Disable IE10 Automatic Update via Group Policy
In this post we will see the steps to disable IE10 automatic update via group policy. Microsoft distributes Internet Explorer 10 as a high-priority update through Automatic Updates for Windows 7 Service Pack 1 (SP1) x86 and x64, and Windows Server 2008 R2 SP1 x64. To disable IE 10 automatic update via group policy we can make use of a toolkit provided by Microsoft called IE 10 Blocker Toolkit which is intended for organizations that would like to block automatic delivery of Internet Explorer 10 to machines in environments where Automatic Updates is enabled.
Few things to consider before you download IE 10 Blocker Toolkit.
Do not deploy the IE 10 Blocker Toolkit in environments managed with an update management solution such as Windows Server Update Services or System Center Configuration Manager.
Also this toolkit is supported by OS – Windows 7 Service Pack 1 and higher, Windows Server 2008 R2 Service Pack 1 and higher. Download Internet Explorer 10 Blocker Toolkit
Once you download the IE 10 blocker toolkit, run the toolkit and provide a folder where the contents of toolkit are extracted. This toolkit contains two components: An executable blocker script (IE10_Blocker.cmd) and a Group Policy Administrative Template (.ADM file) (IE10_Blocker.adm)
If you want to disable IE10 automatic update via group policy then you can make use of IE10_Blocker.adm template. We will use the same template to disable IE10 automatic update. But before that let’s understand what the executable blocker script contains.
When you execute the IE 10 automatic update blocker script, the script creates a registry key and sets the associated value to block or unblock (depending on the command-line option used) automatic delivery of Internet Explorer 10 on either the local machine or a remote target machine.
Registry key: HKEY_LOCAL_MACHINESOFTWAREMicrosoftInternet ExplorerSetup10.0
Key value name: DoNotAllowIE10
If the DoNotAllowIE10 value is set to 0 then the distribution is not blocked and if its set to 1 then the distribution is blocked.
In the script there is a parameter called <machine name> which is optional. If it’s not specified, the action is performed on the local machine.
@echo off
Echo MICROSOFT TOOL KIT TO DISABLE DELIVERY OF
Echo MICROSOFT INTERNET EXPLORER 10
Echo.
Echo Copyright (C) Microsoft Corporation. All rights reserved.
Echo.
set ProductName=Internet Explorer 10
set REGBlockKey=HKLMSOFTWAREMicrosoftInternet ExplorerSetup10.0
set REGBlockValue=DoNotAllowIE10
set RemoteMachine=%1
if ""=="%1" goto Usage
if "/?"=="%1" goto Usage
if /I "/H"=="%1" goto Usage
if /I "/B"=="%1" goto LocalMachine
if /I "/U"=="%1" goto LocalMachine
set RemoteMachineName=%1
set Action=%2
:Parse
if /I "/B" == "%Action%" goto Block
if /I "/U" == "%Action%" goto UnBlock
goto Usage
:Block
Echo Blocking deployment of %ProductName% on %RemoteMachineName%
REG ADD "%RemoteMachine%%REGBlockKey%" /v %REGBlockValue% /t REG_DWORD /d 1 /f
goto End
:UnBlock
Echo Unblocking deployment of %ProductName% on %RemoteMachineName%
REG DELETE "%RemoteMachine%%REGBlockKey%" /v %REGBlockValue% /f
goto End
:LocalMachine
echo LOCAL!
set Action=%1
set RemoteMachine=.
set RemoteMachineName=the local machine
goto Parse
:Usage
Echo.
Echo This tool can be used to remotely block or unblock the delivery of
Echo %ProductName% via Automatic Updates.
Echo.
Echo ------------------------------------------------------------
Echo Usage:
Echo %0 [machine name] [/B] [/U] [/H]
REM [machine name] [/B|U|H]
Echo B = Block %ProductName% deployment
Echo U = Allow %ProductName% deployment
Echo H = Help
Echo.
Echo To block or unblock installation on the local machine use
Echo period ("." with no quotes) as the machine name
Echo.
Echo Examples:
Echo %0 mymachine /B (blocks delivery on machine "mymachine")
Echo.
Echo %0 /U (unblocks delivery on the local machine)
Echo ------------------------------------------------------------
Echo.
:End
Disable IE10 Automatic Update via Group Policy
In this section we will make use of the Group Policy Administrative Template .ADM file (IE10_Blocker.adm)– which allows administrators to import the new Group Policy settings to block or unblock automatic delivery of Internet Explorer 10 into their Group Policy environment, and use Group Policy to centrally execute the action across systems in their environment.
Log on to the domain controller, launch the Group Policy Management tool, right click on the domain name and create a new group policy. Right click the policy and click Edit.
