Enable FIDO2 Security Key in Azure Portal
In Azure portal, you can enable FIDO2 security key method for a passwordless authentication method. FIDO2 enables users to easily authenticate to online services in both mobile and desktop environments.
FIDO stands for Fast Identity Online and provides the option to use two factor authentication. The main goal of FIDO Alliance is to eliminate passwords on the web.
I remember Microsoft talking about passwordless authentication and at that time I didn’t knew anything about FIDO2. As of today Microsoft offers the following three passwordless authentication options :-
- Windows Hello for Business
- Microsoft Authenticator app
- FIDO2 security keys
FIDO2 security keys provide a seamless way for users to authenticate without entering a username or password. In the next step, I will show you show you how to enable FIDO2 security key authentication method in Azure Portal.
When you do that, you will be able to sign in to web-based applications with your Azure AD account using a FIDO2 security key. Most of all note that FIDO2 security keys are a public preview feature of Azure Active Directory.
Requirements
- Azure Multi-Factor Authentication
- Combined security information registration preview
- Compatible FIDO2 security keys
- WebAuthN requires Windows 10 version 1809 or higher
Note – Not all FIDO2 security keys are Microsoft compatible/approved. Hence before you proceed, check the list of FIDO2 keys compatible with Microsoft here.
Enable FIDO2 Security Key in Azure Portal
- Sign in to the Azure portal.
- Navigate to Azure Active Directory > All Services > Azure AD Authentication methods > Authentication method policy (Preview).
- On the right pane, select FIDO2 Security Key authentication method and enable it.
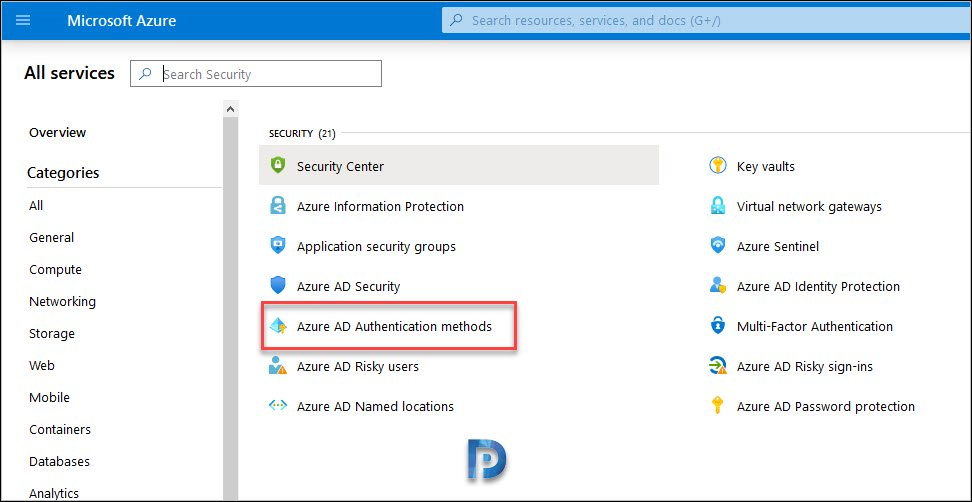
Under Authentication method policy (Preview), you find two methods.
- FIDO2 Security Key
- Microsoft Authentication passwordless sign-in
By default both of them are not enabled. Click FIDO2 Security Key.
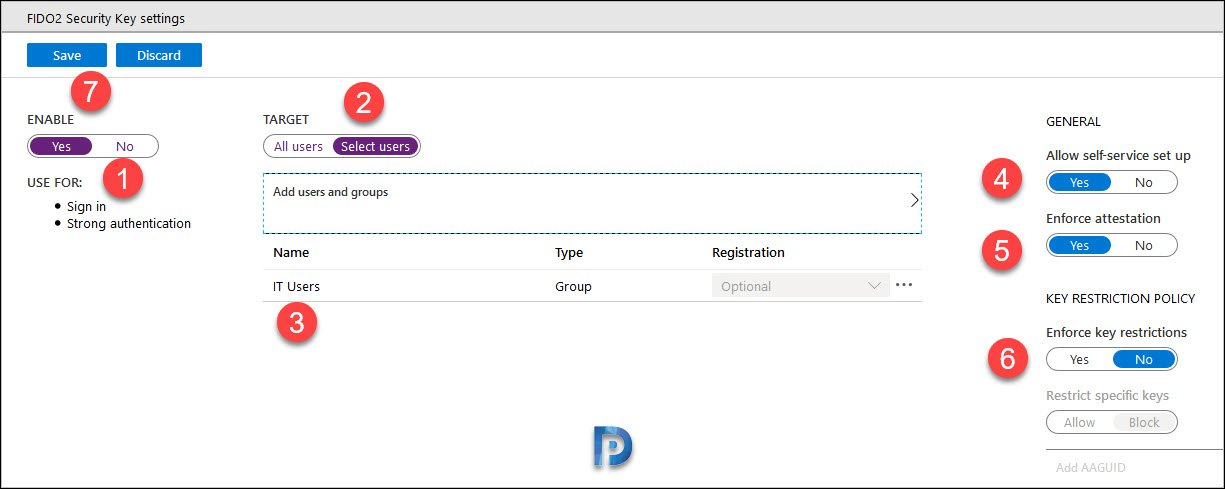
Follow the below steps to configure FIDO2 security key settings in Azure portal.
- Click Enable to enable the FIDO2 security key method.
- Select the Target which is either All Users or selection of Users/Groups.
- If you want to enable this method for specific groups, click Select Users and add the Users/Groups.
- Set Allow self-service set up to Yes.
- Set Enforce attestation to Yes.
- For Enforce key restriction, you can set it to No.

If you don’t allow self-service setup can user administrator set them up for users, or how do you get the security key setup for users?
Are you aware of any future or current support for Windows server authentication using Fido2? I’m seeing support for Windows 10, but for domain controllers, and application type servers the ability to implement Fido2?