Block USB Drives using Intune – A Step-by-Step Guide
In this article, we’ll explain how to block USB drives using Intune. You can block access to USB devices using an attack surface reduction policy in Microsoft Intune on Windows 10/11.
Data breaches are becoming increasingly common, and USB drives can be a potential entry point for unauthorized access. Many organizations want to block specific types of USB devices, such as USB flash drives or cameras on company-owned devices. You may also want to allow specific USB devices, such as a keyboard or mouse.
Malware threats can easily be introduced through infected USB drives, compromising the entire network and exposing valuable information. Hence, it is important to restrict the use of removable storage media in organizations.
Attack surfaces are all the places where your organization is vulnerable to cyberthreats and attacks. Microsoft Defender for Endpoint includes numerous capabilities to help reduce your attack surfaces. Refer to the following article to learn about the Attack Surface Reduction Rules in Intune.
In one of our articles, we showed you how to block USB devices using GPO. For Windows devices that are enrolled in Intune, you can also use the ASR policy to block the use of removable storage on the device. This will basically restrict USB devices and allow specific USB devices using Administrative Templates in Microsoft Intune.
Ways to Block USB device access using Intune
There are two ways to block access to USB drives using Intune on Windows devices:
- Create an ASR policy and use the device control policy to disable “Removable Disk Deny Write Access.”
- Block USB device access on Windows using Intune Remediations
Useful Article: Disable Command Prompt using Group Policy (GPO)
Removable Disk Deny Write Access
According to Microsoft, the policy description states that if you enable the Removable Disk Deny Write Access policy setting, write access is denied to this removable storage class. If you disable or do not configure this policy setting, write access is allowed to this removable storage class.
To require that users write data to BitLocker-protected storage, enable the policy setting “Deny write access to drives not protected by BitLocker,” which is located in “Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Removable Data Drives.”
Microsoft recommends a layered approach to securing removable media, and Microsoft Defender for Endpoint provides multiple monitoring and control features to help prevent threats in unauthorized peripherals from compromising your devices.
Also Read: Easily Block Windows Registry Access using Intune Policy
Reasons for blocking USB device access
By blocking USB drives using Intune for corporate employees, organizations can mitigate risks effectively. Here are a few reasons why this measure is crucial:
1. Preventing Data Breaches: Unauthorized access to sensitive data can lead to severe financial and reputational damage for any organization. Employees are prevented from transferring or copying confidential information onto external devices if USB drives are blocked.
2. Mitigating Malware Threats: Malicious software often spreads through infected USB drives that are unknowingly inserted into company computers. By blocking these devices, organizations reduce the risk of malware infiltrating their systems and causing significant disruptions.
3. Enhancing Data Loss Prevention: Accidental loss or theft of important data is a major concern for corporations. Blocking USB drives helps prevent such incidents by restricting the ability to copy or transfer files onto portable storage devices that could potentially be misplaced or stolen.
4. Strengthening Access Control: Limiting the use of USB drives enhances access control measures within an organization. By preventing unauthorized individuals from easily transferring data in and out of the network, companies can ensure that only approved methods are used for data sharing.
Also Read: Disable Bluetooth access using Intune
Block USB Drives using Intune
We will now create an attack surface reduction policy to block USB drives using Intune.
- Sign in to the Microsoft Intune admin center.
- Go to Endpoint Security > Attack Surface Reduction.
- Select Create Policy.
