Enable Tenant Attach in ConfigMgr | SCCM Cloud Attach
This post is a step-by-step guide to enable tenant attach in ConfigMgr or SCCM. I will explain what SCCM tenant attach is, and we will look at the steps to configure the tenant attach in SCCM.
With SCCM tenant attach, you can now connect Configuration Manager devices to the cloud service and take action from the Devices blade in the Intune admin center. Putting Configuration Manager and Intune together in the Microsoft Intune admin center is a great idea.
What is SCCM Tenant Attach?
By definition, Tenant attach connects your Azure tenant to your on-premises SCCM environment, and then you view and manage devices directly from the Intune Admin Center.
With tenant attach, you can view data and perform basic administrative tasks in your SCCM environment. Co-management is not new and has been around for quite a while now. A co-managed device is basically managed by both ConfigMgr and Intune at the same time.
Tenant Attach means that ConfigMgr or Intune can manage the device. The reason we use the term “Tenant Attach” is because it is simply a way to attach your ConfigMgr hierarchy to your tenant. And once you’ve done that, you can complete several tasks, including synchronizing Azure AD groups from a device collection and discovering cloud users and groups.
Tenant attach vs co-management
Most people consider tenant attach and co-management as similar, but they aren’t. Co-management is a feature with which you can manage your devices with both SCCM and Microsoft Intune. You can switch the workloads from SCCM to Intune such as compliance policies, Windows Update policies etc. The advantage of co-management is it gives you a phased way to move from an on-premises management framework to the cloud.
Tenant attach SCCM uses co-management for its configuration, but it does not require devices to be enrolled into Intune or workloads to be switched from SCCM to Intune. Tenant attach extends simple management capabilities to the Intune admin center.
Benefits of using Tenant Attach
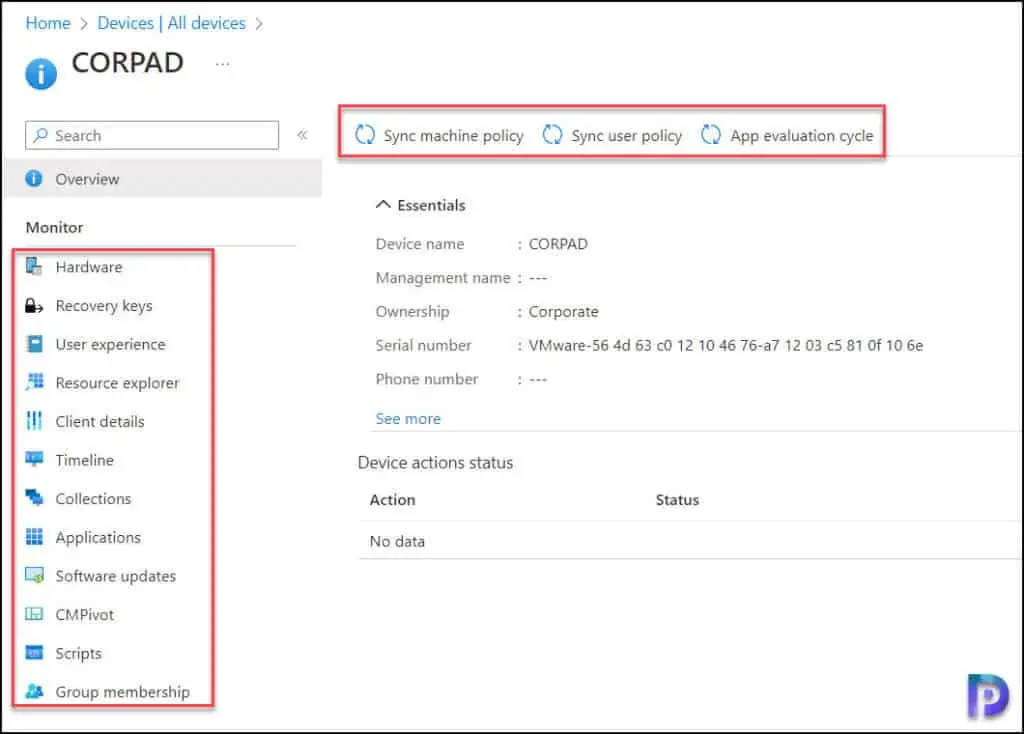
The IT admins can perform the following remote actions on tenant attached devices:
- Sync machine policy
- Sync user policy
- Trigger an app evaluation cycle
- Deploy applications, Software Updates
- Retrieve reports with the CMPivot query tool
- Run scripts on clients
Tenant Attach Prerequisites
To configure tenant attach, you need the following prerequisites:
- An account that is a Global Administrator for signing in when applying the onboarding change.
