Deploying the Client Certificate for Windows Computers
In this post we will see the steps for deploying the client certificate for windows computers. This post is a part of Deploy PKI Certificates for SCCM 2012 R2 Step by Step Guide. In the previous post we saw the PKI certificate requirements for SCCM 2012 R2, how to deploy web server certificate for site systems that run IIS. The next step is to deploy the client certificate for windows computers. You can log in with a root domain administrator account or an enterprise domain administrator account and use this account for all procedures in this example deployment.
This certificate deployment for windows computers has the following procedures:
1) Creating and Issuing the Workstation Authentication Certificate Template on the Certification Authority
2) Configuring Auto enrollment of the Workstation Authentication Template by Using Group Policy
3) Automatically Enrolling the Workstation Authentication Certificate and Verifying Its Installation on Computers
Creating and Issuing the Workstation Authentication Certificate Template on the Certification Authority
On the member server that is running the Certification Authority console, right-click Certificate Templates, and then click Manage to load the Certificate Templates management console. In the results pane, right-click the entry that displays Workstation Authentication in the column Template Display Name, and then click Duplicate Template.
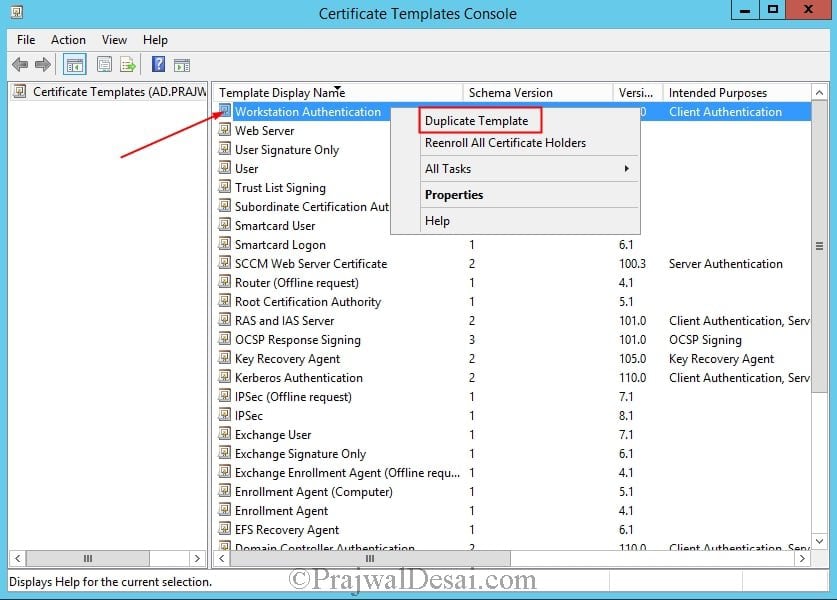
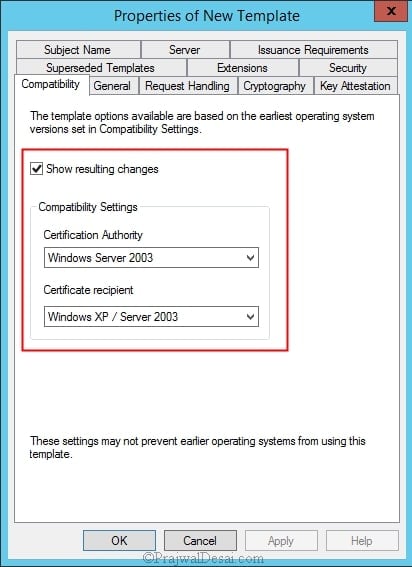
In the Duplicate Template dialog box, ensure that Windows Server 2003 is selected.
