Deploying the Client Certificate for Distribution Points
In this post we will see the steps for deploying the client certificate for distribution points. This is one of the posts of Deploy PKI Certificates for SCCM 2012 R2 Step by Step Guide. In the previous post we understood more about PKI certificate requirements, deploying web server certificate for site systems that run IIS, deploying client certificates for windows computers. The next step is to deploy the client certificate for distribution points.
This certificate server two purposes. The certificate is used to authenticate the distribution point to an HTTPS-enabled management point before the distribution point sends status messages. When the Enable PXE support for clients distribution point option is selected, the certificate is sent to computers that PXE boot so that they can connect to a HTTPS-enabled management point during the deployment of the operating system. You can log in with a root domain administrator account or an enterprise domain administrator account and use this account for all procedures in this example deployment.
This certificate deployment has the following procedures:
- Creating and Issuing a Custom Workstation Authentication Certificate Template on the Certification Authority
- Requesting the Custom Workstation Authentication Certificate
- Exporting the Client Certificate for Distribution Points
Creating and Issuing a Custom Workstation Authentication Certificate Template on the Certification Authority
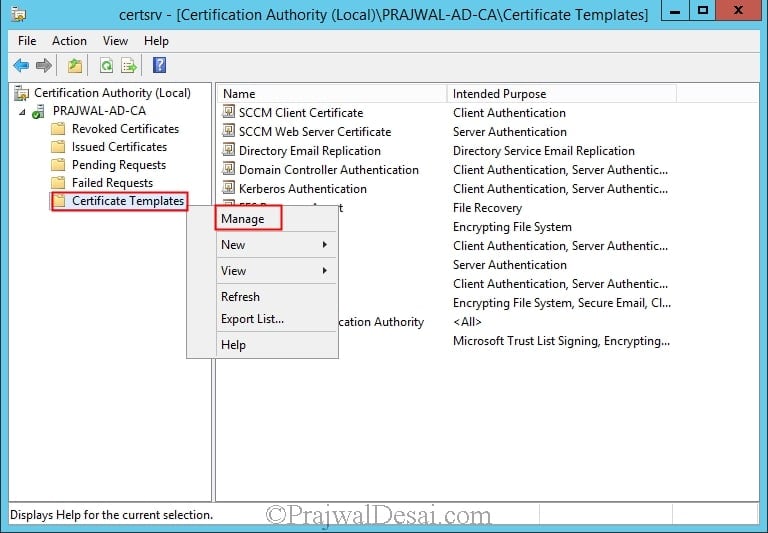
On the member server that is running the Certification Authority console, right-click Certificate Templates, and then click Manage to load the Certificate Templates management console.
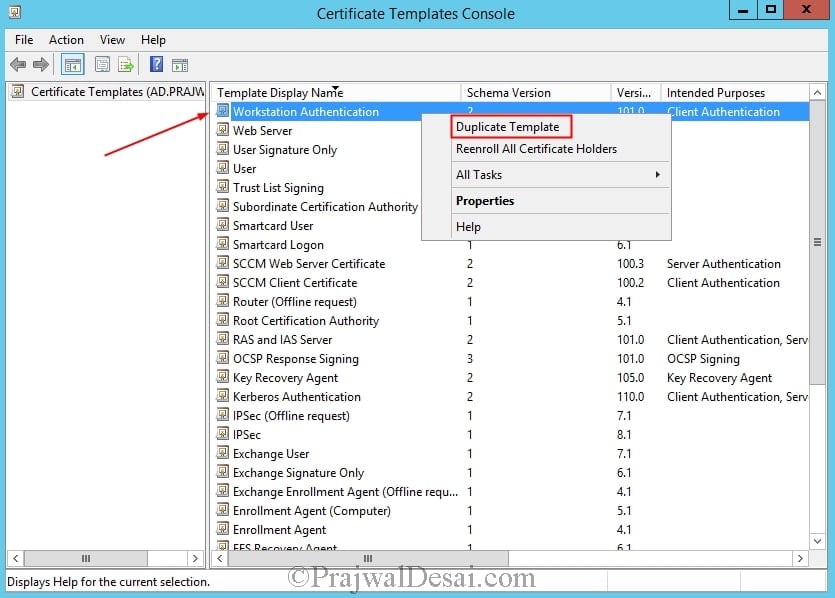
In the results pane, right-click the entry that displays Workstation Authentication in the column Template Display Name, and then click Duplicate Template.