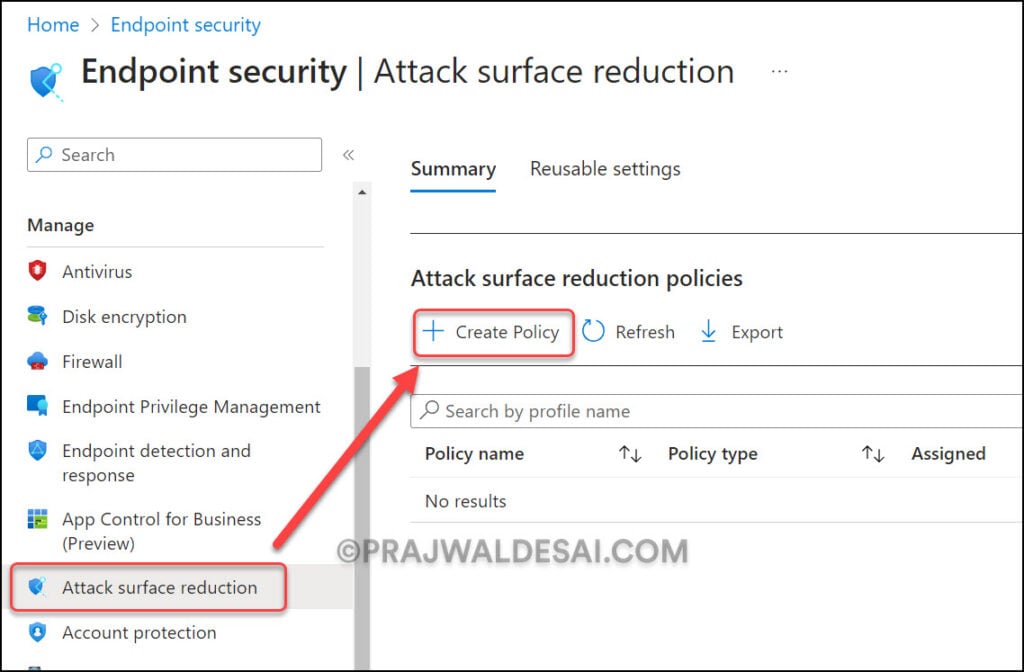
On the Create a profile window, select Platform as Windows 10 and later and Profile as Device Control. select Create.
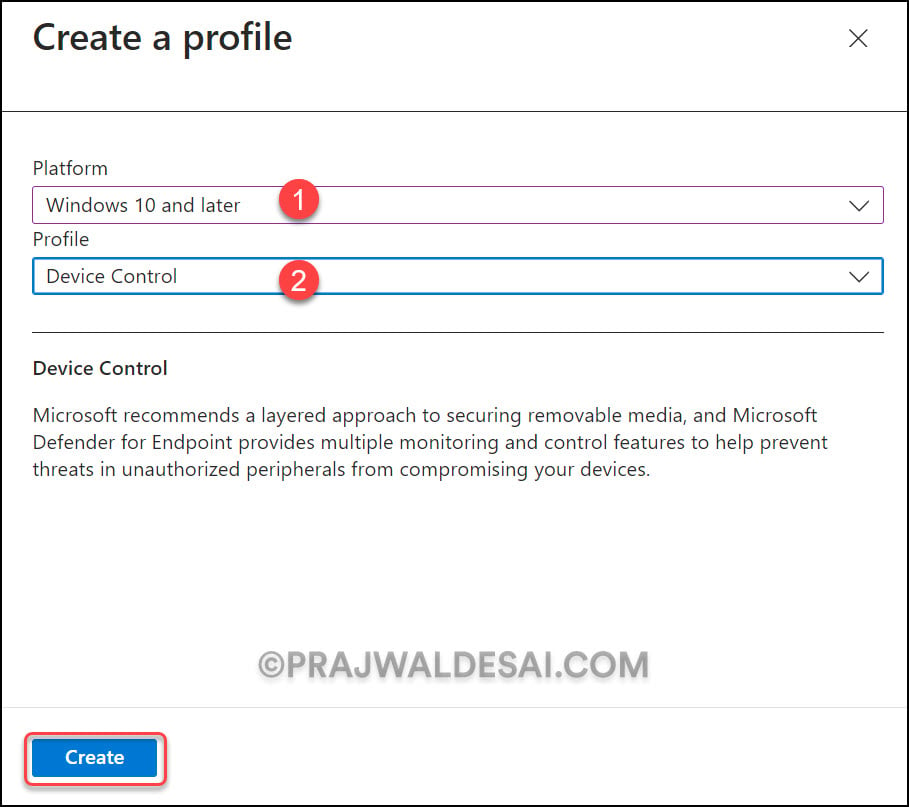
On the Basic tab, specify the name of the profile and add a brief description.
- Name: Block USB drives using Intune
- Description: Use ASR policy to block USB device access using Intune
A description helps other admins understand what this profile is about. Click Next.