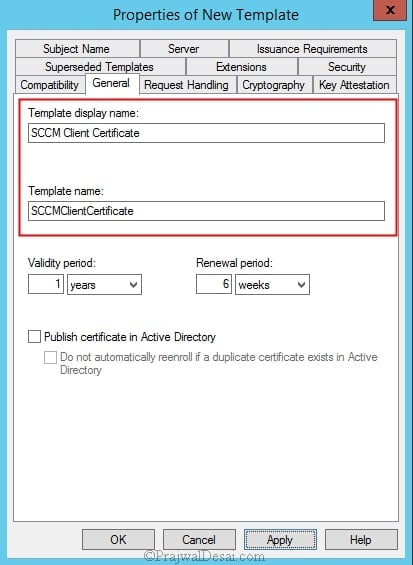
In the Properties of New Template dialog box, on the General tab, enter a template name to generate the client certificates that will be used on Configuration Manager client computers, such as SCCM Client Certificate.
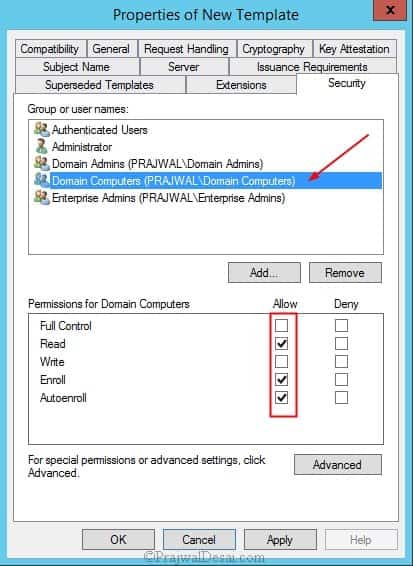
Click the Security tab, select the Domain Computers group, and select the additional permissions of Read and Autoenroll. Do not clear Enroll. Click OK and close Certificate Templates Console.
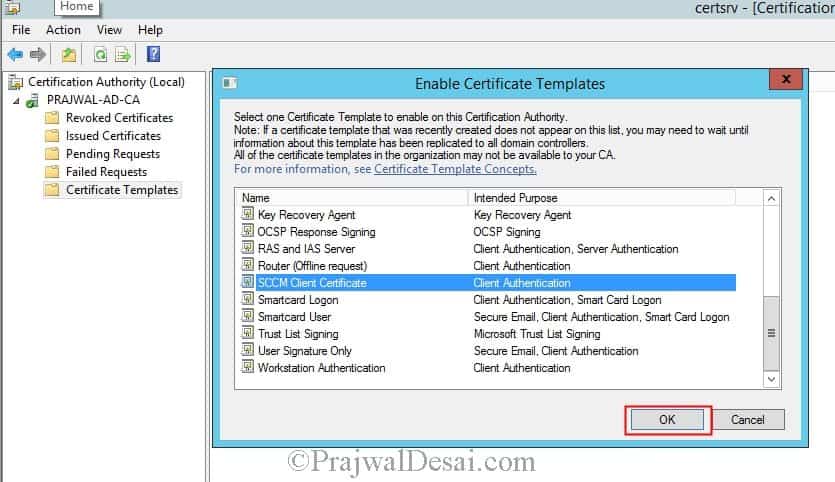
In the Certification Authority console, right-click Certificate Templates, click New, and then click Certificate Template to Issue. In the Enable Certificate Templates dialog box, select the new template that you have just created, SCCM Client Certificate, and then click OK. Close Certification Authority.
