Configure PUA Protection using Group Policy
In this article, I will show you the steps to configure PUA protection using group policy. We will enable the policy Configure detection for potentially unwanted applications.
You can enable or disable detection for potentially unwanted applications on your Windows Operating System. You can choose to block, audit, or allow when potentially unwanted software is being downloaded or attempts to install itself on your computer.
PUA protection provides you protection against the applications that are not safe for your computer. Examples of Potentially unwanted apps include Advertising software products, Evasion software, Bundling software.
Allowing these unwanted apps to run on your computers leads to issues such as slowing down your PC and ads pop up while browsing. Hence, it is important to block potentially unwanted apps.
The PUA protection is supported on Windows 10, Windows Server 2019, Windows Server 2016 and Windows Server 2022. There are different methods to enable or configure PUA protection.
- You can enable PUA protection for Microsoft Edge browser
- Manually configure PUA protection in Microsoft Defender Antivirus
- Use Intune to configure PUA protection
- Use Configuration Manager to configure PUA protection
- Configure PUA protection using PowerShell cmdlets
Configure PUA Protection using Group Policy
Let’s look at the steps to configure PUA protection using group policy. Launch the group policy management console (GPMC). You can either create a new GPO or edit an existing one. I recommend creating a GPO and applying it to an OU instead of entire domain.
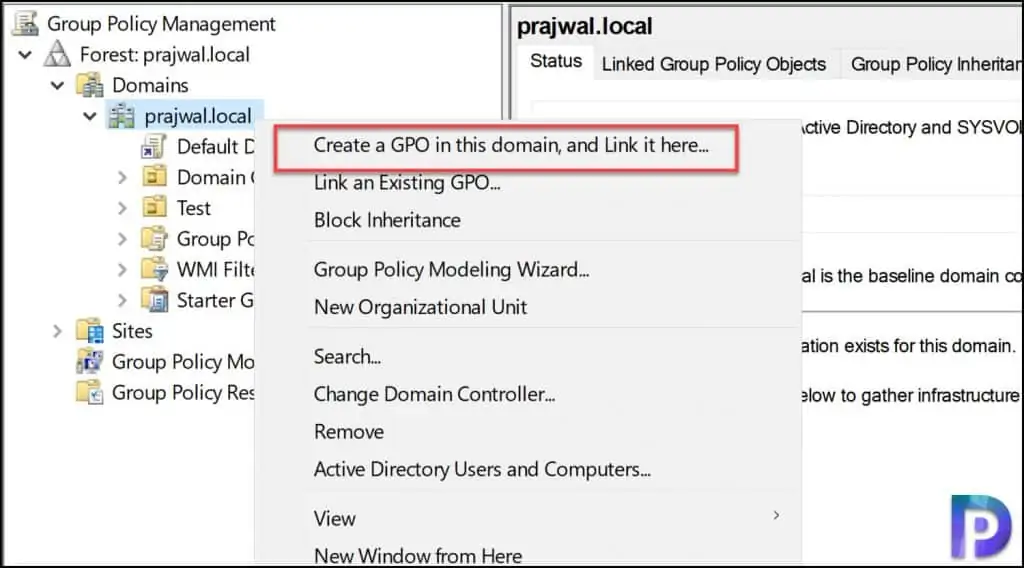
Right-click your domain and select Create a GPO in this domain and link it here.
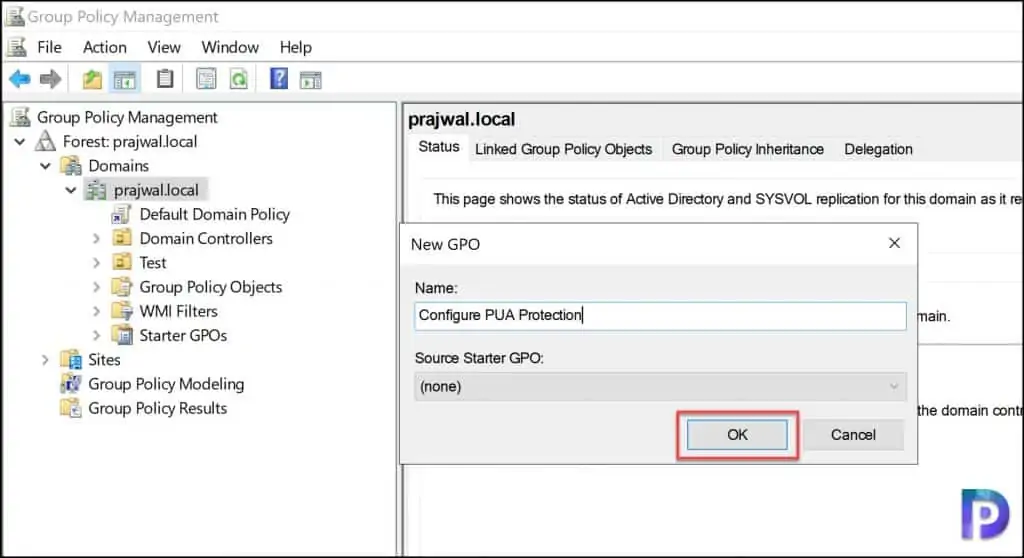
Specify the policy name as Configure PUA Protection and click OK.