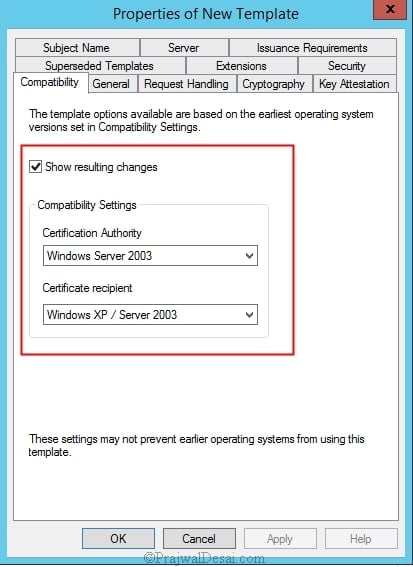
In the Duplicate Template dialog box, ensure that Windows 2003 Server is selected.
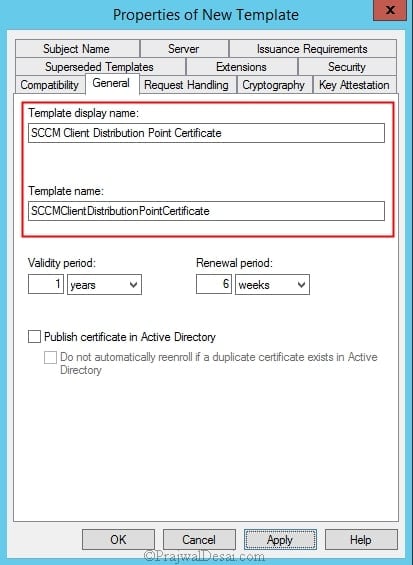
In the Properties of New Template dialog box, on the General tab, enter a template name to generate the client authentication certificate for distribution points, such as SCCM Client Distribution Point Certificate.
Click the Request Handling tab, and select Allow private key to be exported.
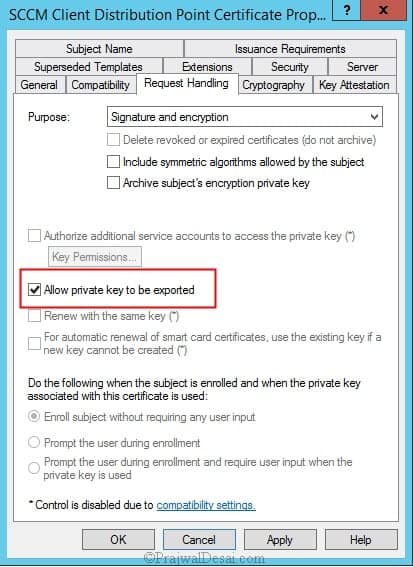
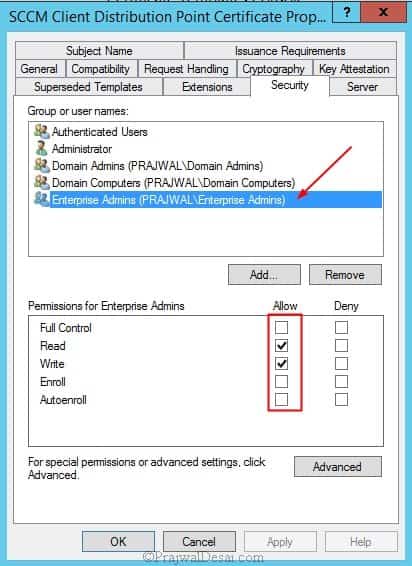
Click the Security tab, and remove the Enroll permission from the Enterprise Admins security group.
