Simple Guide to Enable SCCM Enhanced HTTP Configuration
In this post I will show you how to enable SCCM enhanced HTTP configuration. We will also discuss what exactly is the enhance HTTP configuration in SCCM, how to enable it and about the enhanced HTTP certificates, SMS Role SSL Certificate.
Enhance HTTP configuration feature was first introduced in SCCM 1806 as a pre-release feature. However starting with SCCM 1810, this Enhanced HTTP feature is no longer a pre-release feature.
Recently I published a guide on SCCM 2103 Prerequisite Check Warning about enabling site system roles for HTTPS or Enhanced HTTP. Starting with SCCM 2103 you will require to select HTTPS communication or enhanced HTTP configuration. You must plan to configure the site for HTTPS only or to use Configuration Manager-generated certificates for HTTP site systems. If you don’t select between the two you may encounter a warning during the SCCM 2103 update installation.
Table of Contents
What is SCCM Enhanced HTTP Configuration ?
SCCM Enhanced HTTP secures sensitive client communication without the need for PKI server authentication certificates. When you enable SCCM enhanced HTTP configuration in ConfigMgr, the site server generates a certificate for the management point allowing it to communicate via a secure channel. Azure Active Directory (Azure AD)-joined devices and devices with a ConfigMgr issued token can communicate with a management point configured for HTTP if you enable SCCM enhanced HTTP.
What does Microsoft Recommends – HTTPS or Enhanced HTTP ?
Microsoft recommends using HTTPS communication for all Configuration Manager communication paths. However implementing PKI certificates for SCCM could be challenging for some customers due to the overhead of managing PKI certificates.
Is SCCM Enhanced HTTP Configuration Secure ?
Yes, the enhanced HTTP configuration is secure. When you enable Enhanced HTTP configuration in SCCM, you can secure sensitive client communication without the need for PKI server authentication certificates. Clients can securely access content from distribution points without the need for a network access account, client PKI certificate, and Windows authentication.
How to Enable SCCM Enhanced HTTP Configuration
The steps to enable SCCM enhanced HTTP are as follows.
- Launch the SCCM console.
- Navigate to Administration > Overview > Site Configuration > Sites.
- Select your primary site server. Right-click the Primary server and select Properties.
- In the Communication Security tab, under Site System setting, enable the option HTTPS or enhanced HTTP.
- Enable Use Configuration Manager-generated certificates for HTTP site systems.

NOTE
The procedure to enable enhanced HTTP Configuration in SCCM remains same for Central Administration Site as well. Use this same process, and open the properties of the central administration site. This action only enables enhanced HTTP for the SMS Provider roles at the central administration site. It’s not a global setting that applies to all sites in the hierarchy.
What happens when you enable SCCM Enhanced HTTP ?
When you enable SCCM enhanced HTTP configuration, the site server generates a self-signed certificate named SMS Role SSL Certificate. Here are the steps to access the SMS Role SSL Certificate.
- Login to the SCCM server.
- Click Start > Run and type the command certlm.msc.
- Under Certificates – Local computer, expand Personal > Certificates.
- That’s where you find the SMS Role SSL Certificate. This enhanced HTTP certificate is issued by the root SMS Issuing certificate.

Also the management point adds this certificate to the IIS default web site bound to port 443. On the Management Point server, access the IIS Manager. Right click Default Web Site and click Edit Bindings. Select HTTPS and click Edit. In the Edit Site Binding, ensure you see SMS Role SSL Certificate under SSL Certificate option.

Monitor Enhanced HTTP Configuration in MEMCM
After you enable enhanced HTTP configuration, to see the status of the configuration, review mpcontrol.log on your management point server. I found the following lines relevant to enhanced HTTP configuration.
Successfully performed Management Point availability check against local computer.
SSL is not enabled. SMS_MP_CONTROL_MANAGER
Using thread token for request SMS_MP_CONTROL_MANAGER
Call to HttpSendRequestSync succeeded for port 80 with status code 200, text: OK SMS_MP_CONTROL_MANAGER
Http test request succeeded. SMS_MP_CONTROL_MANAGER

SCCM Enhanced HTTP SMS Issuing Certificate
When you enable enhanced HTTP Configuration in SCCM, the SMS issuing certificate can also be found in ConfigMgr console. This is the self signed certificate created by Configuration Manager for enhanced HTTP feature.
- Launch the Configuration Manager console.
- Go to Administration\Overview\Security\Certificates.
- Look for SMS Issuing Certificate.
When you right click SMS Issuing certificate and click Properties, you may notice that certificate shows as untrusted as it is not placed in trusted root certification authorities store. To eliminate that error, click Install Certificate and ensure you place the SMS Issuing certificate in trusted root certification authorities store.

