Find Antimalware Software Status using CMPivot Query in SCCM
In this article, I will show you how to find antimalware software status using CMPivot query in SCCM (ConfigMgr). Using CMPivot, you can get the status of antimalware software installed on the computer(s), which is usually gathered by the Get-MpComputerStatus cmdlet.
CMPivot is a new in-console utility in SCCM that now provides access to the real-time state of devices in your environment. CMPivot’s KQL-based queries make it easier for administrators to find important data from the clients. All these CMPivot queries can be safely run on the ConfigMgr production server, and you can also export the results or output to a file.
With CMPivot, you can run some basic queries to check the antimalware status on a single computer or on an entire SCCM device collection. If you aren’t using Configuration Manager in your setup, you can find the status of antimalware software by running the Get-MpComputerStatus command.
I have been exploring the CMPivot queries from sometime and I find it very intriguing. The amount of information that you can gather from remote machines is simply outstanding. If you are interested in exploring CMPivot, you can check out all my posts on ConfigMgr CMPivot queries.
Take a look at some interesting CMPivot queries that you can use in SCCM:
- Find Serial Number of Computer using CMPivot
- Find Recently Used Applications using SCCM CMPivot Query
- Use CMPivot Query to Find WSUS Server Details in SCCM
- Easily Find Dot Net Version using SCCM CMPivot Query
- Find Default Browser using SCCM CMPivot Query
Run Get-MpComputerStatus command to find Antimalware Status
The Get-MpComputerStatus is a simple command with which you can check the status of antimalware software on the computer. If you don’t have access to CMPivot, finding the antimalware status can be achieved by running a simple command on the computer.
This command needs to be run locally in the PowerShell window and works on almost all the Windows operating systems with defender running. To get the status of the antimalware software, open the PowerShell and run the below command.
Get-MpComputerStatus
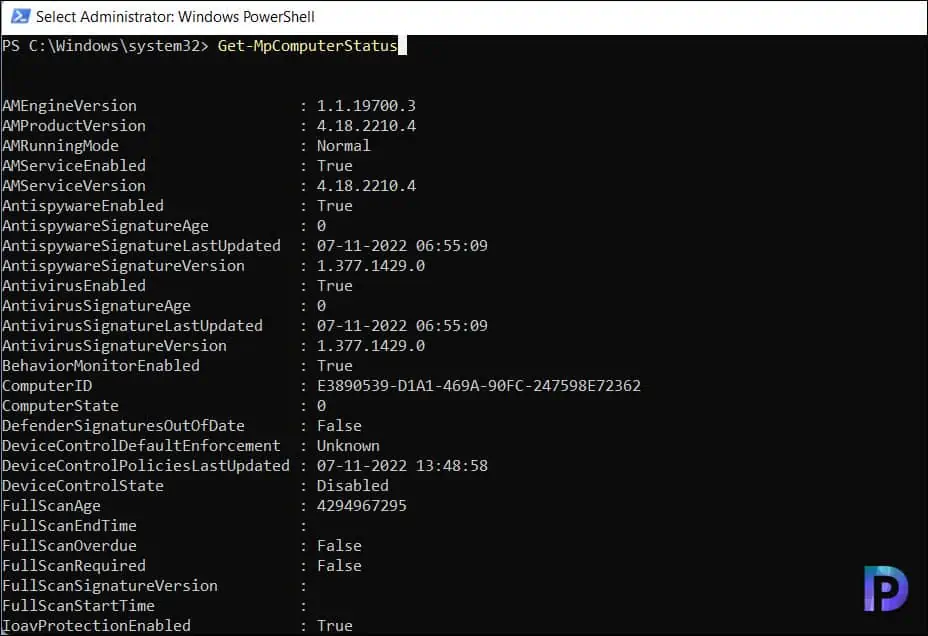
The output of the Get-MpComputerStatus command is pasted below. We see that output includes all the details about the antimalware software properties such as engine version, antivirus component status, RealTimeProtectionEnabled etc.