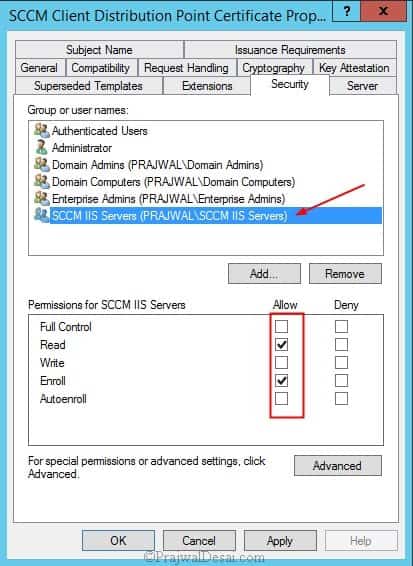
Click Add, enter SCCM IIS Servers in the text box, and then click OK. Select the Enroll permission for this group, and do not clear the Read permission. Click OK and close Certificate Templates Console.
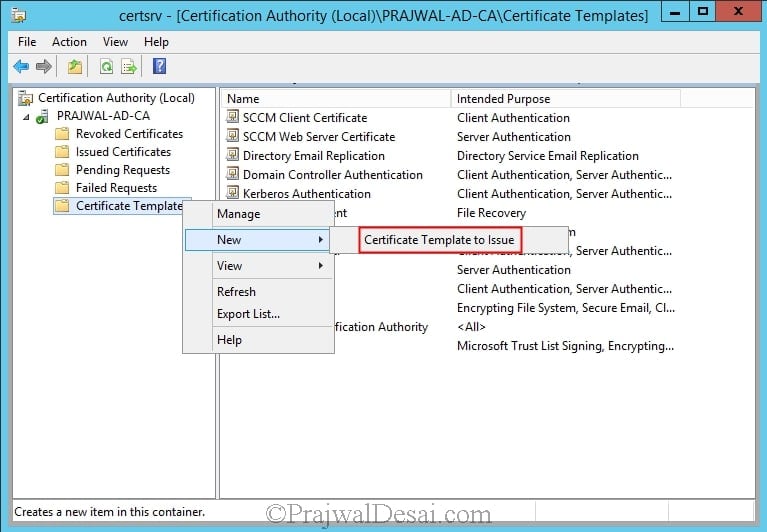
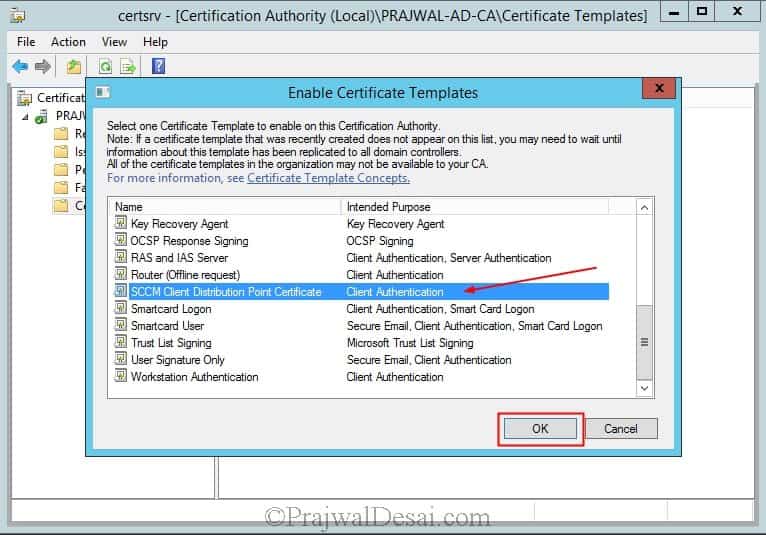
In the Certification Authority console, right-click Certificate Templates, click New, and then click Certificate Template to Issue.
In the Enable Certificate Templates dialog box, select the new template that you have just created, SCCM Client Distribution Point Certificate, and then click OK.