- You need Configuration Manager current branch version 2002 or later to enable tenant attach. Microsoft tenant attach was one of the exciting features of SCCM 2002.
- An Azure public cloud environment.
- The geographic location of the Azure tenant and the service connection point should be the same.
- At least one Intune license for you as the administrator to access the Microsoft Intune admin center.
ConfigMgr Tenant Attach Permissions
The user accounts performing device actions have the following prerequisites:
- The user account needs to be a synced user object in Azure AD (hybrid identity). This means that the user is synced to Azure Active Directory from Active Directory.
- For Configuration Manager version 2103, and later: Has been discovered with either Azure Active Directory user discovery or Active Directory user discovery.
- The Initiate Configuration Manager action permission under Remote tasks in the Microsoft Intune admin center.
- For more information about adding or verifying permissions in the admin center, see Role-based access control (RBAC) with Microsoft Intune.
Enable SCCM Cloud Attach
Use the following steps to enable cloud attach in the SCCM console:
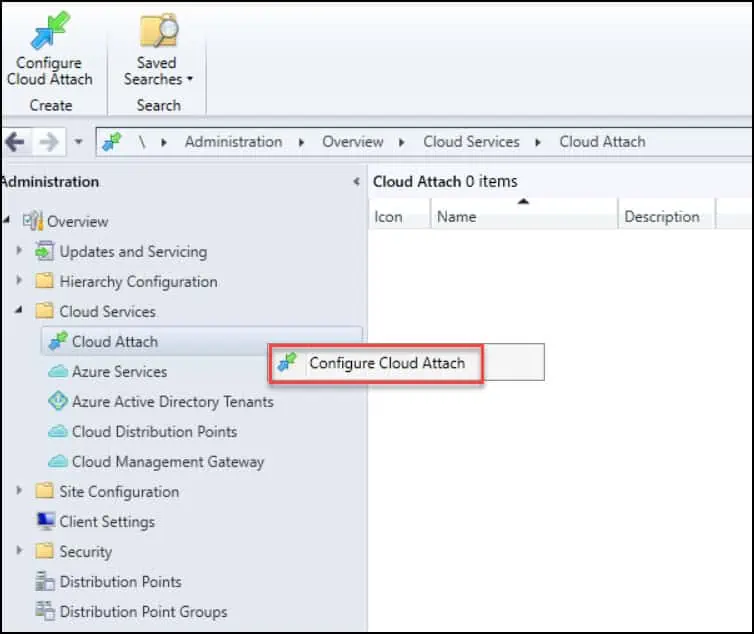
- In the ConfigMgr console, navigate to Administration > Cloud Services > Cloud Attach.
- Right-click Cloud Attach and select Configure Cloud Attach.
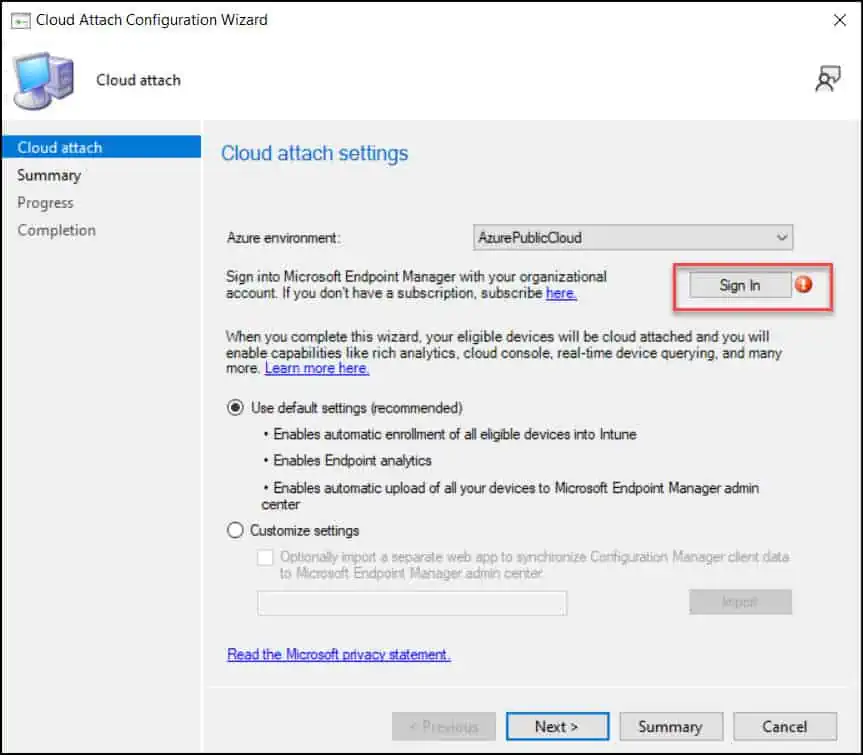
On the Cloud Attach tab, specify the cloud attach settings. First select the Azure environment and then click on Sign In. On the authentication window, sign in with your organizational account.
