How to Configure Multiple Admin Approvals In Intune
In this post, you’ll learn how to configure multiple admin approvals in Intune. You can use the access policies to require multiple administrative approvals (MAAs) over Intune resources.
We will go through the process step-by-step to understand what multiple admin approvals in Intune are, who can create and approve MAA policies in Intune, and how to create an access policy, submit a request, and get an approval.
Multiple Admin Approvals is a new feature introduced in the Microsoft Intune November (2211) service release. With MAA, you can set up access policies that protect specific settings, like apps or scripts for devices. This feature is currently in public preview. You can test out this new feature in your Intune tenant and provide feedback to Microsoft. The general availability of this feature will be announced by Microsoft soon.
If you are using Configuration Manager, you can approve application requests for users and approve SCCM application requests via email. Multiple admin approvals in Intune are more advanced and offer way more features.
What is Multiple Administrative Approval (MAA)?
To help protect against a compromised administrative account, use Intune access policies to require that a second administrative account is used to approve a change before the change is applied. This capability is known as multiple administrative approval (MAA).
With MAA, you can set up access policies to protect certain settings on a device, like apps or scripts. What is protected and which group of accounts is allowed to approve modifications to those resources are both specified by access policies.
When an access policy-protected resource is changed by any account in the Tenant, Intune won’t make the change effective until a different account explicitly approves it. Changes can only be approved by administrators who are a part of an approval group that has been given a protected resource by an access protection policy. Change requests may also be rejected by approvers.
Currently, the access policies in Intune are supported only for the following resources:
- Apps: Applies to app deployments, but doesn’t apply to app protection policies.
- Scripts: Applies to deploying scripts to devices that run macOS or Windows.
Who can Create and Approve Requests?
To create an MAA access policy, the account must be assigned the Intune Service Administrator or Azure Global Administrator role. Only these two roles have the permissions to create MAA policies in Intune.
To approve MAA policies, an account must be in the group that’s assigned to the access policy for a specific type of resource. Ensure the user is part of the group that can approve requests before you test the admin approvals in Intune.
How to Configure Multiple Admin Approvals In Intune
We will now go through the steps to configure multiple admin approvals in Intune. There are many steps involved in getting Multiple Administrative Approvals to work. We will go through each step and understand how to configure the admin approvals in Intune.
Step 1: Create Access Policy for MAA in Intune
Perform the following steps to create an access policy for multiple administrative approvals in Intune:
- Launch the browser and sign-in to the Intune Portal.
- Go to Tenant administration > Multi Admin Administration > Access policies and select Create.

On the Basics page, provide a Name, and optional Description. For the Profile type, there are two options available: Apps and Scripts. Select Apps from the available options. Each policy supports a single profile type. Click Next.

On the Approvers page, select Add groups and then select a group as the group of approvers for this policy. More complex configurations that exclude groups aren’t supported. Click Next.
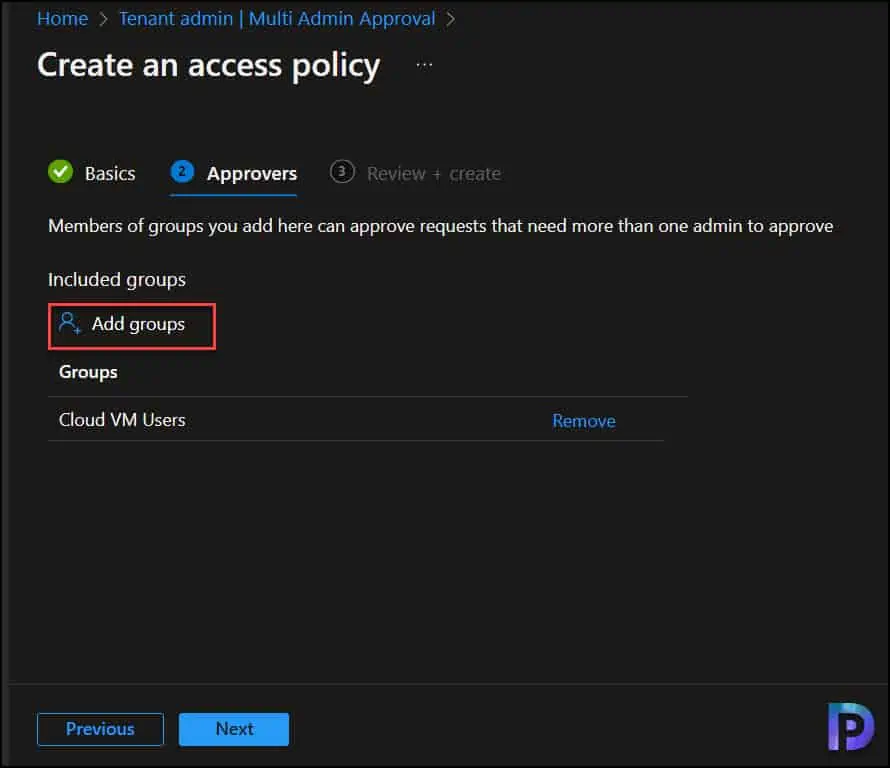
On the Review + Create page, review the access policy, and then save your changes. After this policy is applied by Intune, configurations for the protected profile type will need approval from more than one admin.