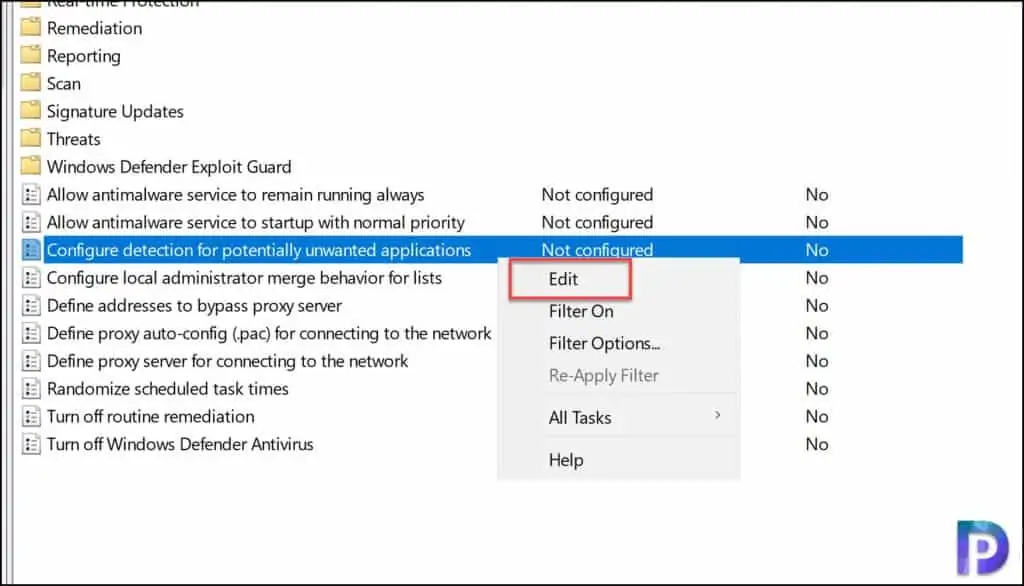
In the Group Policy Management Editor, go to Computer configuration > Administrative templates. Expand the tree to Windows Components > Windows Defender Antivirus. Right click Configure detection for potentially unwanted applications and select Edit.