You can enable SCCM cloud attach with default settings or customize the settings. With default settings, the following points apply:
- Enables automatic enrollment of all eligible devices into Intune.
- Enables Endpoint Analytics.
- Enable automatic upload of all your devices for Microsoft Intune admin center.
Click Next.
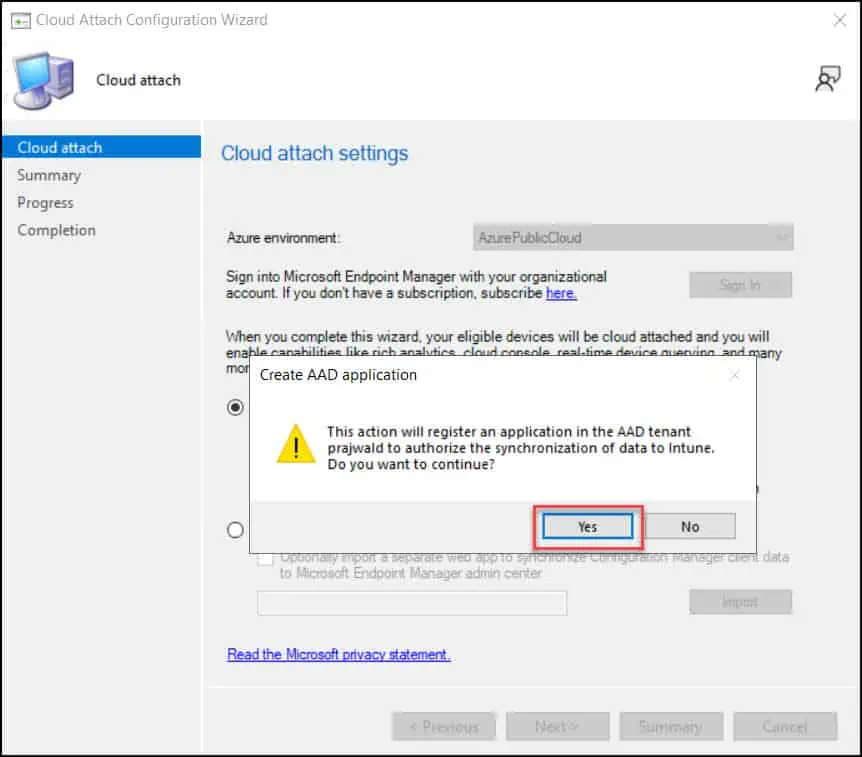
In this step, you will need to provide consent to create AAD application. Selecting Yes will register an application in the AAD tenant to authorize the synchronization of data to Intune.
Review the SCCM cloud attach settings on the Summary window and click Next.
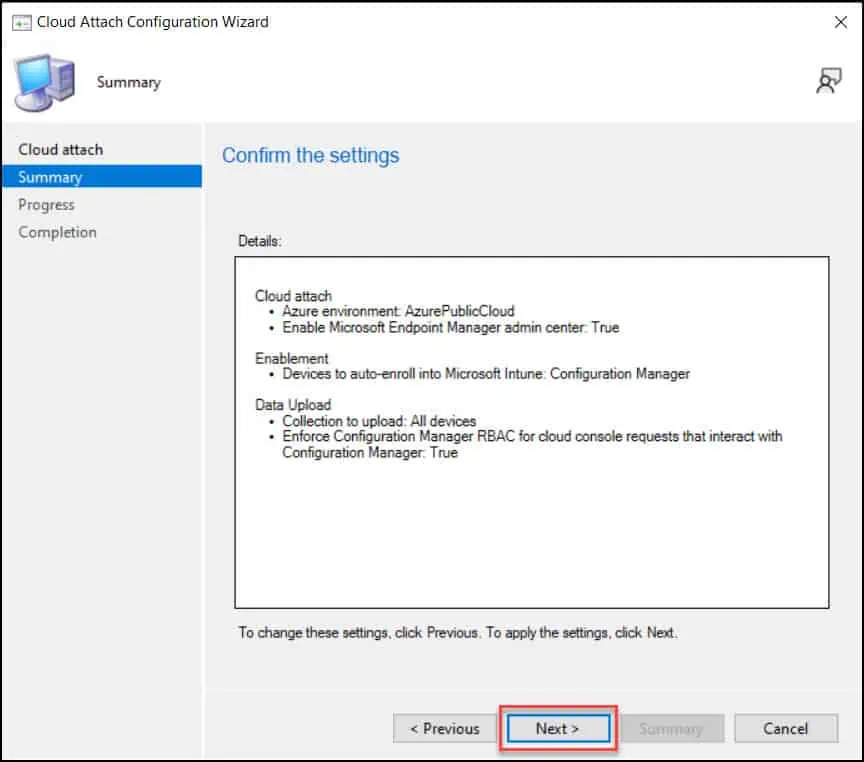
Close the Cloud Attach Configuration Wizard.