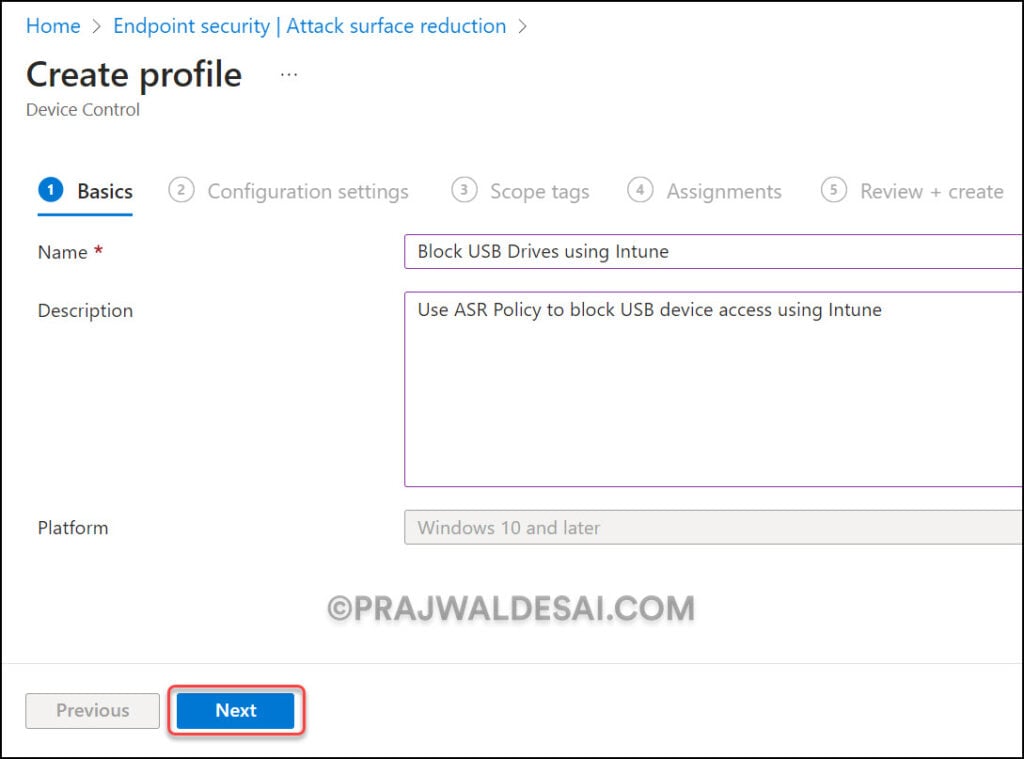
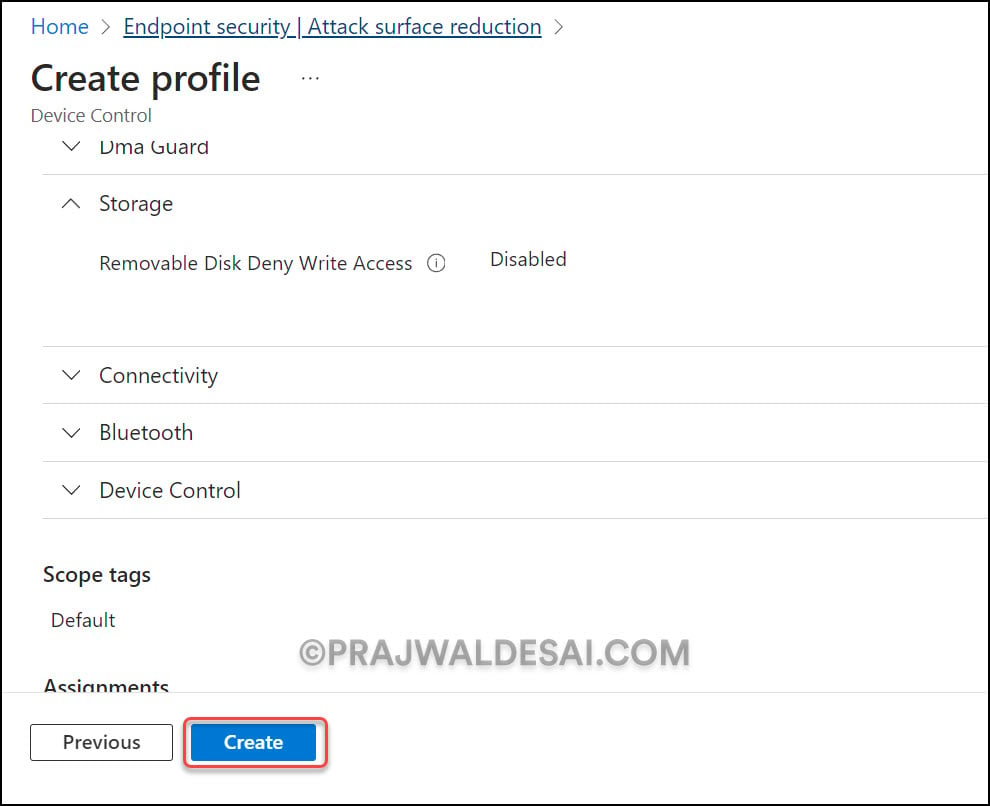
On the Configuration Settings tab, scroll down and look for the setting named “Removable Disk Deny Write Access“. Click the drop-down and select “Disabled” which will block USB devices on Windows devices.