Requesting the Custom Workstation Authentication Certificate
This procedure requests and then installs the custom client certificate on to the member server that runs IIS and that will be configured as a distribution point. Run the mmc command to launch the Certificate snap-in dialog box, select Computer account and then click Next. In the Select Computer dialog box, ensure Local computer: (the computer this console is running on) is selected, and then click Finish.In the Add or Remove Snap-ins dialog box, click OK. In the console, expand Certificates (Local Computer), and then click Personal. Right-click Certificates, click All Tasks, and then click Request New Certificate.
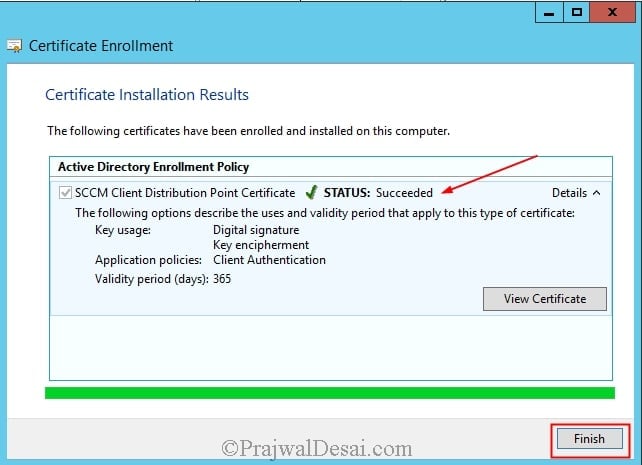
On the Request Certificates page, select the SCCM Client Distribution Point Certificate from the list of displayed certificates, and then click Enroll.
On the Certificates Installation Results page, wait until the certificate is installed, and then click Finish.
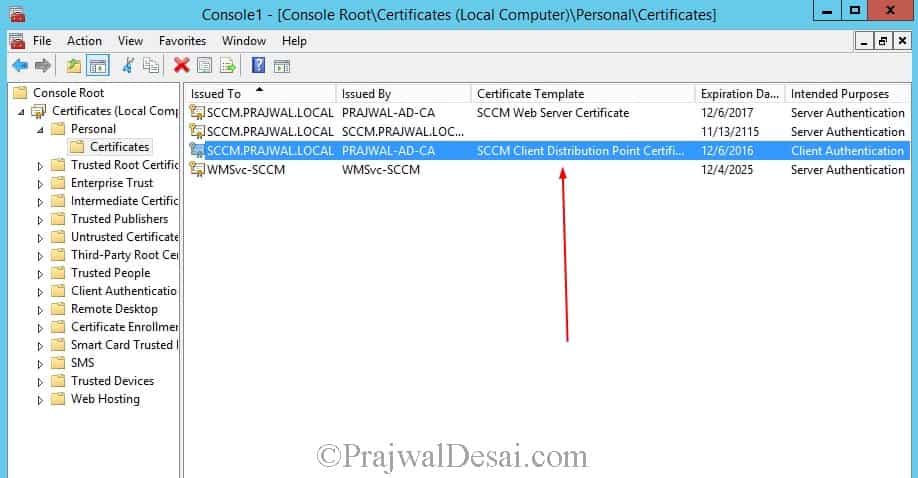
In the results pane, confirm that a certificate is displayed that has Client Authentication displayed in the Intended Purpose column, and that SCCM Client Distribution Point Certificate is displayed in the Certificate Template column.