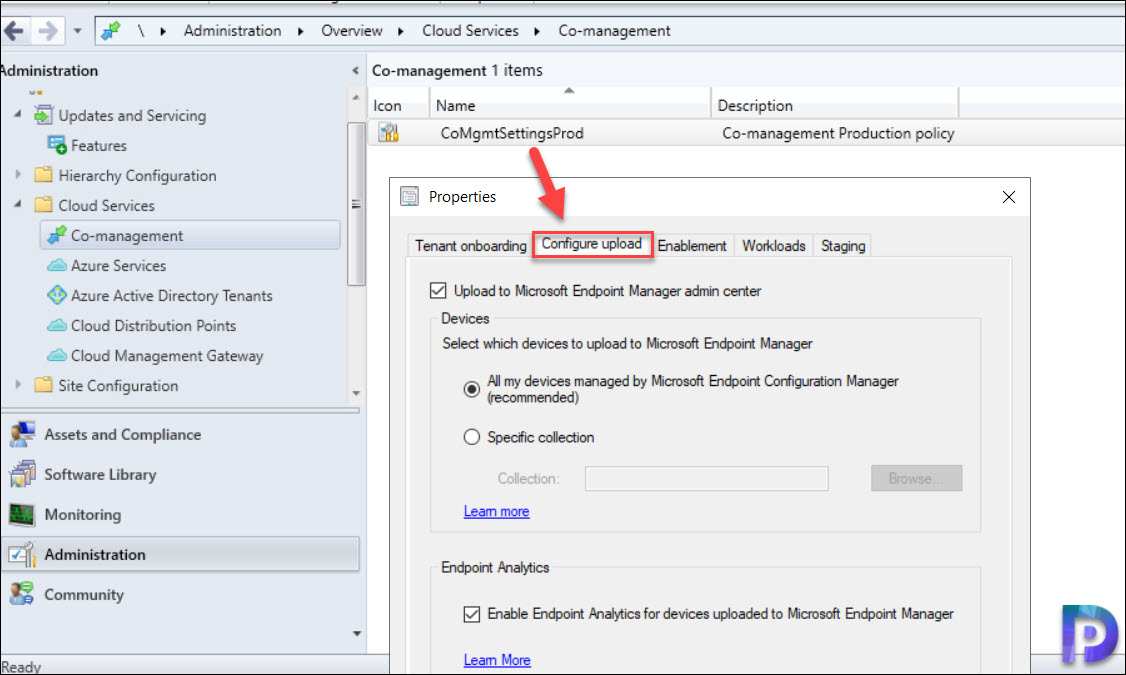
Enable device upload when co-management is already enabled
If you have already enabled co-management in your setup, you’ll use the co-management properties to enable device upload. If co-management isn’t already enabled, then jump to the next step. You use the Configure Co-Management Wizard to enable device upload instead.