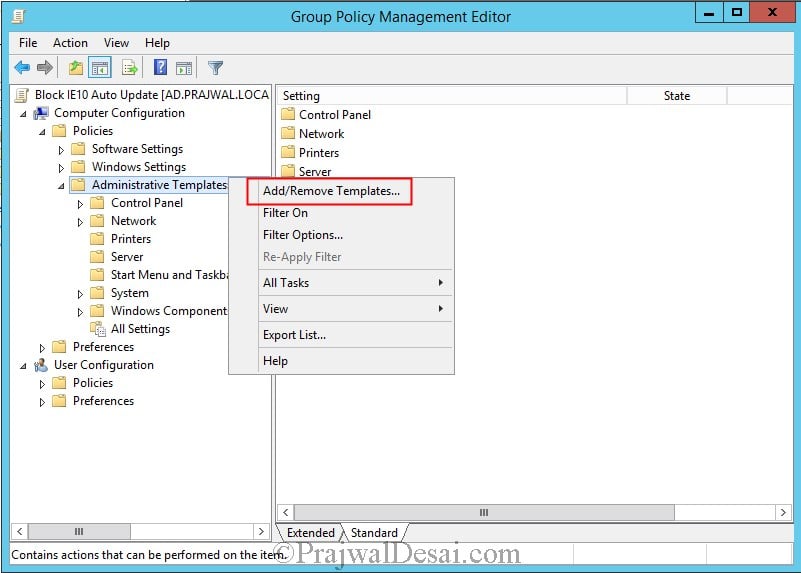
In the Group Policy Management Editor, expand Computer Configuration, expand Policies, right click Administrative Tools and click Add/Remove Templates.
Note – This setting is available only as a Computer setting, there is no Per-User setting.
In Add/Remove Templates window, click on Add and import the IE10_Blocker.adm template. Click Close.
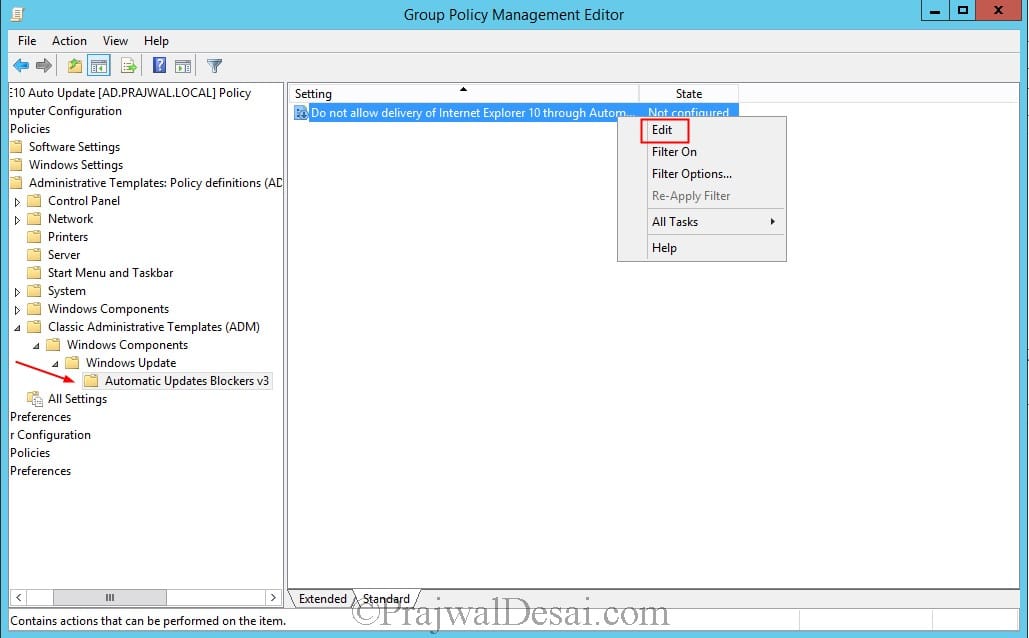
After you import the template navigate to Computer Configuration > Administrative Templates > Classic Administrative Templates > Windows Components > Windows Update > Automatic Updates Blockers v3.
Right click on the policy setting Do not allow delivery of Internet Explorer 10 through Automatic Updates and click Edit.
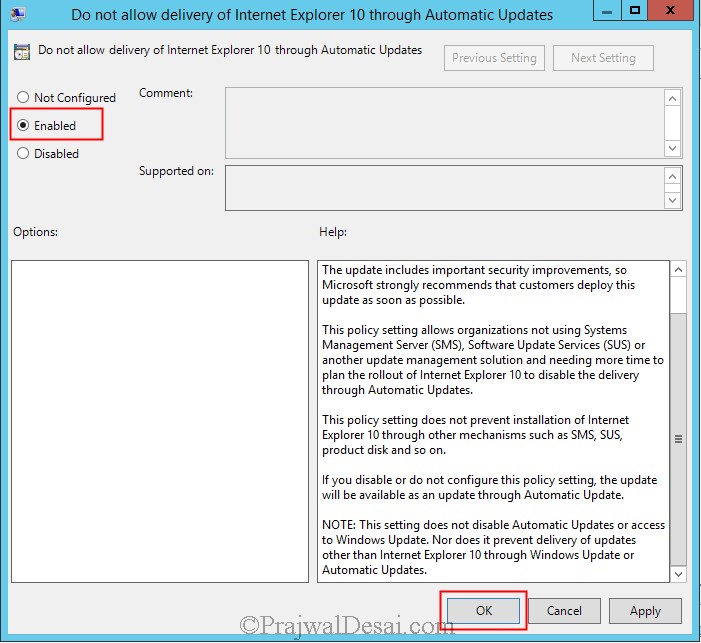
This policy setting allows you to disable delivery of Internet Explorer 10 via Automatic Updates. Click Enabled. Click OK.
Note – This setting does not disable Automatic Updates or access to Windows Update. Nor does it prevent delivery of updates other than Internet Explorer 10 through Windows Update or Automatic Updates.
On the client machines run a gpupdate command and you will see that IE10 will not install through automatic updates.



i have aquestion ,if You have a (WSUS) server named Server01
You need to prevent the WSUS service on Server01 from being updated automatically