Exporting the Client Certificate for Distribution Points
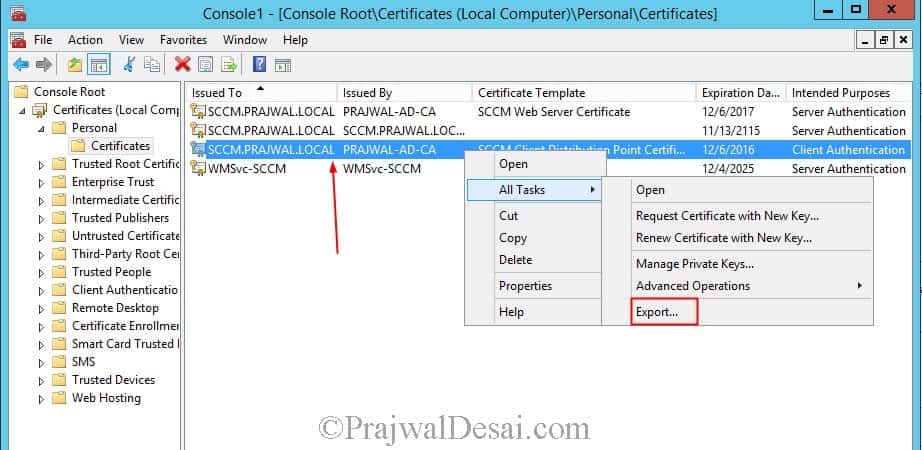
In the Certificates (Local Computer) console, right-click the certificate that you have just installed, select All Tasks, and then click Export.
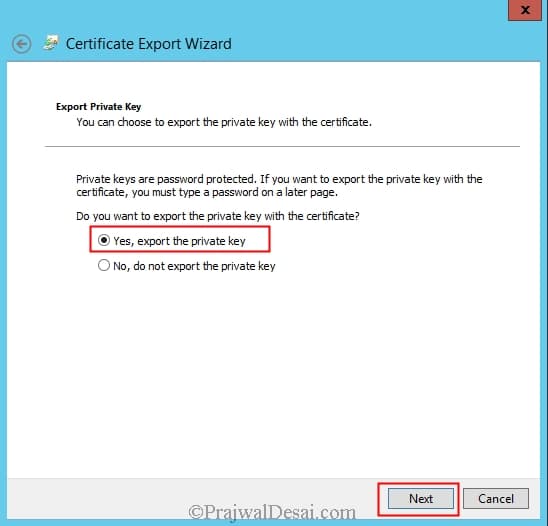
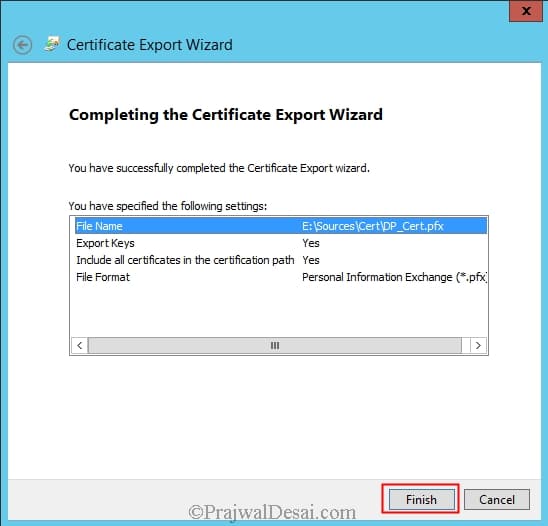
In the Certificates Export Wizard, click Next. On the Export Private Key page, select Yes, export the private key, and then click Next.
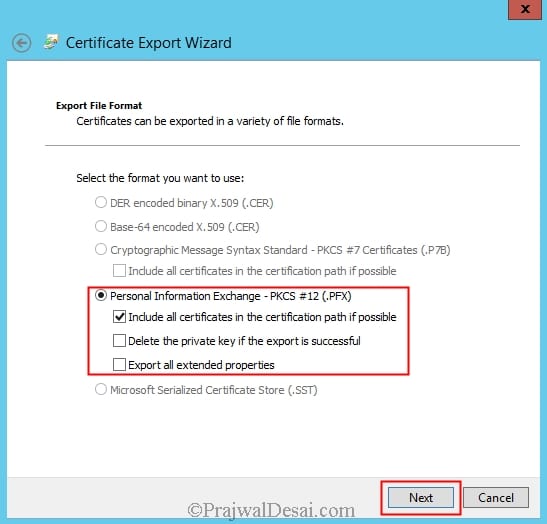
On the Export File Format page, ensure that the option Personal Information Exchange – PKCS #12 (.PFX) is selected. Click Next.