Assuming co-management is already turned on, follow the steps below to change the co-management properties to allow device upload:
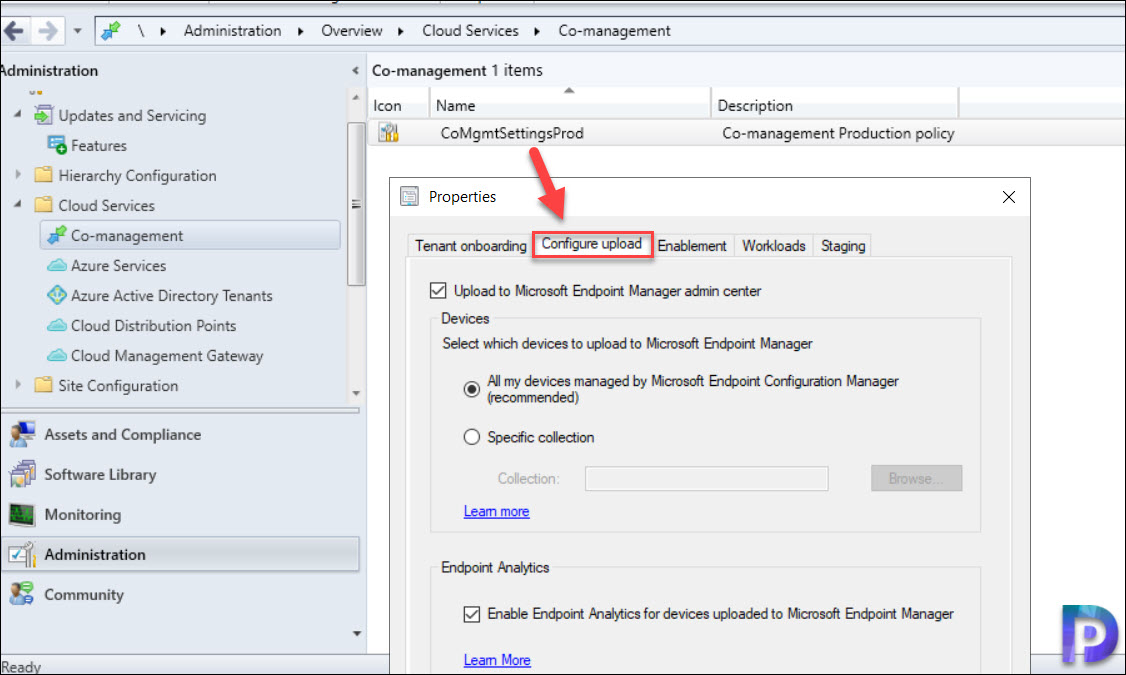
- In the Configuration Manager admin console, go to Administration > Overview > Cloud Services > Co-management.
- Right click CoMgmtSettingsProd and select Properties.
- In the Configure upload tab, select Upload to Microsoft Intune admin center. Select Apply. The default setting for device upload is All my devices managed by Microsoft Configuration Manager. If required, you can limit upload to a single device collection.
- Click Enable Endpoint analytics for devices uploaded to Microsoft Endpoint Manager if you want to get insights to optimize the end-user experience in Endpoint Analytics.
- Sign in with your Global Administrator account when prompted. Select Yes to Create AAD Application notification. Click OK to exit the co-management properties once you’ve done making changes.
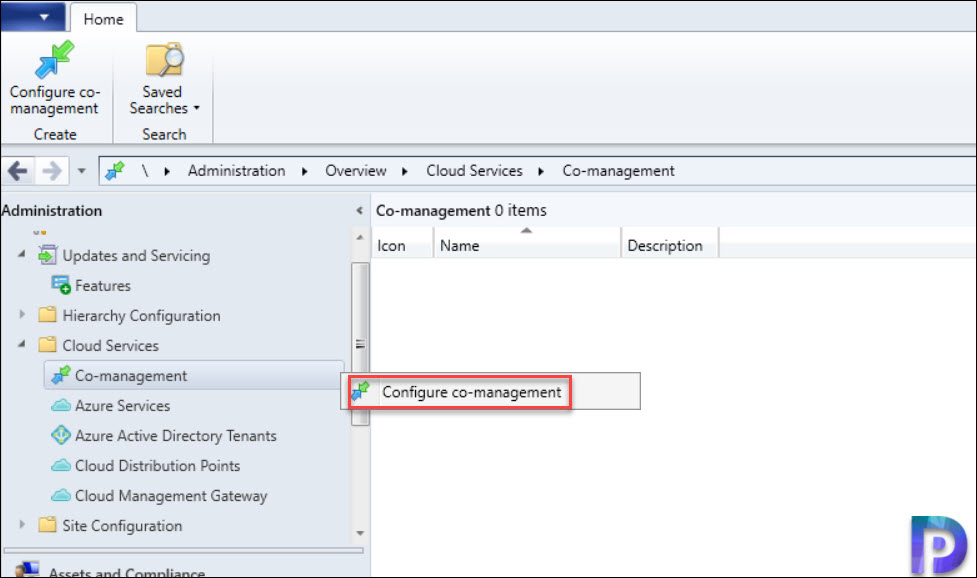
Configure Co-Management in ConfigMgr
To configure the Co-management for the first time in the Configuration Manager setup.
- Launch the Configuration Manager console.
- Go to Administration > Overview > Cloud Services > Co-management.
- Right click Co-management and click Configure co-management.
