users or devices. To resolve the issues, we recommend reviewing Intune logs on Windows computers.
Manually Sync Policies on Windows devices
When you assign a policy through Intune, it takes some time to apply it to the devices within the targeted groups. You can wait for the policy settings to apply, or to accelerate the sync, you can manually sync Intune policies on your Windows computers to sync with Intune. You can also use PowerShell to sync the Intune policies on Windows devices.
End-User Experience
On the Windows devices that have successfully received the policy settings, the remote desktop connection will be denied. When you try to RDP into a virtual machine or computer, it should refuse you, confirming that the Intune policy has successfully prevented RDP access.
Conclusion
In conclusion, disabling remote desktop connections using Intune is a crucial step in enhancing your organization’s cybersecurity posture. It helps mitigate risks associated with unauthorized access, brute-force attacks, and potential vulnerabilities within the RDP protocol itself. By prioritizing security measures like this one, you are actively protecting your network and valuable data from cyber threats in an increasingly interconnected world.

Great to see the new controls
Great