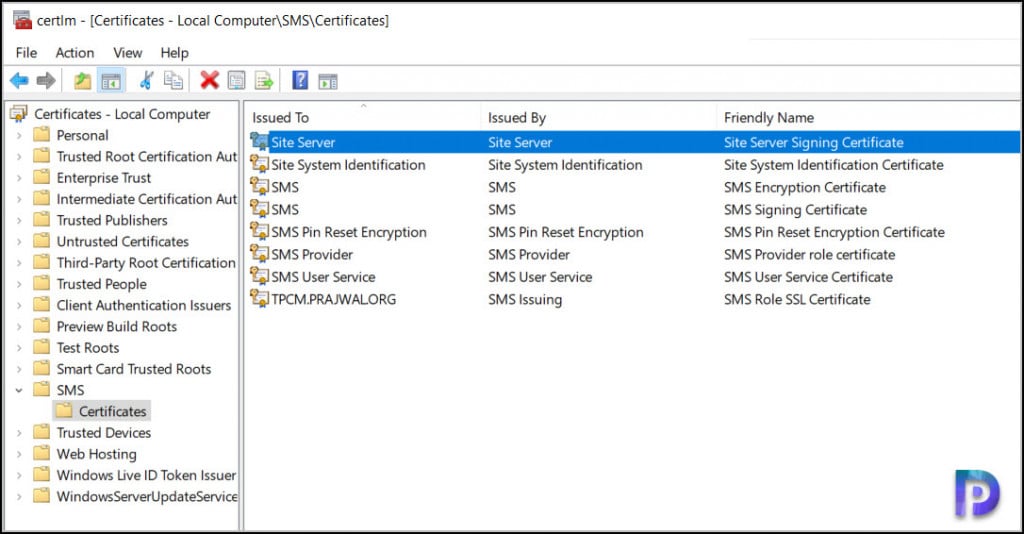
SCCM Enhanced HTTP Certificates on Server
The ConfigMgr Enhanced HTTP certificates on the server are located in the following path Certificates – Local computer > SMS > Certificates. Following are the SCCM Enhanced HTTP certificates that are created on server.
| Certificate Issued To | Certificate Issued By | Enhanced HTTP Certificate Friendly Name |
| Site Server | Site Server | Site Server Signing Certificate |
| Site System Identification | Site System Identification | Site System Identification Certificate |
| SMS | SMS | SMS Encryption Certificate |
| SMS | SMS | SMS Signing Certificate |
| SMS Pin Reset Encryption | SMS Pin Reset Encryption | SMS Pin Reset Encryption Certificate |
| SMS Provider | SMS Provider | SMS Provider role certificate |
| SMS User Service | SMS User Service | SMS User Service Certificate |
| ConfigMgr Server Name | SMS Issuing | SMS Role SSL Certificate |
SCCM Enhanced HTTP Certificates on Client Computers
Following are the SCCM Enhanced HTTP certificates that are created on client computers. The E-HTTP certificates are located in the following path Certificates – Local computer > SMS > Certificates.
| Certificate Issued To | Certificate Issued By | Enhanced HTTP Certificate Friendly Name |
| SMS | SMS | SMS Signing Certificate |
| SMS | SMS | SMS Encryption Certificate |

Configuration Manager Enhanced HTTP FAQ’s
Here are some of the common questions related to Configuration Manager Enhanced HTTP configuration.
What is SCCM Enhanced HTTP?
The SCCM Enhanced HTTP feature secures sensitive client communication without the need for PKI server authentication certificates in SCCM.
How do I enable SCCM Enhanced HTTP Configuration?
Navigate to Administration > Overview > Site Configuration > Sites. Right-click the Primary server and select Properties. In the Communication Security tab enable the option HTTPS or enhanced HTTP. Enable Use Configuration Manager-generated certificates for HTTP site systems.
How Secure is SCCM Enhanced HTTP Configuration?
Enhanced HTTP configuration is secure. When you enable Enhanced HTTP configuration in SCCM, you can secure sensitive client communication without the need for PKI server authentication certificates. Clients can securely access content from distribution points without the need for a network access account, client PKI certificate, and Windows authentication.
What is SMS Role SSL Certificate?
The SMS Role SSL Certificate enhanced HTTP certificate is issued by the root SMS Issuing certificate. When you enable SCCM enhanced HTTP configuration, the site server generates a self-signed certificate named SMS Role SSL Certificate.
Location of SCCM Enhanced HTTP Certificates?
The SCCM Enhanced HTTP certificates are located in the the following path – Certificates – Local computer > SMS > Certificates.
How can I see the status of Enhanced HTTP Configuration in SCCM?
To see the status of the Enhanced HTTP Configuration, review mpcontrol.log on the site server.