ConfigMgr Tenant Onboarding
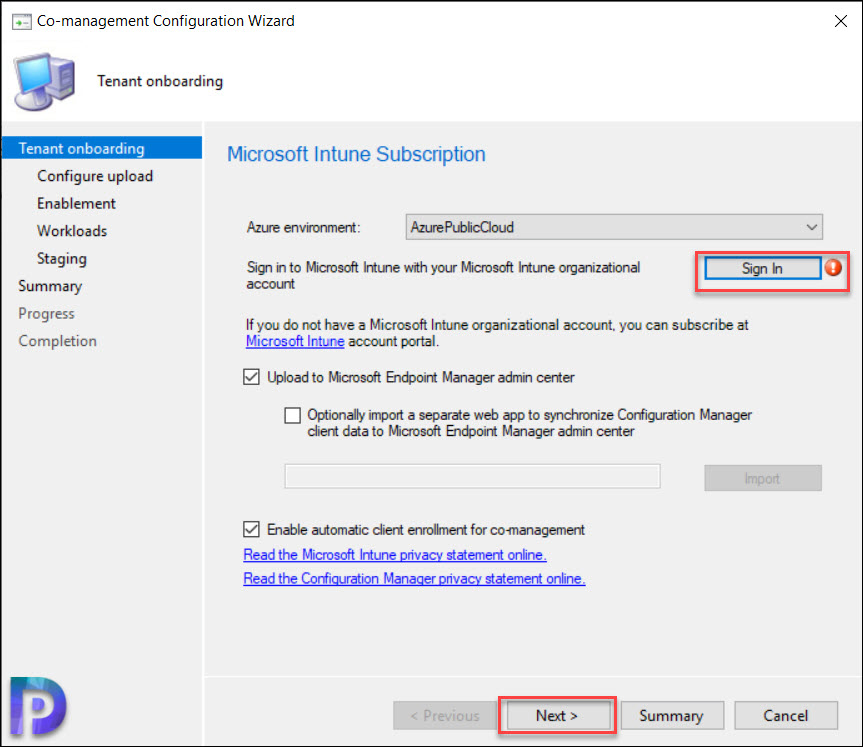
On the tenant onboarding page, select AzurePublicCloud for your environment. Azure Government Cloud and Azure China 21Vianet aren’t supported. Therefore, don’t select them.
Next, click Sign In. Use your Global Administrator account to sign in.
Ensure the Upload to Microsoft Endpoint Manager admin center option is selected on the tenant onboarding page.
Make sure the option Enable automatic client enrollment for co-management isn’t checked if you don’t want to enable co-management now. However if you do want to enable co-management, select the option.
Click Next.
Click Yes to accept the Create AAD Application notification. This action provisions a service principal and creates an Azure AD application registration to facilitate the sync.
Configure Upload to Microsoft Endpoint Manager Cloud Console
On the Configure Upload page, select the devices that you want to upload to Microsoft Endpoint Manager.
- All devices managed by Microsoft Endpoint Configuration Manager – This is a recommended option.
- Specific Collection – If you don’t wish to choose all devices, you can click and Browse and select a specific collection.
Endpoint Analytics – Enable Endpoint analytics for devices uploaded to Microsoft Endpoint Manager if you want to get insights to optimize the end-user experience in Endpoint Analytics.
Click Next.
Enable Co-Management in SCCM Console
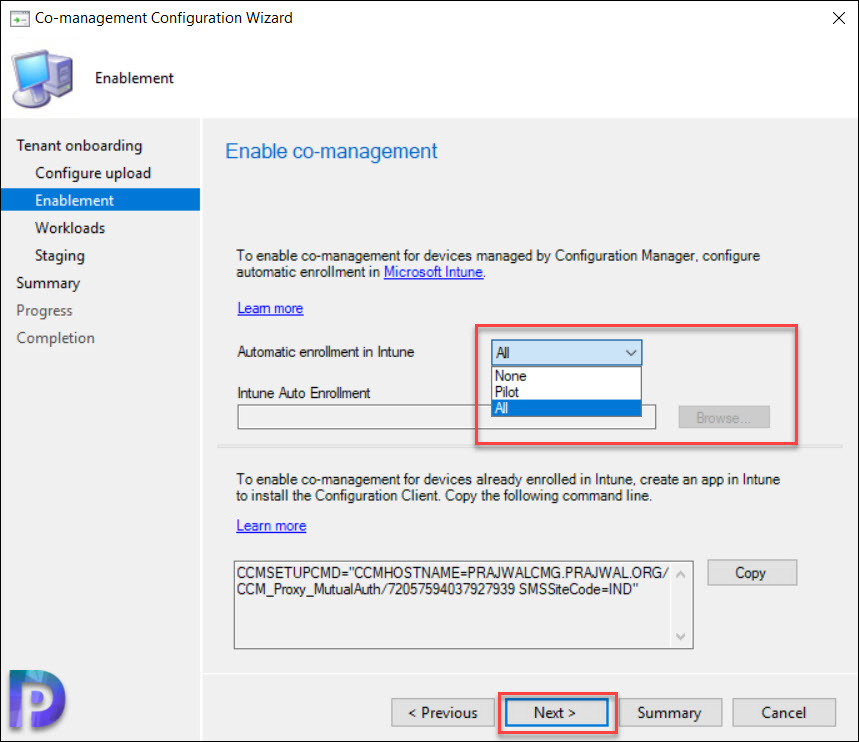
To enable co-management for devices managed by Configuration Manager, you must configure the automatic enrollment.