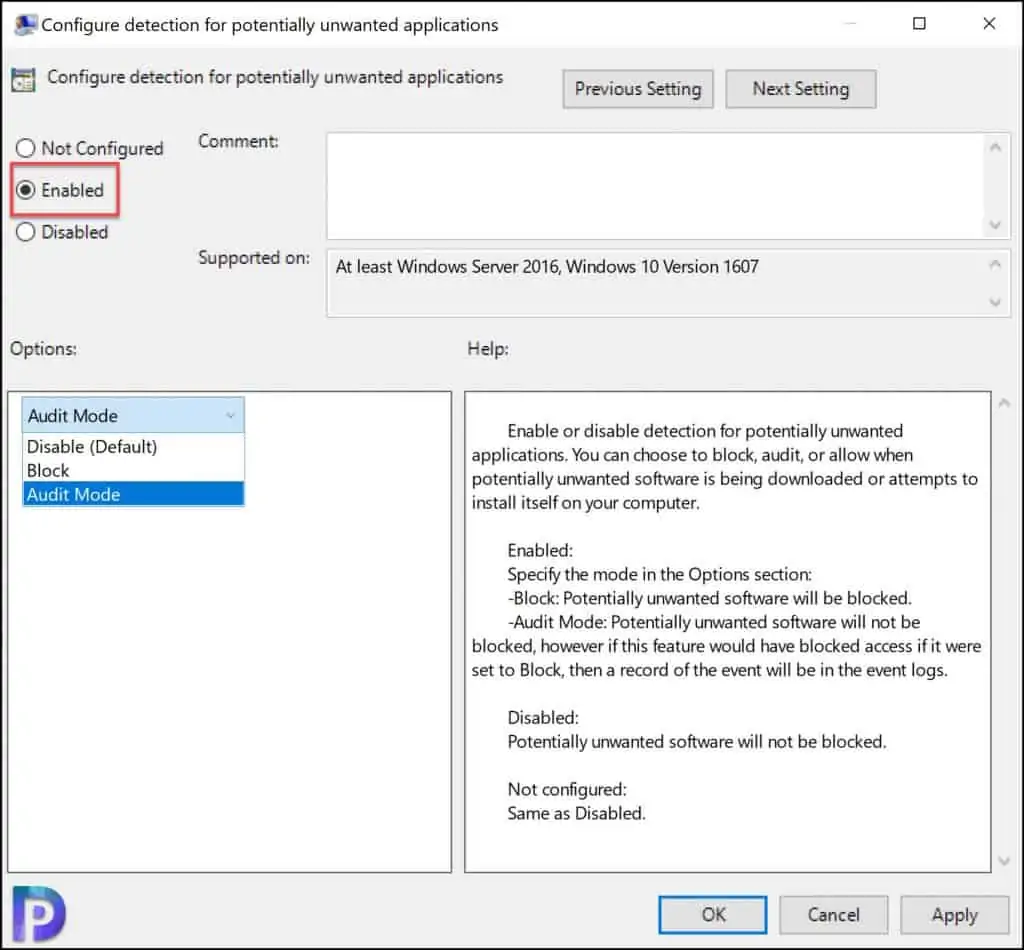
By default, this policy is set to Disabled. To enable the PUA protection, select Enabled. Under the options, you must select the mode.
- Block: Potentially unwanted software will be blocked.
- Audit Mode: Detect potentially unwanted applications without blocking them.
- Disabled: Potentially unwanted software will not be blocked.
Which mode should you select?. I recommend selecting the Audit mode and test how the setting works in your environment. The audit mode detects the potentially unwanted applications without blocking them.
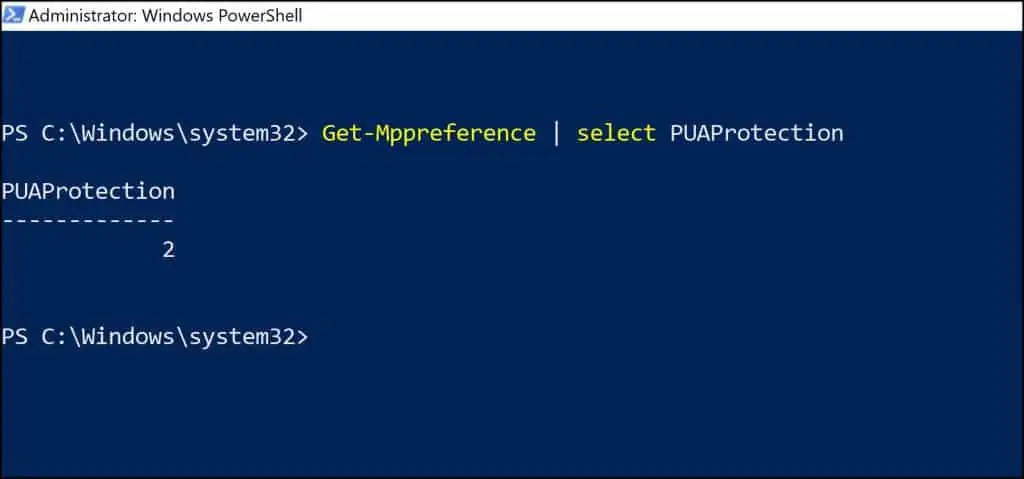
Finally, let’s check the PUAProtection value using PowerShell and check if the group policy has been deployed successfully. You can use the following PowerShell command to check the PUAProtection value.
Get-Mppreference | select PUAProtection
The PUAProtection value 2 indicates that PUA Protection is enabled with Audit mode.