A message stating that multiple admin approvals were successfully created can be seen in the console’s upper-right corner. All the access policies that you have created will appear under the Tenant Admin > Multiple Admin Approval blade of the Intune console.

Step 2: Submit a Request
After the access policy for MAA has been created, it gets into action immediately. When an admin edits or creates a new object for an area that’s protected by an access policy, they see an option on the Save + Review surface where they can enter a description of the change as a business justification.
When the apps are protected by an access policy, any changes introduced to the existing apps or add new apps will require business justification. The requester can add additional notes as to what changes were made and why. Only after adding the business justification, the approver can approve the request or reject it.
To test this, you can either add a new app into Intune or edit any existing apps and make some changes. For example, you may modify the application description, add/remove the assignments, etc. After you’ve finished making changes to the app, click Review and Save.

The requester now sees the following message “Before this resource can be updated, it must be approved by another admin. Before you can submit this request, you must enter your business justification.“
Before you can save your changes on the last page, fill out the Business justification field with information before submitting the request. After you’ve finished adding the business justification, click Save.

Note: When there’s a request for the same object that is already pending approval, you won’t be able to submit your request. Intune displays a message to alert you to this situation.
The admin who submitted the request now sees a notification in the Intune console “Change request submitted” confirming that the request for approval is submitted.

Step 3: Approve Requests
The request needs to be approved after the admin has submitted it. Here are the steps that you need to follow to find requests to approve:
In the Intune admin center, go to Tenant administration > Multi Admin Administration > Received Requests. Select the Business justification link for a request to open the review page, where you can learn more about the request, and manage approval or rejection.

After reviewing the details, enter relevant details in the Approver Notes field, and then select Approve request or Reject request. An example of what a multi admin approval request would look like. The example illustrates that the change requested is to update information about the Windows App. The changes are highlighted, and the admin has the ability to approve or reject the request, and add approver notes.

After you approve a request, Intune processes the change and updates the status to Completed after it’s successfully applied. The request status might change to Approved for a limited time if the update to the resource takes time to process.

Step 4: Monitor the Status of your Requests
An admin who has submitted a change request can view the status of their requests in the Microsoft Endpoint Manager admin center by going to Tenant administration > Multi Admin Approval and viewing the “My requests” page.
Few important things to note here:
- You can cancel a request before it’s approved by selecting it from the “My Requests” page, and then selecting Cancel request.
- When an approval is already pending for an object, a new request is can’t be submitted for it.
- Actions for requests and the approval process are logged in the Intune audit logs.

Intune Multiple Administrator Approval Statuses
The table lists all the status conditions that are available for a request submitted by admins.
| Multiple Administrator Approval Status | Description |
|---|---|
| Needs approval | This request is pending action by an approver. |
| Approved | This request is being processed by Intune. |
| Completed | This request has been successfully applied. |
| Rejected | This request was rejected by an approver. |
| Cancelled | This request was canceled by the admin who submitted it. |
| Expired | The request has been expired. |
In the picture below, you can see how an admin who is also an approver sees the different statuses.

Conclusion
Intune’s Multiple Administrator Approval is a fantastic feature. Given the importance of protecting the policies, this could be a great addition to your change processes to expedite policy operations. This is a good start, and I believe the same feature will be added to Security Policies, Device Configuration Profiles, App Configuration Profiles, and App Protection Profiles once it is ready for general availability.

Any word on if/when they will extend this to compliance and config policies? Having it for apps and scripts is great but those other settings are just as critical IMO.