Fix Incorrect Version of TLS Error Azure AD Connect
While installing Azure AD connect, I encountered incorrect version of TLS error. In this post, I will cover the solution to Azure AD Connect incorrect version of TLS 1.2 error.
If you have previously installed Azure AD connect, the installation is simple. However, Azure Active Directory Connect version 1.2.65.0 and later supports only TLS 1.2 for communications with Azure.
Transport Layer Security (TLS) protocol version 1.2 is a cryptography protocol that is designed to provide secure communications. The TLS protocol aims primarily to provide privacy and data integrity.
To maintain a secure connection to Azure Active Directory (Azure AD) and Microsoft 365 services, you must ensure your client apps and client and server operating system (OS) are enabled for TLS 1.2 and modern cipher suites.
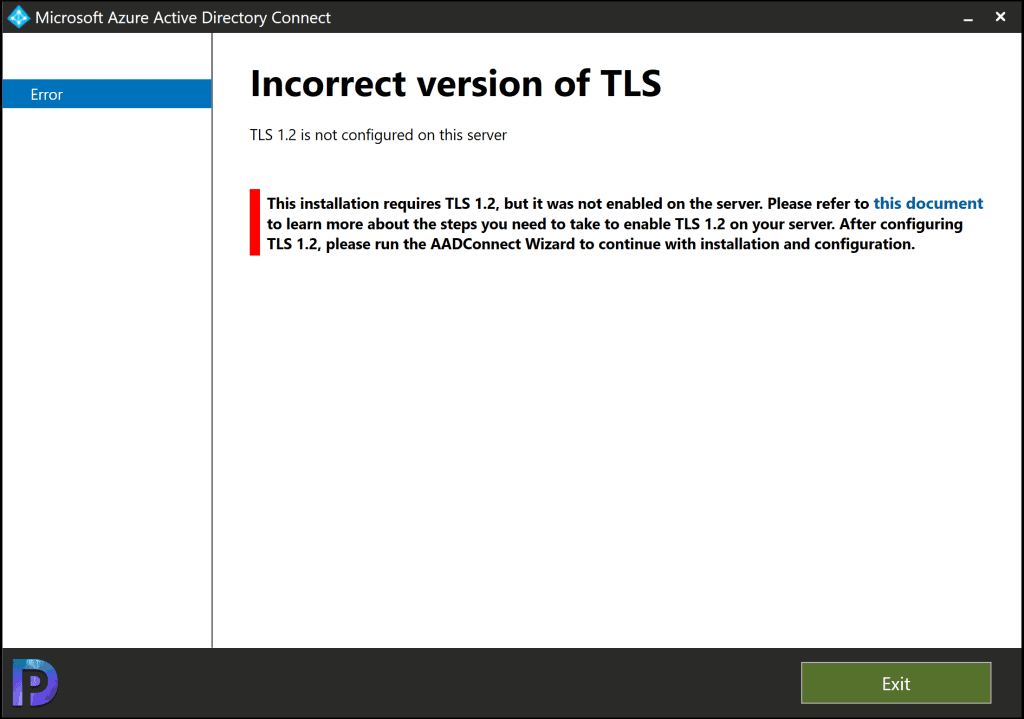
Now let me show you the incorrect TLS version 1.2 error that I encountered while installing Azure AD connect. Here is the complete error description.
Incorrect version of TLS. TLS 1.2 is not configured on this server.
This installation requires TLS 1.2, but it was not enabled on the server. You need to enable TLS 1.2 on your server. After configuring TLS 1.2, please run the AADConnect wizard to continue with installation and configuration.
I have published a video on how to fix Azure AD connect TLS 1.2 Error on YouTube.
Fix Incorrect Version of TLS Error Azure AD Connect
You can fix the incorrect version of TLS error by enabling TLS 1.2 on your Azure AD Connect server. There are two ways to force your Azure AD Connect server to use only TLS 1.2.
- Registry
- PowerShell
I recommend using PowerShell to force the Azure AD Connect server to use only TLS 1.2 because it’s easy. Registry method involves adding several registry keys, which might look difficult for most admins.
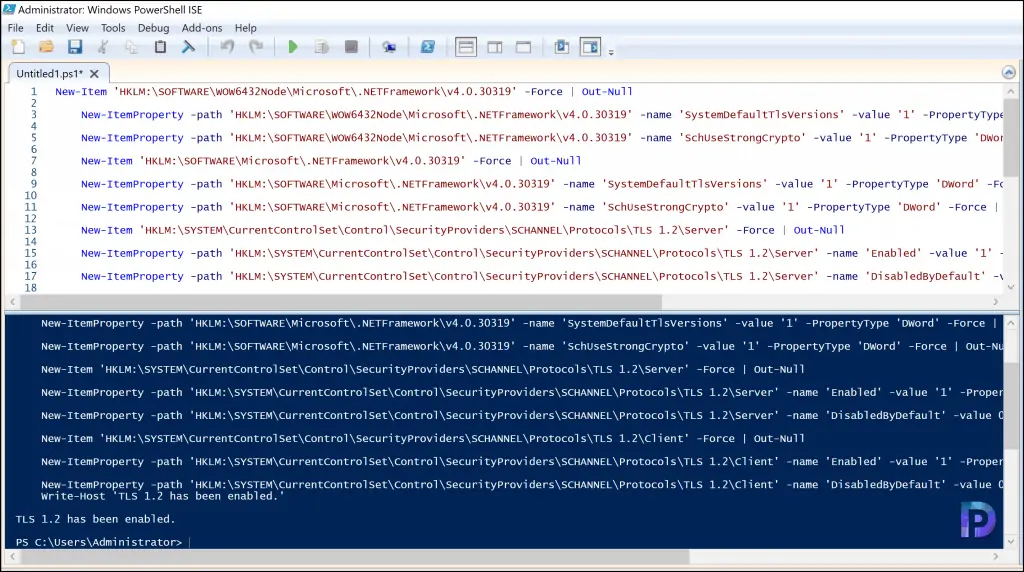
Microsoft provides you the PowerShell script to fix incorrect version of TLS error on Azure AD connect server. Copy the script to a file and save it as filename.ps1. You may also run the PowerShell script in PowerShell ISE without saving it anywhere.
New-Item 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null Write-Host 'TLS 1.2 has been enabled.'
On the Azure AD server, launch the Windows PowerShell ISE as administrator. Paste the above PowerShell script and run the script. Running the below script enables TLS 1.2 on Windows Server. Once the TLS 1.2 has been enabled, close the PowerShell ISE.
Restart the server after you enable TLS 1.2. Login and run the Azure AD connect tool, and now you shouldn’t see any TLS 1.2 error.