Next to Automatic enrollment in Intune, click the drop-down and select one of the following.
- None
- Pilot
- All
I have selected Pilot and for Intune Auto Enrollment, I have selected a Windows 10 device collection. This collection consists of only 4 devices running Windows 10. Click Next.
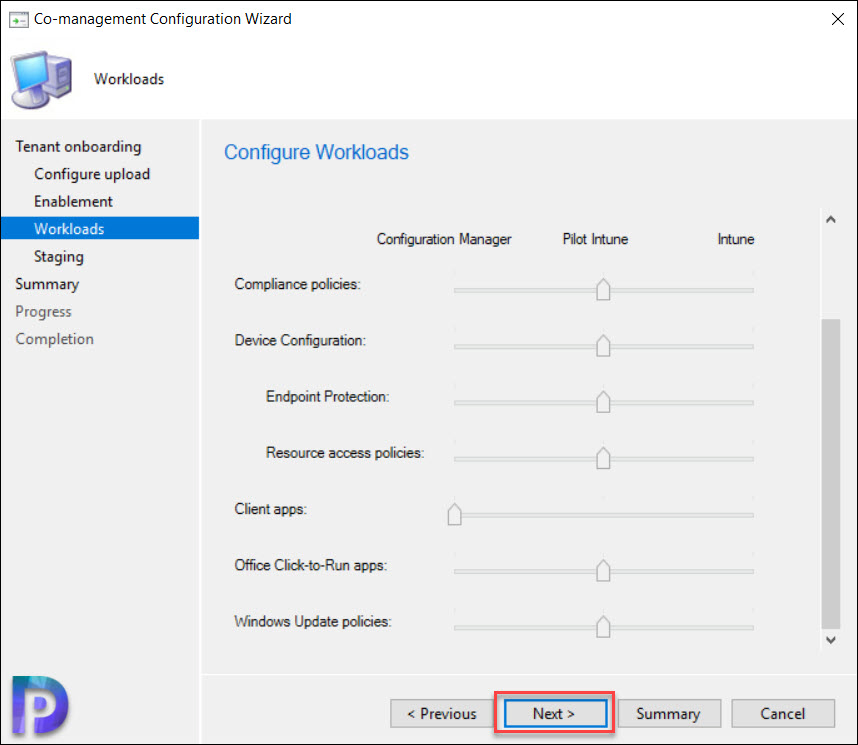
In this step, as an administrator you can configure specific workloads for Configuration Manager or Microsoft Intune.
Click Next.
Staging – Configure Roll Out Collections
When you configure a workaround for Pilot Intune, you must select a device collection to each of the pilot group.
For each of the items listed below, click Browse and select a device collection.
- Compliance Policies
- Device Configuration
- Endpoint Protection
- Resource access policies
- Office click-to-run apps
Finally click Next.
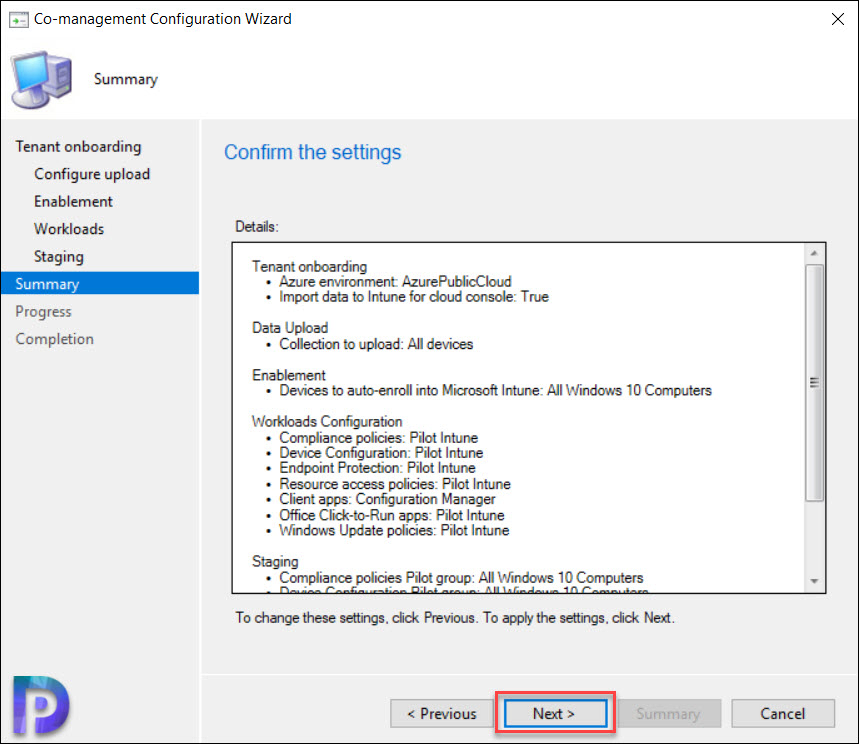
On the Summary page, click Next.