Configuring Auto enrollment of the Workstation Authentication Template by Using Group Policy
On the domain controller, launch the Group Policy Management. Navigate to your domain, right-click the domain, and then select Create a GPO in this domain, and Link it here. In the New GPO dialog box, enter a name for the new Group Policy, such as Autoenroll Certificates, and click OK
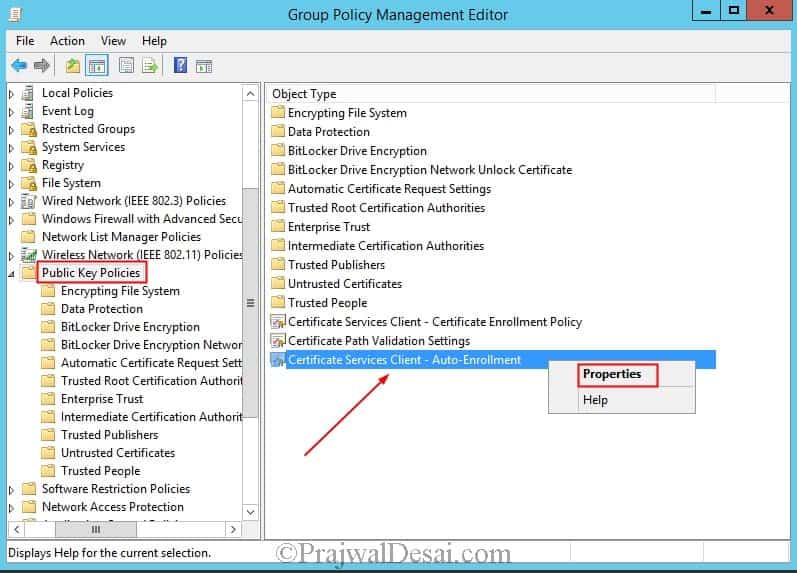
In the results pane, on the Linked Group Policy Objects tab, right-click the new Group Policy, and then click Edit. In the Group Policy Management Editor, expand Policies under Computer Configuration, and then navigate to Windows Settings > Security Settings > Public Key Policies. Right-click the object type named Certificate Services Client – Auto-enrollment, and then click Properties
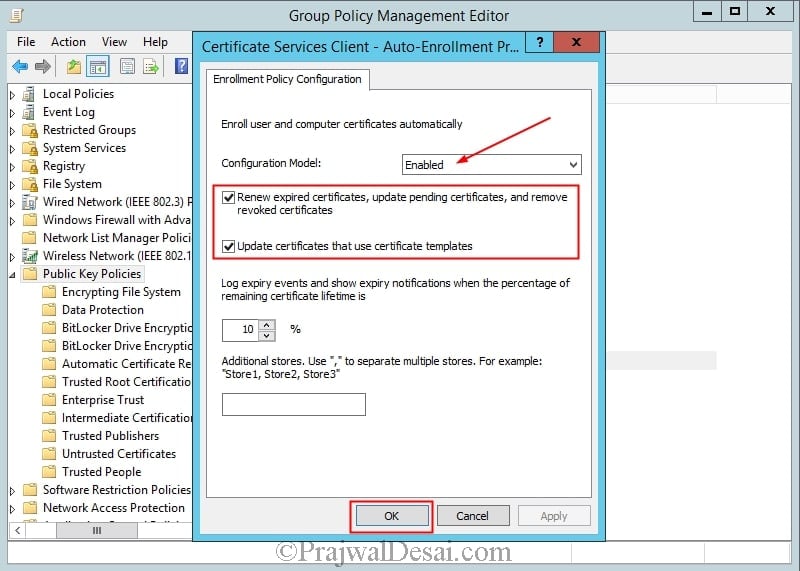
From the Configuration Model drop-down list, select Enabled, select Renew expired certificates, update pending certificates, and remove revoked certificates, select Update certificates that use certificate templates, and then click OK. Close the GPMC.
