Secure Windows Systems against Meltdown Spectre CPU Flaws
This week of mine has been very busy in understanding about Meltdown and Spectre vulnerabilities. You should know that Meltdown and Spectre unleash critical vulnerabilities in modern processors. In fact the researchers have recorded all the information about these vulnerabilities here. If you really need to understand what’s Meltdown and Spectre, visit that link. That link helped me a lot in understanding about the vulnerabilities. This post contains the information on how to secure windows systems against meltdown spectre CPU flaws.
What is Meltdown and Spectre ?.
Meltdown and Spectre vulnerabilities affect modern computers leak passwords and sensitive data from them. Meltdown breaks isolation between user apps and the OS. Spectre breaks the isolation between different applications. Meltdown is more easy to patch as we have patches available but Spectre is harder to figure out and patch.
So if your question is should i care about this thing ?. Probably Yes, because these are CPU flaws and there is a high chance that your system could be exploited. Most of all you cannot find whether these exploits have been run against your computer. This is because the exploits do not leave any traces in log files. When you understand how critical this is, every organization must secure windows systems against Meltdown Spectre CPU Flaws. I also want to add that these vulnerabilities affect your PC’s, mobile devices, and machines in the cloud.
Where can I find more information about patching Meltdown and Spectre
Here are some of the links that should help you. These vulnerabilities are also referred as speculative execution side-channel attacks.
- Windows Client OS- Link.
- Windows Server OS – Link.
- Security Advisory from Microsoft – Link.
- AV Compatibility Issues – Link.
- SQL Server Guidance – Link.
How to Secure Windows Systems against Meltdown Spectre CPU Flaws
Before you plan to secure windows systems against Meltdown and Spectre CPU flaws, I would like highlight few things.
- Antivirus – Microsoft has reported compatibility issues with few antivirus software products. MS is working with AV providers to get this fixed via a security update. More info is here. Antivirus is something that you should consider before installing any of the patches. I recommend you to check with your AV provider to see if they have any updates on it.
- Processors – So far the patches released by Microsoft works well systems with Intel processors. Seems like the same is not the case with AMD processors. Microsoft has pulled off Meltdown and Spectre security updates for some older AMD machines. These updates have bricked AMD machines and led to PCs not booting. AMD is aware of this issue and from either of them the updates should come soon.
- Applications – When you plan to deploy these patches across your organization, ensure your business apps work fine post patch installation. You must test the working of apps before you roll out the patches. For example I rolled out KB4056891 to some of machines in my organization. The very next hour i received emails where users were unable to connect to VPN using pulse secure client. After research i found latest version of Pulse Secure was released to address this issue. In your case it could be other apps, so have a thorough testing first.
If you are prepared to roll out the patches to your organization, the easiest way is to check for Windows Updates. Most of the required patches should be downloaded through windows updates. However you could visit Microsoft Update Catalog site and search for KB number and download the patch. You could then use SCCM or other tools to push these updates to computers.
Checking the Status of patches
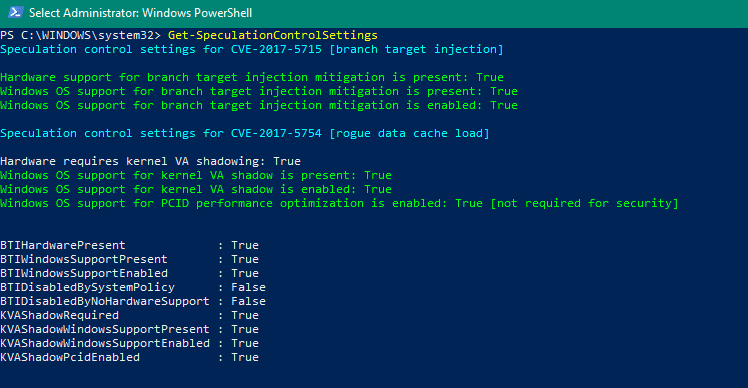
I will show you some steps that will help you to check status of these patches. To verify that protections are enabled, Microsoft has published a PowerShell script. With this script we will determine how safe is our computer against these vulnerabilities.
Run the PowerShell as administrator and run the below command. This command installs speculation control module.
Install-Module SpeculationControl
Type Y to proceed with install.
 Once the module is installed, type the below command. This command checks your systems and shows the speculation control results.
Once the module is installed, type the below command. This command checks your systems and shows the speculation control results.
Get-SpeculationControlSettings
You shouldn’t worry about the lines that are green. Those are the ones fixed by patches installed via Windows Update. So I suggest you to perform windows update once. The red lines are the ones that needs attention. These are not fixed by installing any software updates.
If you look closely, the red ones can be fixed by contacting your device manufacturer. While not all device manufacturers have the updates ready, but the updates should be released soon.  In my case I went to Dell support site and checked for latest BIOS updates. Yes there was one available. So i downloaded it, upgraded my BIOS and rebooted the laptop. Ran the speculation settings and it was all patched. I am now working on upgrading BIOS on other laptops using SCCM across organization.
In my case I went to Dell support site and checked for latest BIOS updates. Yes there was one available. So i downloaded it, upgraded my BIOS and rebooted the laptop. Ran the speculation settings and it was all patched. I am now working on upgrading BIOS on other laptops using SCCM across organization.

Hi
I can’t wait till your write up on the bios update I cannot get it to work
Hi
Can’t wait for your write up on bios update using sccm I’m having all sorts of issues
Thanks PrajwaI believe bios update or firmware update is not we do generally. There are many reasons behind it, it breaks drive encryption, also breaks security products either ms or other such as device guard, credentials guard.. Specifically challenges with Access protection. Not sure sccm will be interactive during upgrade for enterprise environment.. For machines which are going to be build newly we can do bios update then we can install bios updates and then os install. For existing systems access protection and other security controls should be turned off before update. Share your experience past how you achieved bios updates for enterprise.
Thanks Prajwal for your great post.very much appreciated.
Can you please help or share the steps to upgrade bios through SCCM.
Hi Rajneesh, I am still working on it. Upgrading BIOS through SCCM seems to be challenging specially when you have bitlocker enabled, it requires suspending it, updating the BIOS and then enabling it back.