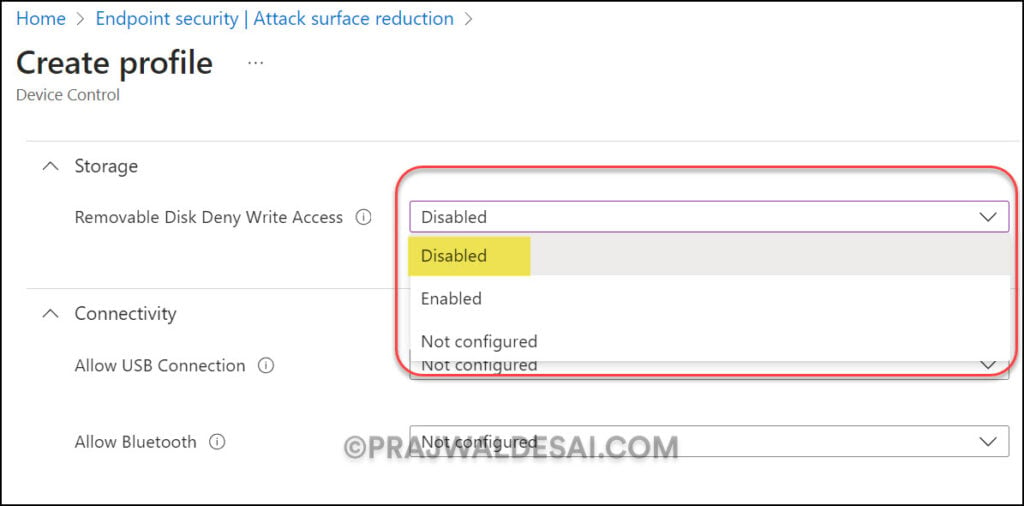
On the Scope tags tab, select the scope tags for the policy. If you don’t have any scope tags, click Next.
On the Assignments tab, click Add Groups and select the Entra groups to which you want to restrict access to USB drives. The devices that are part of the group will be prevented from using any USB devices. Click Next.
On the Review+Create tab, verify all the settings and click Create. A notification should appear confirming that the profile has been created successfully. This completes the steps to create an ASR policy to block USB drives using Intune.
Manually Sync Policies on Windows devices
When you assign a policy through Intune, it takes some time to apply it to the devices within the targeted groups. You can wait for the policy settings to apply, or to accelerate the sync, you can manually sync Intune policies on your Windows computers to sync with Intune. You can also use PowerShell to sync the Intune policies on Windows devices.
End-User Experience
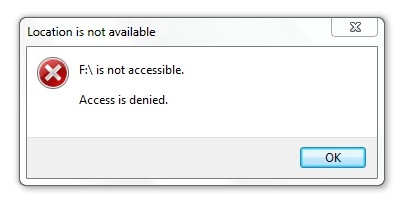
When a user connects a removable storage device to a computer after successfully applying the Intune policy to the devices, this is what the user will see. Location is not available. The drive is not accessible. Access is denied. This confirms that you can use an ASR policy in Intune to prevent the use of removable storage.

On the Configuration Settings tab, scroll down and look for the setting named “Removable Disk Deny Write Access“. Click the drop-down and select “Disabled” which will block USB devices on Windows devices.
It should be Selecting Enabled will block write access.