Automatically Enrolling the Workstation Authentication Certificate and Verifying Its Installation on Computers
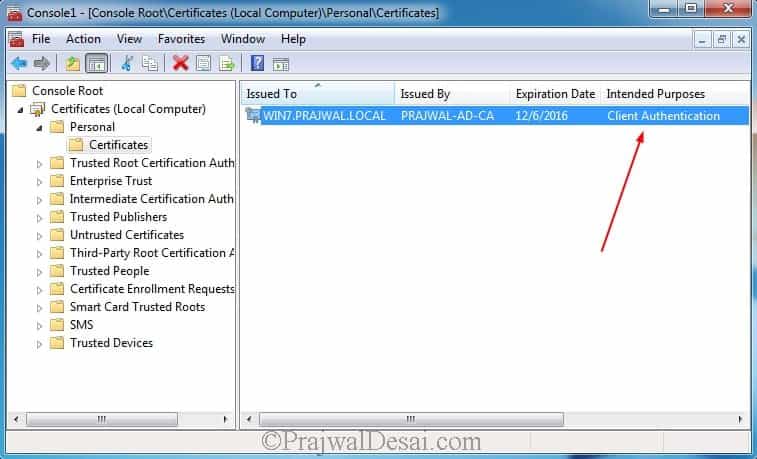
In the above steps we have configured auto enrollment of the workstation authentication template by using group policy. This procedure installs the client certificate on computers and verifies the installation. Restart the workstation computer, and wait a few minutes before logging on. Using the mmc command open the Certificate snap-in dialog box, select Computer account, and then click Next. In the Select Computer dialog box, ensure that Local computer: (the computer this console is running on) is selected, and then click Finish. In the console, expand Certificates (Local Computer), expand Personal, and then click Certificates. In the results pane, confirm that a certificate is displayed that has Client Authentication displayed in the Intended Purpose column, and that SCCM Client Certificate is displayed in the Certificate Template column. Close the console.
You need to repeat same steps for the member server to verify that the server that will be configured as the management point also has a client certificate. The computer is now provisioned with a Configuration Manager client certificate.


Hello,
First of all great site and article.
Other than the fact that you have probably followed Microsoft’s documentation, is there a reason you explicitly saying “ensure that Windows Server 2003 is selected”?
Do you know if the Server compatibility being “Windows Server 2016” would cause any issues?
Trying to get an answer from Microsoft is impossible because they point you to their article but they cannot explain the reason as to why.
Thanks
Hello,
I have the Client Authentication certificate expired on Clients which continue to send their inventory and get success from Deployment!!! Is it normal?
What is the process to renew them? could it be automatic?
Could I get a list of all certificates and expiration date for a specific SCCM Collection?
For now I am renewing them manually …
Thanks,
Dom
Can we deploy the client authentication certificate using SCCM to devices
Can you please help me how to generate certificate for DMZ/WG machines in order to communicate to the SCCM, ?
Hello,
which role services I need on CA to enable auto enrollment certificates to PC? Are the services roles sufficient: Certification Authority and Certification Aurhority Web Enrollement, or do I need to install the Certificate Enrollment Policy Web Service and Certification Enrollment Web Service?
You need another entry in the GPO to automatically issue the requested certificates, otherwise they willl be on “pending” on the CA.
You have to tell the clients what type of certificate they can request and this can be done by creating a Certificate Request Setting. To set it up expand the Public Keys Policies folder, right-click Automatic Certificate Request Settings and choose New > Automatic Certificate Request. Choose Computer.
Thanks for all the guides Prajwal, I learnt so much thanks to you!
Hello,
very nice guide.
One question regarding the certificates. Is it not important or necessary to tick the box
on the “General” tab “Publish certificate in Active Directory”?
BR
Sandra
Don’t do it. Not necessary. Will only bloat AD.
Great guide! Thanks for taking the time to document the process. 🙂
Hello! First of all great site, helped me a lot and I installed 2 System Center from scratch in the last 6 months. I trying now the certificates and all is working. I have one Server that is the primary site and only one by now (will have DP on different locations though). I already have Server Authentication certificates for IIS and SQL Server (was already there). Am I missing something from the last paragraph or is everything OK?
Could you plz tell us how to deploy above certificate for windows 10, as widows 10 nether communicate with our local CA server (Windows Server 2008 CA) nor auto enroll .
We are deploying certificate manually, but it make confusion for SCCM server as certificate is one for all computers not individual client certificate.