AMEngineVersion : 1.1.19700.3 AMProductVersion : 4.18.2210.4 AMRunningMode : Normal AMServiceEnabled : True AMServiceVersion : 4.18.2210.4 AntispywareEnabled : True AntispywareSignatureAge : 0 AntispywareSignatureLastUpdated : 07-11-2022 06:55:09 AntispywareSignatureVersion : 1.377.1429.0 AntivirusEnabled : True AntivirusSignatureAge : 0 AntivirusSignatureLastUpdated : 07-11-2022 06:55:09 AntivirusSignatureVersion : 1.377.1429.0 BehaviorMonitorEnabled : True ComputerID : E3890539-D1A1-469A-90FC-247598E723 ComputerState : 0 DefenderSignaturesOutOfDate : False DeviceControlDefaultEnforcement : Unknown DeviceControlPoliciesLastUpdated : 07-11-2022 13:48:58 DeviceControlState : Disabled FullScanAge : 4294967295 FullScanEndTime : FullScanOverdue : False FullScanRequired : False FullScanSignatureVersion : FullScanStartTime : IoavProtectionEnabled : True IsTamperProtected : True IsVirtualMachine : True LastFullScanSource : 0 LastQuickScanSource : 2 NISEnabled : True NISEngineVersion : 1.1.19700.3 NISSignatureAge : 0 NISSignatureLastUpdated : 07-11-2022 06:55:09 NISSignatureVersion : 1.377.1429.0 OnAccessProtectionEnabled : True ProductStatus : 524416 QuickScanAge : 18 QuickScanEndTime : 20-10-2022 13:10:30 QuickScanOverdue : True QuickScanSignatureVersion : 1.377.471.0 QuickScanStartTime : 20-10-2022 13:07:54 RealTimeProtectionEnabled : True RealTimeScanDirection : 0 RebootRequired : False SmartAppControlExpiration : SmartAppControlState : Off TamperProtectionSource : Signatures TDTMode : N/A TDTSiloType : N/A TDTStatus : N/A TDTTelemetry : N/A TroubleShootingDailyMaxQuota : TroubleShootingDailyQuotaLeft : TroubleShootingEndTime : TroubleShootingExpirationLeft : TroubleShootingMode : TroubleShootingModeSource : TroubleShootingQuotaResetTime : TroubleShootingStartTime : PSComputerName :
Find Antimalware Software Status using CMPivot in SCCM
Let’s look at the steps to find antimalware software status using CMPivot query in SCCM. Launch the SCCM console and go to Assets and Compliance > Overview > Device Collections. Choose the device collection against which you want to run the CMPivot query. Right-click the device collection and select Start CMPivot.