If you need to change or modify any of the co-management settings, you can edit co-management properties to enable device upload.
In the Configuration Manager console, if you navigate to Cloud Services > Azure Active Directory Tenants, you should see a new application. The name begins with ConfigMgrSvc_id.
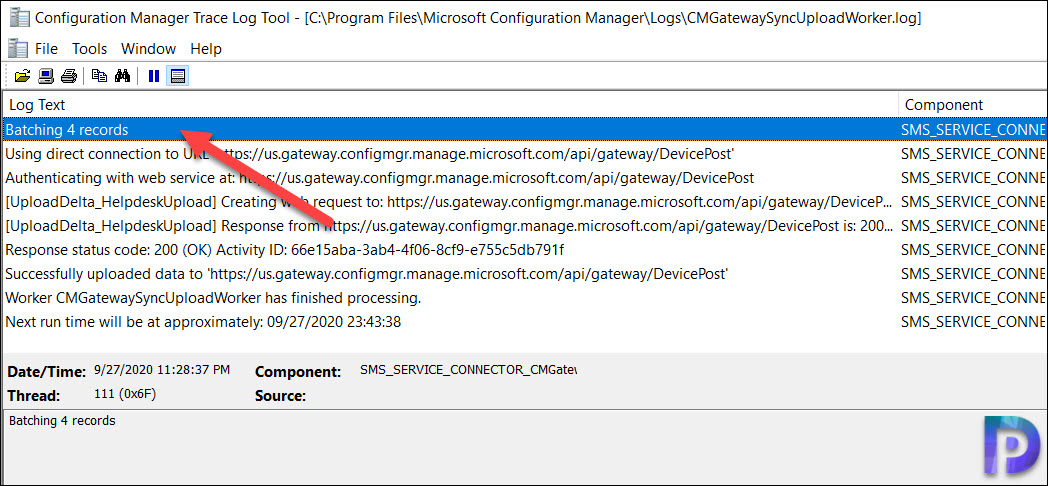
ConfigMgr Tenant Attach Log Files
If you are looking for Tenant Attach log files, then here they are. The below two ConfigMgr logs are located on the service connection point. Use these log files for troubleshooting tenant attach and device actions.
- CMGatewayNotificationWorker.log
- CMGatewaySyncUploadWorker.log
Most of all, if you monitor the CMGatewaySyncUploadWorker.log, we see 4 devices uploaded to Intune. The device collection that i chose has got 4 devices running Windows 10.
In the upcoming posts, I will show you what you can do after you have enabled tenant attach in SCCM. Until then, follow by blog for more such awesome guides.






Question: I’ve recently taken over looking after the Endpoint environment in my new workplace, and I see that co-management has been enabled already, and checking in Intune all Windows 10 machines are enrolled, and are showing co-managed. But under the Configure Upload section there is nothing checked (so no options are selected). If I were to enable this and choose the default All my devices option would that have any negative impact on how things are already setup and configured. Currently, there is no CMG or Azure Services configured (on my to-do list as well).
Hi
I don’t have an install string in for the client under the Enablement tab, all i see is “Please ensure the proper prereqs are installed” I’m not sure what those are?
Hey Prajwal, love your work as always. I have an odd issue hopefully you have some insight on. If I attempt to attach with my ***@***.onmicrosoft.com account which is GA, i get a “You can’t get there from here” error stating that its a personal device. If i use my ***@.com account, it gets past all of that but then fails because that account doesn’t have GA and can’t create the azure applications. What am i missing here? Does the configuration manager server have to be hybrid-joined before doing all of this? I cannot make my local domain account GA in Azure. Any idea’s on this?
Hi, when I click on the Sign In button on the Co-management Configuration Wizard. I get prompted with “content within this application coming from the website listed below is being blocked in IE enhanced Security configurations.” However, I’ve added https://login.microsoftonline.com to my local security. Any thoughts
Wonderful Article as always from you. Can you show picture of:
” Initiate Configuration Manager action permission under Remote tasks in the Microsoft Endpoint Manager admin center.” requirement?