How does this work on a Win10 DP? Just set one up, clients PXE boot off the DP fine, then error with:
IP: 10.100.35.41 10.100.35.0 TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
CLibSMSMessageWinHttpTransport::Send: WinHttpOpenRequest – URL: <>:80 GET /SMS_MP/.sms_aut?MPLOCATION&ir=10.100.35.41&ip=10.100.35.0 TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
Not in SSL. TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
Request was successful. TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
pwsSig != NULL, HRESULT=80004005 (K:\dbs\sh\cmgm\1125_114522\cmd\6\src\Framework\OSDMessaging\libsmsmessaging.cpp,6405) TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
Invalid MP cert info; no signature. Make sure the certificates are correctly configured in MP’s registry TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
CCM::SMSMessaging::CLibSMSMPLocation::RequestMPLocation failed; 0x80004005 TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
MPLocation.RequestMPLocation (szTrustedRootKey, sIPSubnets.c_str(), sIPAddresses.c_str(), httpS, http), HRESULT=80004005 (K:\dbs\sh\cmgm\1125_114522\cmd\6\src\Framework\OSDMessaging\libsmsmessaging.cpp,10821) TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
CCM::SMSMessaging::GetMPLocations failed; 0x80004005 TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
Failed to query <> for MP location TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
MpCnt > 0, HRESULT=80004005 (K:\dbs\sh\cmgm\1125_114522\cmd\k\src\client\TaskSequence\TSMBootstrap\tsmbootstraputil.cpp,2038) TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
QueryMPLocator: no valid MP locations are received TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
TSMBootstrapUtil::QueryMPLocator ( true, sSMSTSLocationMPs.c_str(), sMediaPfx.c_str(), sMediaGuid.c_str(), sAuthenticator.c_str(), sEnterpriseCert.c_str(), sServerCerts.c_str(), nHttpPort, nHttpsPort, bUseCRL, m_bWinPE, httpS, http, accessibleMpCnt), HRESULT=80004005 (K:\dbs\sh\cmgm\1125_114522\cmd\k\src\client\TaskSequence\TSMBootstrap\tsmediawizardcontrol.cpp,1054) TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
Failed to query Management Point locator TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
Exiting TSMediaWizardControl::GetPolicy. TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
pWelcomePage->m_pTSMediaWizardControl->GetPolicy(), HRESULT=80004005 (K:\dbs\sh\cmgm\1125_114522\cmd\k\src\client\TaskSequence\TSMBootstrap\tsmediawelcomepage.cpp,304) TSMBootstrap 08/11/2023 09:22:29 1856 (0x0740)
Setting wizard error: An error occurred while retrieving policy for this computer (0x80004005). For more information, contact your system administrator or helpdesk operator. TSMBootstrap 08/11/2023 09:22:29 1676 (0x068C)
WelcomePage::OnWizardNext() TSMBootstrap 08/11/2023 09:22:29 1676 (0x068C)
Tries each MP with the same errors
Can we use http and https both at the same time?
There was no mention of the Distribution Points.
Prajwal do you have a document to upgrade SCCM from HTTP to HTTPS (PKi certificates)
I want to use only port 443 for client communication on Enhanced HTTP mode, can someone confirm if this is possible ?
Is it possible to replace the SMS Issuing self-signed certificate with a trusted one from a CA?
Vulnerability scans from Nessus flag the SMS Issuing self-signed as untrusted and a vulnerability.
we have the same issue.
For Clients, I’m wondering if option “Use PKI client certificate (client authentication capability) when available” would fix this at least for the Clients.
My certificates are successfully renewed months ago but i noticed there are a lot of expired certificates on my servers some times more then one with the same name. But they are not automatically cleaned up. Is it safe to delete the expired ones from the certificate store?
Yes, you can delete them. Shouldn’t cause any issues.
SMS Role SSL Certificate is not getting populated in IIS Server certificates and system “Personal” Certificates, even after selecting ehttp. Tried multiple times.
Its supposed to be automatically populated, but its not showing up. There is a “SMS token signing certificate” and “WMSVC” certificate. But not SMS Role SSL Certificate. Can you help ?
Thanks a lot. It was perfect.
The certificate is always installed in default web site?. If you have de custom website SMSWEB the certificate is always installed in the default web site by the MP. Is posible to change it.
Hi,
I am also interested in how the certificate gets deployed / installed on the client after enhanced http has been set up in configuration Manager
Setting this up can be quite annoying if you already have server authentication certificates in the personal store issued to your site server. Looks like someone previously tried to setup https communication in our environment and left old authentication certs in the personal store and config manager refused to add the sms role ssl cert due to this and when i attempted to install the cert to the personal store from config manager, it does not install the cert with the private key since it is not marked as exportable, so then i could not use it for binding in iis because it would not show as available. Had to remove remove ehttp delete all these other certs remove the iis binding and re-enable ehttp.
Hi – After moving to enhanced HTTP on SCCM v2107, has anyone noticed any errors on clients like this “Key ‘ConfigMgrMigrationKey’ not found, 0x80090016” in client PCs CertificateMaintenance.log? Everything seems to be working fine but all clients have this error.
Hey there Prajwal:
Nice article, but I do not see one thing. How do you get the Self Signed certificate that the server creates to the client machines? Does it get deployed, or do you have to do that through group policy, or is it something else entirely?
Hello all
I have the same question as Kacey. Would be really interesting to know how the SMS Issuing cert gets installed on the client.
Kind regards
Matias
Hi,
I am also interested in how the certificate gets deployed / installed on the client.
did you ever found out? I am planning to do this, but want to make sure i have all bases covered.
Appears the certs just deploy via SCCM. Turned it on for testing and everything rolled out to end clients and things were working. No issues. Leaving it on.
But it is a self signed cert deployed to clents? wont workstations complain of its validity ?