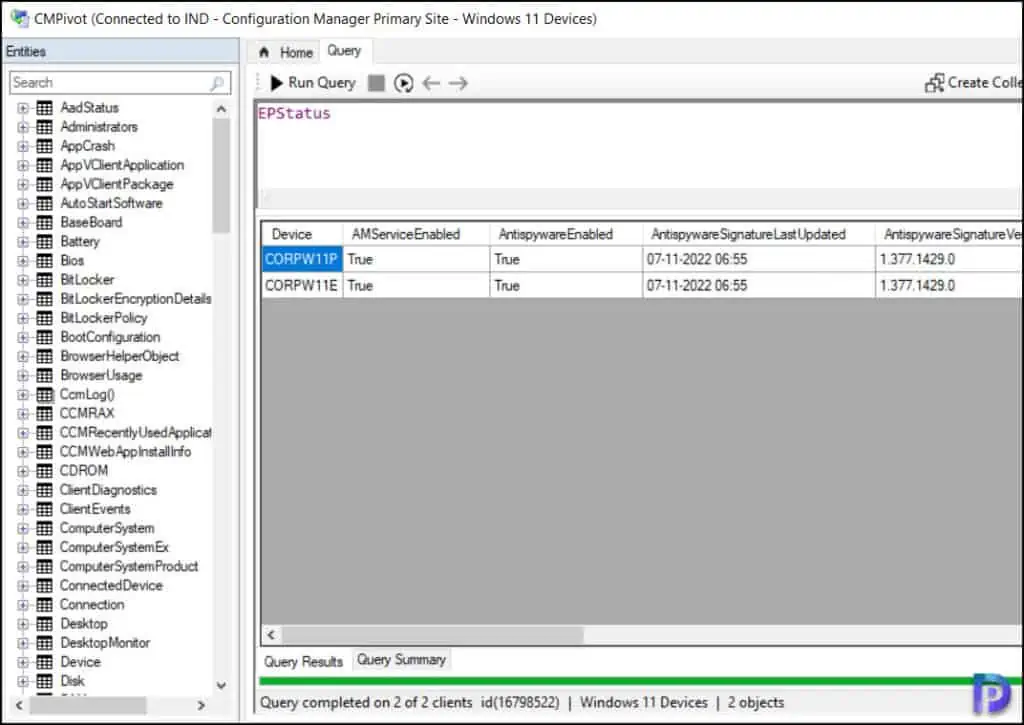
In the CMPivot tool, select the Query tab. Enter the query “EPStatus” and click on Run Query. The CMPivot query output includes a list all the details about the antimalware software including the status and signature updates. The output will include several details, and you might have to export the list to a CSV file and review the results.
Note: The Get-MpComputerStatus command will not work when entered in CMPivot query window. The EPStatus is the correct CMPivot query that you should use to check the antimalware software status and its properties.
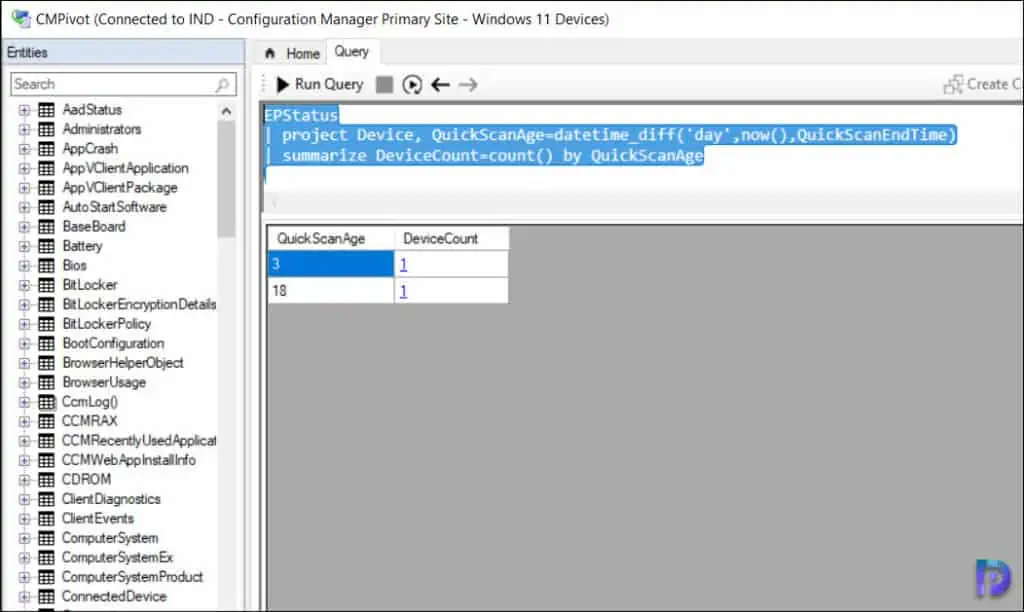
CMPivot query to find the Antimalware Software QuickScanAge with Device Count
In this example, we will run a simple CMPivot query to find the last quick scan age in days and filter the output along with the device count. “A quick scan looks at all the locations where there could be malware registered to start with the system, such as registry keys and known Windows startup folders.”