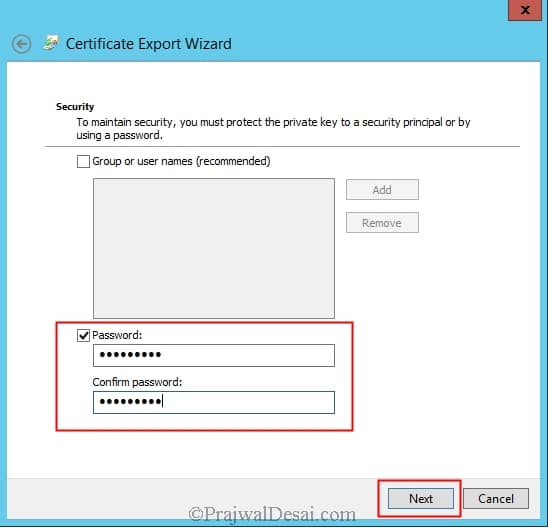
On the Password page, specify a strong password to protect the exported certificate with its private key, and then click Next.
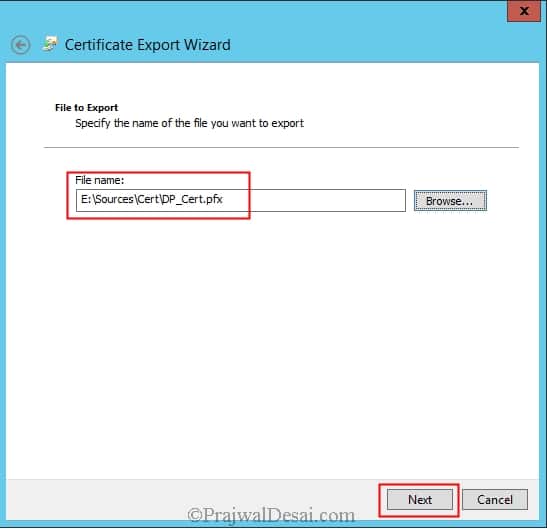
On the File to Export page, specify the name of the file that you want to export, and then click Next.
To close the wizard, click Finish in the Certificate Export Wizard page, and click OK in the confirmation dialog box. Close Certificates (Local Computer). The certificate is now ready to be imported when you configure the distribution point.
Deploying the Client Certificate for Distribution Points
Now that we have got the client certificate for distribution points, let’s assign them to the DP’s. Right click on the DP and under General tab, choose HTTPS and to import the certificate click on Browse. Import the certificate that you have exported in the above steps, provide the password and click OK.
For other roles, you may not be able to switch from HTTP to HTTPS as the options are greyed out. For example on Application catalog web service point, the options are greyed out. You have to uninstall both App catalog website point and App catalog web service point role and install the roles again.