With CMPivot, you can query all the devices in SCCM to find the QuickScanAge property shows the number of days since the quick scan has been initiated. On a Windows device running defender software, if the signatures have never been updated you will see QuickScanAge value as 65535 days.
In the CMPivot window, run the below query to find the QuickScanAge of the devices along with the total device count.
EPStatus
| project Device, QuickScanAge=datetime_diff('day',now(),QuickScanEndTime)
| summarize DeviceCount=count() by QuickScanAge
Check the Antimalware Software Service Status using CMPivot Query
With CMPivot, you can run a query to determine the status of antimalware software service. You can find if the Windows Defender Firewall service is installed and running on the remote computers with CMPivot query. See also how to find the services installed and running on Windows computers with CMPivot.
You can manually determine the status of Windows defender service (mpssvc) by going to services console and checking the Windows Defender Firewall service status. On most computers, the service is up and running.
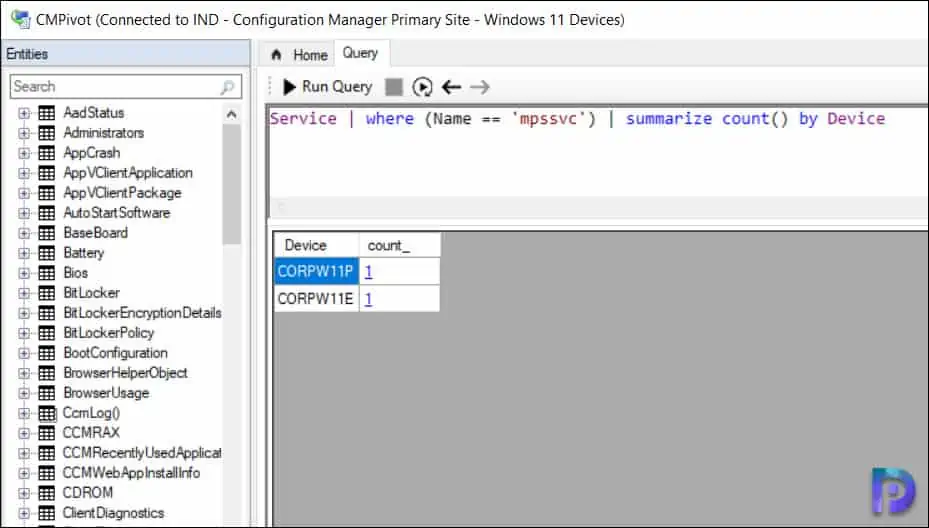
Run the below CMPivot query to find the antimalware software service status.
Service | where (Name == 'mpssvc') | summarize count() by Device
In the below query output, we see the computers that have the Windows Defender service up and running.

Hi Prajwal. Good learn about the CMPivot function. What I miss there though is AMProductVerion and AMEngineVersion. So far I can’t find that information in SCCM besides the Definition versions. One would like to know also the current version of Defender thus AMProductVersion itself. Now I know you could do that with powershell but still ain’t that information really available in SCCM itself?
I don’t think that information is available with SCCM hence you cannot query.
It is available, I did some more digging and trying and found out that you can query this information:
select SMS_G_System_AntimalwareHealthStatus.Version, SMS_R_System.Name from SMS_R_System inner join SMS_G_System_AntimalwareHealthStatus on SMS_G_System_AntimalwareHealthStatus.ResourceID = SMS_R_System.ResourceId where SMS_G_System_AntimalwareHealthStatus.Version > “0” order by SMS_G_System_AntimalwareHealthStatus.Version
I set the version to greater then “0” here to see all but you can specify a version.
Also later I found out the AMversion is also visible in device view (or in a collection view of devices better said) by adding a column “Antimalware Client Version”.