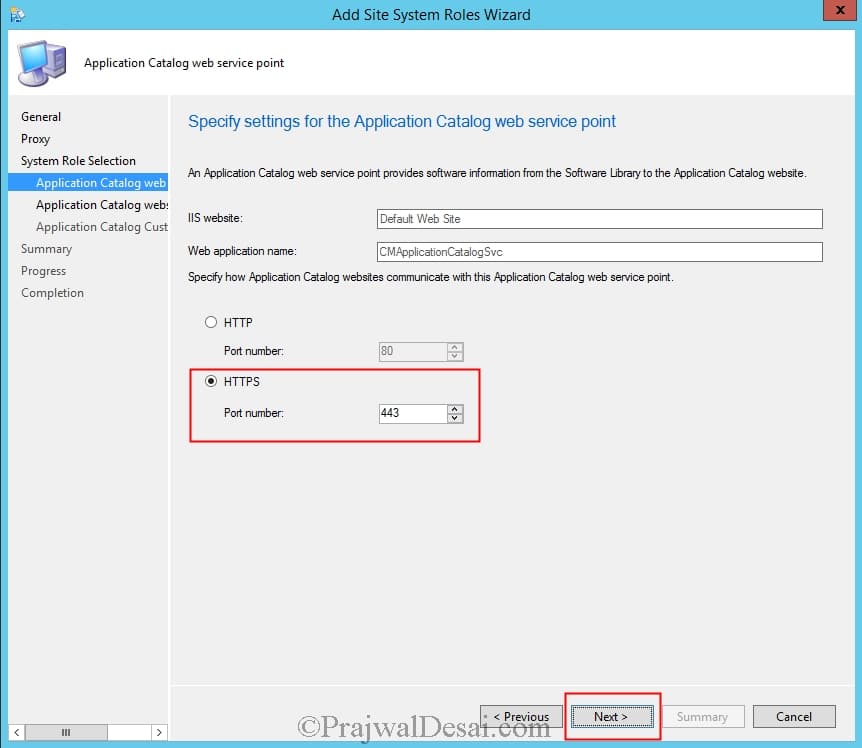
When you are reinstalling the App catalog web service point, you can now specify how App catalog website communicates with App catalog web service point. Choose HTTPS this time.
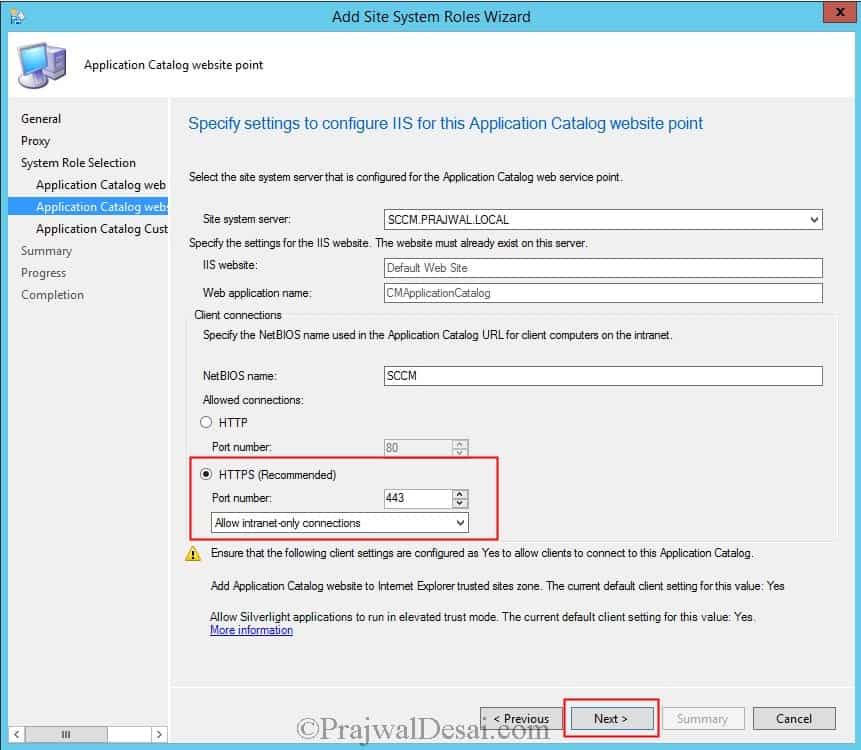
The same goes for App catalog website point. Choose HTTPS here. Click Next.
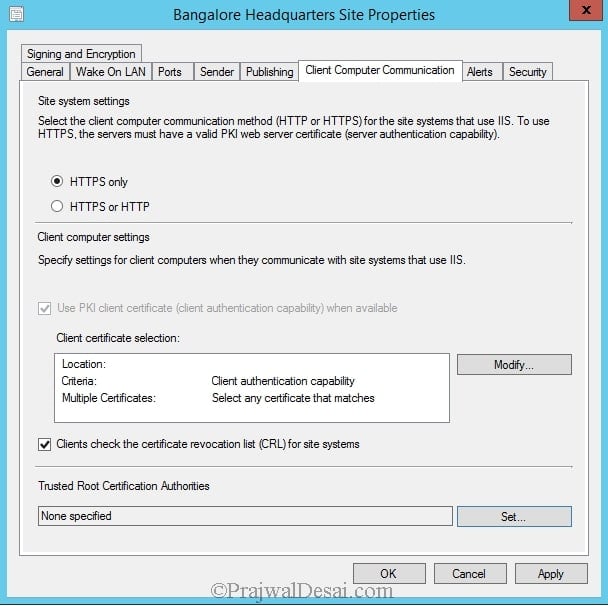
In the Configuration Manger console, navigate to Administration > Overview > Site Configuration > Sites. Right click on the site server and click Properties. Under site system settings, choose HTTPS only and click OK.
Login to one the computers which has Configuration Manager client installed. Look under General tab of configuration manager client properties. You will notice that Client Certificate is changed from self-signed to PKI.





Hi, can someone please help with this?
I followed instructions above here:
“For other roles, you may not be able to switch from HTTP to HTTPS as the options are greyed out. For example on Application catalog web service point, the options are greyed out. You have to uninstall both App catalog website point and App catalog web service point role and install the roles again.”
After i uninstalled the App Catalog Website point and App Catalog web service point role, i tried adding the roles again and it’s not showing up after waiting several hours and doing several restarts already. Why can’t I install the role back? I only have 1 SCCM server with all the roles on that 1 server.
Thanks
Hello,
Thanks for all you do!! When having to create new boot media, can i use the same cert that i used before if its not expired?
Hi Prajwal,
My security team has an issue creating an exportable certificate template.
If they provided me a certificate in pfx format with the password, would this work to import into the Distribution Point?
Of does the imported certificate have to be exportable?
Thanks
Finn
Hi Prajwal, I needa say thank you in advance, as your posts gave me many ideas and helped me to resolve many issues. Thanks!!
BTW, May I ask if my test lab don’t have Microsoft CA server (in real case, my company also don’t have it, that’s why I would like to simulate the case). Do you have idea how to handle this HTTPS issue if I don’t have CA server? Is it possible to use another application to generate cert, like OpenSSL. I really don’t have too much idea on it.
Thank you so much.
Hi
We have a single DP/SCCM server and Client Certificate for the DP was expired. We have renewed the certificate and installed as per the instruction.
We are still unable to pxe boot the Windows 10 image. Errors: 1. in SSL, but with no client cert. 2. Certificate not valid.. A required certificate is not within its validity period when verifying against the current system clock or the timestamp in the signed file. (Error: 800B0101; Source: Windows)
New Certificate is already listed in Administration>> Security >> Certificate and status is ‘Unblocked”
Do we need to update image .wim to include the new certificate? or Certificate will be automatically updated? Restarted the SMS_EXECUTIVE server but no avail.
PXE boot is complaining about the expired certificate.
Quick help will be appreciated.
same problem here with SCCM version 2203 did you solve it back then? 🙂
You need to redistribute the Boot image to the DP to get the Cert injected to the Boot image
What is about specify Trusted Root Certification Authorities in Site properties, it have to setup a cert or not? Is this the same imported certificate for Distribution Points??
Hi
I have clarification on DP certificate Renewal.
1. My DP certificate is going to expire in another 10 days. So what i have to do?
2. I can renew the same certificate or to create a New certificate and import it into DP Properties.
Please guide me how to perform this task.
Hi – Just one question – Do, I need new certificate for multiple DP’s? I have 2 DP. On the site server, I have created DP cert and assigned it to the DP. Now, I am installing one more DP. Can, I use the same DP cert that, I have on the site server or do, I need to create a new cert for the DP, I am deploying.
Thanks
Ram
You have to create a request a new cert for new DP and then export the certificate. You then assign this certificate under DP properties. I hope i answered your question.
I’m getting a .net error when I import the certificate foor DP…
System.FormatException: Index (zero based) must be greater than or equal to zero and less than the size of the argument list
Any Idea?